You only need to anonymise public IPs. Anonymising private IPs only complicates troubleshooting.
Ok, so the update was done.
I obviously checked the relevant files after that. This is what I did:
- In /etc/config/firewall I discovered an incorrect LAN IP which I corrected.
- In /etc/config/firewall added the second forwarding rule for bi-directional traffic (so added wan to lan).
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'wan'
option dest 'lan'
Changed zone and default rule as highlighted:
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward '**ACCEPT**'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward '**ACCEPT**'
Finished with
/etc/init.d/firewall reload and discovered it also works with service firewall restart
Both options return the complaint (not really an error I would say...)
Section @redirect[0] (Dev-1) does not specify a destination, assuming 'lan'
Section @redirect[1] (Dev-2) does not specify a destination, assuming 'lan'
Section @redirect[2] (Dev-3) does not specify a destination, assuming 'lan'
This I believe may be the consequence of removing the optional entry
config redirect
option dest 'lan'
Right now it is still not worwarding but I'll give it some time and maybe another reboot...
Is the wan network connected directly to the internet? If so then you need to get rid of:
The WAN goes through an ISP router which is set to "bridge mode".
But if I connect e.g. an IP cam or a NAS I do need both directions I would think as traffic surely goes both ways then, doesn't it?
In that case,
That is absolutely critical for security. What you are saying is that the wan should have access to the lan. You do not want that.
But if I connect e.g. an IP cam or a NAS I do need both directions I would think as traffic surely goes both ways then, doesn't it?
Any time a lan device establishes a connection out via the wan, the related traffic is allowed back in automatically. You do not need to set special allowances.
That may have confused me a bit now:
If I access a NAS or an IP cam I establish a connection from outside to the local network, so wan to lan via the forwarded ports, correct?
The device then responds and returns the request and traffic might go both ways during the established connection. That's why I assumed, I need to set 'config forwarding' both ways.
Did I understand this incorrectly?
Did I understand this incorrectly?
Yes, you have an incorrect understanding.
I'll try to explain a bit differently....
The forward rule determines which zone is allowed to initiate a connection to the other. Normally, you only want lan > wan forwarding to allow your local devices to reach the internet. If you want to open specific ports such that you can reach a device from the internet, you do this in a more specific and granular way via port forwarding. A port forward rule includes the destination port from the source (i.e. what port is the initiator trying to reach), a destination port at the actual destination (i.e. what port is the server listening on), and the IP address on your lan of the server host.
You do not want to allow blanket forwarding from the wan (internet) to your lan, as that would present a massive security vulnerability.
Hmm, thanks for that.
Now this is eactly what I am trying to set up:
I want specific devices accessible from the internet, so wan -> lan access with specific open ports and everything else should be closed.
And if I understand this correctly, 'config forwarding' sets a global rule and 'config redirect' will override the global rule (which would disallow forwarding in general) for specific LAN IPs and their specific open ports- correct?
This is in fact how I did that before a major update prior to this last one. And that worked fine- until that update came.
And here's my update:
I can access one device remotely (I get a PW promt), the other two won't respond.
Below is the /etc/config/firewall again fyi:
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
# config forwarding
option src 'wan'
option dest 'lan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option name 'Dev-0'
option src 'wan'
option src_dport '120'
option dest_port '120'
option dest_ip '192.168.2.170'
option proto 'tcp udp'
config redirect
option target 'DNAT'
option name 'Dev-1'
option src 'wan'
option src_dport '121'
option dest_port '121'
option dest_ip '192.168.2.171'
option proto 'tcp udp'
config redirect
option target 'DNAT'
option name 'Dev-2'
option src 'wan'
option src_dport '122'
option dest_port '122'
option dest_ip '192.168.2.172'
option proto 'tcp udp'
Delete this entirely:
# config forwarding option src 'wan' option dest 'lan'
All three of the redirect rules below are missing a single line:
option dest 'lan'
config redirect option target 'DNAT' option name 'Dev-0' option src 'wan' option src_dport '120' option dest_port '120' option dest_ip '192.168.2.170' option proto 'tcp udp' config redirect option target 'DNAT' option name 'Dev-1' option src 'wan' option src_dport '121' option dest_port '121' option dest_ip '192.168.2.171' option proto 'tcp udp' config redirect option target 'DNAT' option name 'Dev-2' option src 'wan' option src_dport '122' option dest_port '122' option dest_ip '192.168.2.172' option proto 'tcp udp'
Finally, make sure that the hosts at 192.168.2.170, .171, and .172 are listening on the respective ports (120, 121, 122). You can test this from inside your network. If they are not listening, the port forward won't do anything.
I'm back again.... next chapter of this:
Added the destinations and yes hosts are listening. I can access all three from inside ther lan.
So I compared /etc/config/firewall with a previous (pre-update) backup I found where the forwarding was working well.
There are a few (syntax only?) differences:
Current file:
config zone
option name 'wan'
**list network 'wan'**
** list network 'wan6'**
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
Old file:
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
**option network 'wan6 wan'**
option forward 'REJECT'
option input 'REJECT'
Only the current file knows the below rules:
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
But this rule below is only included in the old file and does not occur in the recent one.
config include
option path '/etc/firewall.user'
If I add it, it returns
Section @include[0] is not marked as compatible with fw4, ignoring section
Section @include[0] requires 'option fw4_compatible 1' to be considered compatible
Should I include the suggested 'option fw4_compatible 1' from the config that actually worked?
I understand that with 'config include' the software expects a custom firewall file which however doesn't exist (and never did previously) in that location at all.
Last question: Just like to confirm that one can comment in /etc/config/firewall.
What seems to be the general defaults under /rom/etc/config/firewall contains a lot of commented lines. So I assume it's ok, but don't want to log myself out unnecessarily (or open the device up to the bots...).
option path '/etc/firewall.user'
Is there anything in this file? Or does it even exist? If it doesn't exist, you can simply delete the line above.
No, there is no option path.
Since this isn't going anywhere I am considering two ways forward, one I have already tried:
- Go back to a previous release for this device (since it used to work before the last update!). Not done that yet, but it's on the list.
- Use a VPN tunnel to get to LAN devices.
So I set up a WireGuard server on the router as well as client devices (iPad and Android phone). Went through some tutorials plus the official guide pages here
However, I can only see TX data on "WireGuardStatus", no RX. Similar picture on the devices.
This seems to confirm that the firewall is the issue, as it also uses port forwarding. And WireGuard is communicating both ways if the clients are within the LAN, once out, it won't work anymore.
Not sure if I should continue the WireGuard idea in this thread as it might go off topic.
Also need to do some analysis as suggested on the guide pages here...
What's the output of nft list ruleset?
Well, without having had the time to study what the output is, please find it below.
Should also nmention that I did a reset and new install before, so previous IPs and ports are different. Hope that doesn't cause confusion.
table inet fw4 {
chain input {
type filter hook input priority filter; policy drop;
iifname "lo" accept comment "!fw4: Accept traffic from loopback"
ct state established,related accept comment "!fw4: Allow inbound established and related flows"
tcp flags syn / fin,syn,rst,ack jump syn_flood comment "!fw4: Rate limit TCP syn packets"
iifname { "WGuard", "br-lan" } jump input_lan comment "!fw4: Handle lan IPv4/IPv6 input traffic"
iifname "wan" jump input_WAN comment "!fw4: Handle WAN IPv4/IPv6 input traffic"
jump handle_reject
}
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname { "WGuard", "br-lan" } jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname "wan" jump forward_WAN comment "!fw4: Handle WAN IPv4/IPv6 forward traffic"
jump handle_reject
}
chain output {
type filter hook output priority filter; policy accept;
oifname "lo" accept comment "!fw4: Accept traffic towards loopback"
ct state established,related accept comment "!fw4: Allow outbound established and related flows"
oifname { "WGuard", "br-lan" } jump output_lan comment "!fw4: Handle lan IPv4/IPv6 output traffic"
oifname "wan" jump output_WAN comment "!fw4: Handle WAN IPv4/IPv6 output traffic"
}
chain prerouting {
type filter hook prerouting priority filter; policy accept;
iifname { "WGuard", "br-lan" } jump helper_lan comment "!fw4: Handle lan IPv4/IPv6 helper assignment"
}
chain handle_reject {
meta l4proto tcp reject with tcp reset comment "!fw4: Reject TCP traffic"
reject comment "!fw4: Reject any other traffic"
}
chain syn_flood {
limit rate 25/second burst 50 packets return comment "!fw4: Accept SYN packets below rate-limit"
drop comment "!fw4: Drop excess packets"
}
chain input_lan {
ct status dnat accept comment "!fw4: Accept port redirections"
jump accept_from_lan
}
chain output_lan {
jump accept_to_lan
}
chain forward_lan {
jump accept_to_WAN comment "!fw4: Accept lan to WAN forwarding"
ct status dnat accept comment "!fw4: Accept port forwards"
jump accept_to_lan
}
chain helper_lan {
}
chain accept_from_lan {
iifname { "WGuard", "br-lan" } counter packets 11742 bytes 978421 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain accept_to_lan {
oifname { "WGuard", "br-lan" } counter packets 2395 bytes 214798 accept comment "!fw4: accept lan IPv4/IPv6 traffic"
}
chain input_WAN {
meta nfproto ipv4 udp dport 68 counter packets 0 bytes 0 accept comment "!fw4: Allow-DHCP-Renew"
icmp type echo-request counter packets 0 bytes 0 accept comment "!fw4: Allow-Ping"
meta nfproto ipv4 meta l4proto igmp counter packets 704 bytes 22528 accept comment "!fw4: Allow-IGMP"
meta nfproto ipv6 udp dport 546 counter packets 1 bytes 181 accept comment "!fw4: Allow-DHCPv6"
ip6 saddr fe80::/10 icmpv6 type . icmpv6 code { mld-listener-query . no-route, mld-listener-report . no-route, mld-listener-done . no-route, mld2-listener-report . no-route } counter packets 0 bytes 0 accept comment "!fw4: Allow-MLD"
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply, nd-router-solicit, nd-router-advert } limit rate 1000/second counter packets 342 bytes 51984 accept comment "!fw4: Allow-ICMPv6-Input"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, nd-neighbor-solicit . no-route, nd-neighbor-advert . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 6643 bytes 459064 accept comment "!fw4: Allow-ICMPv6-Input"
ct status dnat accept comment "!fw4: Accept port redirections"
jump reject_from_WAN
}
chain output_WAN {
jump accept_to_WAN
}
chain forward_WAN {
icmpv6 type { destination-unreachable, time-exceeded, echo-request, echo-reply } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
icmpv6 type . icmpv6 code { packet-too-big . no-route, parameter-problem . no-route, parameter-problem . admin-prohibited } limit rate 1000/second counter packets 0 bytes 0 accept comment "!fw4: Allow-ICMPv6-Forward"
meta l4proto esp counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-IPSec-ESP"
udp dport 500 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-ISAKMP"
udp dport 115 counter packets 0 bytes 0 jump accept_to_lan comment "!fw4: Allow-WG-Input"
ct status dnat accept comment "!fw4: Accept port forwards"
jump reject_to_WAN
}
chain accept_to_WAN {
meta nfproto ipv4 oifname "wan" ct state invalid counter packets 150 bytes 10493 drop comment "!fw4: Prevent NAT leakage"
oifname "wan" counter packets 25907 bytes 4958000 accept comment "!fw4: accept WAN IPv4/IPv6 traffic"
}
chain reject_from_WAN {
iifname "wan" counter packets 453 bytes 29009 jump handle_reject comment "!fw4: reject WAN IPv4/IPv6 traffic"
}
chain reject_to_WAN {
oifname "wan" counter packets 0 bytes 0 jump handle_reject comment "!fw4: reject WAN IPv4/IPv6 traffic"
}
chain dstnat {
type nat hook prerouting priority dstnat; policy accept;
iifname { "WGuard", "br-lan" } jump dstnat_lan comment "!fw4: Handle lan IPv4/IPv6 dstnat traffic"
iifname "wan" jump dstnat_WAN comment "!fw4: Handle WAN IPv4/IPv6 dstnat traffic"
}
chain srcnat {
type nat hook postrouting priority srcnat; policy accept;
oifname { "WGuard", "br-lan" } jump srcnat_lan comment "!fw4: Handle lan IPv4/IPv6 srcnat traffic"
oifname "wan" jump srcnat_WAN comment "!fw4: Handle WAN IPv4/IPv6 srcnat traffic"
}
chain dstnat_lan {
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 tcp dport 110 dnat ip to 192.168.0.42:110 comment "!fw4: Dev-0 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 udp dport 110 dnat ip to 192.168.0.42:110 comment "!fw4: Dev-0 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 tcp dport 111 dnat ip to 192.168.0.111:111 comment "!fw4: Dev-1 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 udp dport 111 dnat ip to 192.168.0.111:111 comment "!fw4: Dev-1 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 tcp dport 112 dnat ip to 192.168.0.112:112 comment "!fw4: Dev-2 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 udp dport 112 dnat ip to 192.168.0.112:112 comment "!fw4: Dev-2 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 udp dport 115 dnat ip to 192.168.0.2:115 comment "!fw4: WGuard (reflection)"
}
chain srcnat_lan {
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.42 tcp dport 110 snat ip to 192.168.0.2 comment "!fw4: Dev-0 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.42 udp dport 110 snat ip to 192.168.0.2 comment "!fw4: Dev-0 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.111 tcp dport 111 snat ip to 192.168.0.2 comment "!fw4: Dev-1 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.111 udp dport 111 snat ip to 192.168.0.2 comment "!fw4: Dev-1 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.112 tcp dport 112 snat ip to 192.168.0.2 comment "!fw4: Dev-2 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.112 udp dport 112 snat ip to 192.168.0.2 comment "!fw4: Dev-2 (reflection)"
ip saddr { 192.168.0.0/24, 192.168.13.0/24 } ip daddr 192.168.0.2 udp dport 115 snat ip to 192.168.0.2 comment "!fw4: WGuard (reflection)"
}
chain dstnat_WAN {
meta nfproto ipv4 tcp dport 110 counter packets 0 bytes 0 dnat ip to 192.168.0.42:110 comment "!fw4: Dev-0"
meta nfproto ipv4 udp dport 110 counter packets 0 bytes 0 dnat ip to 192.168.0.42:110 comment "!fw4: Dev-0"
meta nfproto ipv4 tcp dport 111 counter packets 0 bytes 0 dnat ip to 192.168.0.111:111 comment "!fw4: Dev-1"
meta nfproto ipv4 udp dport 111 counter packets 0 bytes 0 dnat ip to 192.168.0.111:111 comment "!fw4: Dev-1"
meta nfproto ipv4 tcp dport 112 counter packets 0 bytes 0 dnat ip to 192.168.0.112:112 comment "!fw4: Dev-2"
meta nfproto ipv4 udp dport 112 counter packets 0 bytes 0 dnat ip to 192.168.0.112:112 comment "!fw4: Dev-2"
meta nfproto ipv4 udp dport 115 counter packets 0 bytes 0 dnat ip to 192.168.0.2:115 comment "!fw4: WGuard"
}
chain srcnat_WAN {
meta nfproto ipv4 masquerade comment "!fw4: Masquerade IPv4 WAN traffic"
}
chain raw_prerouting {
type filter hook prerouting priority raw; policy accept;
}
chain raw_output {
type filter hook output priority raw; policy accept;
}
chain mangle_prerouting {
type filter hook prerouting priority mangle; policy accept;
}
chain mangle_postrouting {
type filter hook postrouting priority mangle; policy accept;
}
chain mangle_input {
type filter hook input priority mangle; policy accept;
}
chain mangle_output {
type route hook output priority mangle; policy accept;
}
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
iifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone WAN IPv4/IPv6 ingress MTU fixing"
oifname "wan" tcp flags syn tcp option maxseg size set rt mtu comment "!fw4: Zone WAN IPv4/IPv6 egress MTU fixing"
}
}
reset and new install before, so previous IPs and ports are different
Ok, so what's the current content of /etc/config/network and /etc/config/firewall?
Sorry, should have added it straight away...
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc9:813d:8a94::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.0.2'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'wan'
option macaddr 'MACanonymised'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'WGuard'
option proto 'wireguard'
option private_key 'KEYanonymised'
option listen_port '115'
list addresses '192.168.10.2/24'
config wireguard_WGuard
option description 'Client'
option public_key 'KEYanonymised'
option private_key 'KEYanonymised'
list allowed_ips '192.168.10.65/32'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host '192.168.0.2'
option endpoint_port '115'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'WGuard'
config zone
option name 'WAN'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'WAN'
config rule
option name 'Allow-DHCP-Renew'
option src 'WAN'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'WAN'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'WAN'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'WAN'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'WAN'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'WAN'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'WAN'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'WAN'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'WAN'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Dev-0'
option src 'WAN'
option src_dport '110'
option dest_port '110'
option dest_ip '192.168.0.42'
option proto 'tcp udp'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Dev-1'
option src 'WAN'
option src_dport '111'
option dest_port '111'
option dest_ip '192.168.0.111'
option proto 'tcp udp'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Dev-2'
option src 'WAN'
option src_dport '112'
option dest_port '112'
option dest_ip '192.168.0.112'
option proto 'tcp udp'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WGuard'
list proto 'udp'
option src 'WAN'
option src_dport '115'
option dest_ip '192.168.0.2'
config rule
option name 'Allow-WG-Input'
list proto 'udp'
option src 'WAN'
option dest 'lan'
option dest_port '115'
option target 'ACCEPT'
Which port are you saying is at issue? Port 115 for Wireguard, or something else?
Or is it port 110, 111, or 112?
Either way, delete this as it is wrong:
config redirect option dest 'lan' option target 'DNAT' option name 'WGuard' list proto 'udp' option src 'WAN' option src_dport '115' option dest_ip '192.168.0.2'
I'm using port 115 for Wireguard.
The other ports are for the forwarding to other devices (which also doesn't work).
What exactly is wrong with this entry?
I actually created the Wireguard setup via Luci and only went into /etc/config/firewall afterwards.
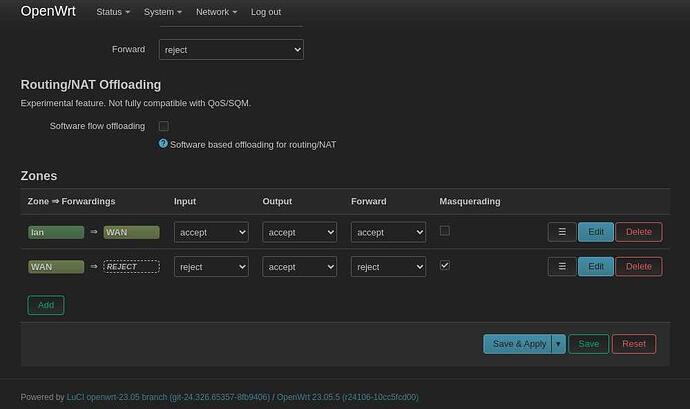
I'm attaching two screenshots of the zones/general settings in Luci. For some reason WAN has changed its colour, no idea if this carries any meaning. Can't pinpoint when it happened.
The other ports are for the forwarding to other devices (which also doesn't work).
Let's start with Wireguard because it's on the router itself, whereas the other services are forwarded to another host behind your router.
I actually created the Wireguard setup via Luci and only went into /etc/config/firewall afterwards.
You had two rules for port 115 -- a forward (redirect) and a traffic rule. The only one you want is the traffic rule. The other should not be used.
For some reason WAN has changed its colour, no idea if this carries any meaning. Can't pinpoint when it happened.
The color doesn't really matter, but the reason it changed is that you renamed the wan firewall zone from wan to WAN. This is not critical, but you've unnecessarily changed it and you're always best served by leaving things alone. It is generally recommended (but again not critical) to use lowercase for firewall zones, network names, and the like.
Let's start with this, though -- we need to know if your wan has a public IP or not.
Please post only the first two octets (in bold: aaa.bbb.ccc.ddd) of the following:
ifstatus wan | grep address
It seems it doesn't, but that may be because it is a static client of the ISP router on 192.168.0.1 whereas 192.168.0.2 is the default gateway for all LAN devices (so can post the whoe IP)
root@OpenWrt:~# ifstatus wan | grep address
"addresses",
"ipv4-address": [
"address": "192.168.0.2",
"ipv6-address": [
"ipv4-address": [
"ipv6-address": [
Now I will need to read up on the difference between using a port forward and a traffic rule.
I created the traffic rule and the port forward following several tutorials who all do at least the port forward whis this one doing both and if I understood the OpenWRT guide page it also indicates a firewall rule. Maybe I misunderstood it there.
![]()