Hello everyone,
I can't figure out how to forward ports that should be open for online gaming. I am using a TP-Link Archer C7 v5 with OpenWRT on it behind a Fritzbox 7412 (I basically followed this setup: Should I replace my Fritz!Box 7490? - #43 by bachph). I'm connected to the Internet via vectoring (fiber to an access point and then copper from there on). I've got an IPv4 but no IPv6 address and the ip address that the router's configuration shows is the same that I can see on https://whatismyipaddress.com/ (I came across a thread in which people thought that this might be relevant so I wanted to mention it as well).
I tried to forward ports that are listed on a game dev's website (e.g. for Call of Duty: Vanguard) but it seems like the ports are still closed (it tested it in game and online on websites such as https://canyouseeme.org).
As far as I understand it, all I have to do within the settings of the Fritzbox is to configure the TP-Link router as an exposed host so that I can forward ports using OpenWRT. Then I added new Port Forwards using OpenWRT that look like this:
Protocol: TCP
Souce Zone: WAN
External Port: 3074
Destination Zone: LAN
Internal IP address: any
Internal Port: any
Is there anything else that I have to configure or could there be another underlying issue (e.g. something preconfigured by my ISP)?
Thank you so much in advance for your help!
These need to be explicitly defined. The IP address needs to be the LAN address of the device that is hosting the service (I.e the game console or pc) and the port must be the same as the game is expecting (3074, it appears).
As long as the “exposed host” is configured properly to point to your openwrt router’s IP address and it actually sends all ports, it should be fine.
Thank you for your fast reply! I just adjusted the port forwards, restarted my router and the gaming pc but it looks like the ports are still closed. I tried the same with a different device (opening port 80 for my laptop) but this port is also closed according to https://www.yougetsignal.com/tools/open-ports/ .
You must be actively running the game/service when you try a port scan.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
Also please show us the “exposed host” setup from the fritz box and the openwrt’s wan IP address.
I hope that there's no sensible data visible in these files. Please let me know if there's anything that I should redact.
Network Config:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix ‚XXX‘ (redacted because I wasn’t sure if this is sensible data or not)
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
option mtu '1472'
option mtu6 '1472'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config device
option name 'eth0.2'
option type '8021q'
option ifname 'eth0'
option vid '2'
option mtu '1472'
option mtu6 '1472'
config device
option name 'eth0'
option mtu '1472'
option mtu6 '1472'
config device
option name 'eth0.1'
option type '8021q'
option ifname 'eth0'
option vid '1'
option mtu '1472'
option mtu6 '1472'
config device
option name 'wlan0'
option mtu '1472'
option mtu6 '1472'
config device
option name 'wlan1'
option mtu '1472'
option mtu6 '1472'
config device
option name 'wlan1-1'
option mtu '1472'
option mtu6 '1472'
Firewall Config:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'CoD Vanguard'
list proto 'tcp'
option src 'wan'
option src_dport '3074'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'CoD Vanguard'
list proto 'tcp'
option src 'wan'
option src_dport '27014-27050'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'CoD Vanguard'
list proto 'udp'
option src 'wan'
option src_dport '3074-3079'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Test'
list proto 'tcp'
option src 'wan'
option src_dport '80'
option dest_ip '192.168.1.185'
option dest_port '80'
Screenshot Fritzbox:
These all need the dest_ip and dest_port fields (similar to what you have done in the "Test" redirect rule). The first rule (3074) is effectively duplicated by the 3rd one (3074-3079), so you might want to remove the first rule. Be sure to verify that these are the required ports.
Aargh, sorry. I already pulled the info before I applied the saved settings. I just did that and restarted all three devices (fritzbox, tp-link archer, pc) but the nat type ist still listed as "strict". I followed https://portforward.com/call-of-duty-vanguard/ when it comes to the port forwards. I thought that I had to add both entries because 3074 is TCP and 3074-3079 is UDP – but then again, as you can tell I know barely anything about network protocols.
Oh... good catch. I missed that one was TCP and the other was UDP. You do need both. I'm just starting my first cup of coffee...lol.
I'm glad I got that one right :D. Is there anything else I should try before reaching out to my ISP?
I never noticed that there's a problem until a couple of days ago when I bought my first gaming pc after about 10 years only to experience severe connection problems that seem – at least that's what the game support told me – to be connected to NAT issues/port forwarding.
can you verify that the OpenWrt router has 192.168.178.21 as the WAN address?
Now I'm totally confused: While the Fritzbox lists the OpenWRT Router's address as .21 in the firewall settings, it shows .22 within the network overview. Within OpenWRT I get
IPv4 Upstream
Protocol: DHCP client
Address: 192.168.178.22/24
Gateway: 192.168.178.1
I tried to manually set the Open WRT's router to .22 within the fritzbox network settings but I just get an error (error code 1).
This will obviously need to be resolved. Can you just edit the exposed host rule on the fritz to set it to 192.168.178.22? Or delete that rule and then create a new one?
I can't edit/force the IP address for the exposed host rule. I can delete it, but the device is still listed with .21 so that I can only add new rules. I also realized that I can set the router's ip to any other address (such as .25, .26) but .21 (= the ip address shown in the firewall rules tab of the fritzbox).
There are a few other ways to handle this...
you could set the OpenWrt to use a static IP on the WAN. To do this, you'll need to make sure that it is outside the DHCP scope of the Fritz. Then you'll set the exposed host to that static IP.
Or, you can see if your Fritz allows 'DHCP reservations' -- allowing you to specify an address that the Fritz will assign to your OpenWrt router using DHCP.
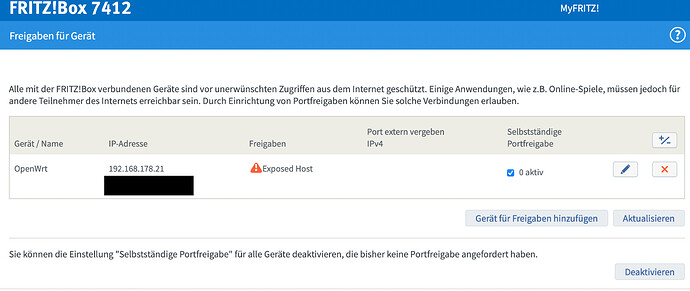
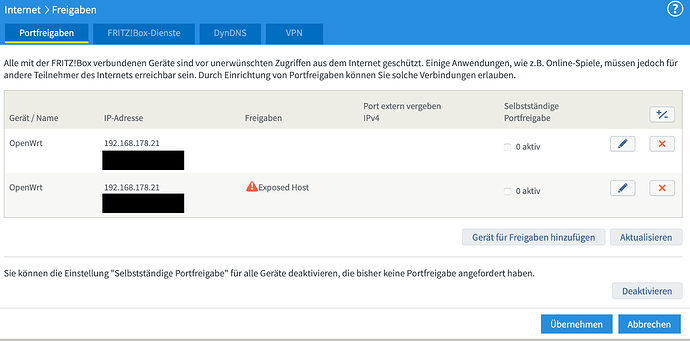
Ok so I changed the DHCP scope for the fritzbox and set the OpenWRT router's IP address to 192.168.178.21 so that the exposed host rule applies. The OpenWRT router is now also listed with its static IP address within the fritzbox network overview. I experienced something weird from the fritzbox, though: When I set the exposed host rule and accept changes, it creates a second entry (see attached screenshot). Is this something I should worry about?
I have no idea how the Fritzbox works... and I don't read or speak German, so I can only guess at that screen. However, it looks like those rules are not active.
If you changed the OpenWrt box to use static IP on the WAN, make sure it has all of the necessary information on the WAN -- IP, subnet mask, dns, and gateway.
I'm sorry, I should have added some more context: The first entry does not contain any rules. I can't even edit or delete it because all I get is an error message. The second one is active (The box that I can check is for UPNP which is not active at the moment. I made sure to keep the network settings except for the IP address (= same subnet mask, dns, gateway) and I can still use my connection (I checked that the IP changed) but it looks like the port forwards are still not active. At this point I am wondering if the fritzbox is just acting weird here and whether or not I should just reset it / contact support.
Please confirm the following:
- your Fritz shows an address on its WAN, and that matches the address you see when you use an external IP checker (such as googling "what's my IP")
- Your OpenWrt device has 192.168.178.21/24 (subnet mask 255.255.255.0) on its WAN (static assignment) complete with a valid gateway (192.168.178.1) and DNS, and you are able to access the internet normally through the OpenWrt device
- Your Fritz is forwarding all ports to your OpenWrt device (sometimes called DMZ).
- if you can't guarantee that it is forwarding all ports, you might need to setup port forwarding on the Fritz similar to the way you have done it on the OpenWrt system, but on the Fritz, you'd be sending those ports to 192.168.178.21.
- You've fixed your OpenWrt redirect rules to include the dest_ip and the dest_port fields that point to your gaming PC (and you have verified that your gaming PC has the same IP address used in the dest_ip field).
- You're running the game when you attempt the port scan
If all of those are true and verified, you may want to ask your ISP if they have any restrictions on inbound connections and/or how to configure the Fritz to forward all ports to a specific host.
First, let me thank you for your effort!
I can confirm that all settings match; however, the ports seem to be closed. I am going to follow your suggestion and forward the ports 1 by 1 within the fritzbox as well before contacting my ISP.
It actually helped forwarding the ports twice (within the OpenWRT router and the fritzbox) and they are in fact open right now.
Now I'm facing another challenge and I'm not sure if I should open a new thread for this or just continue within this one: I experienced serious latency issues so I got in contact with the game dev's support. They told me that this might be due to my double NAT setup. Is there anything I can do in this situation?
I also realized that the two entries for port forwarding rules within the Fritzbox (one for all the ports, the second for the exposed host rule) point to the same IP address but different mac addresses (A and B at the end). Are these just pointing to different interfaces (wireless vs. lan)? I can't choose which mac address to use when setting up the rules. Even after a factory reset, the fritzbox automatically creates separate entries for port forwarding and the exposed host rule.