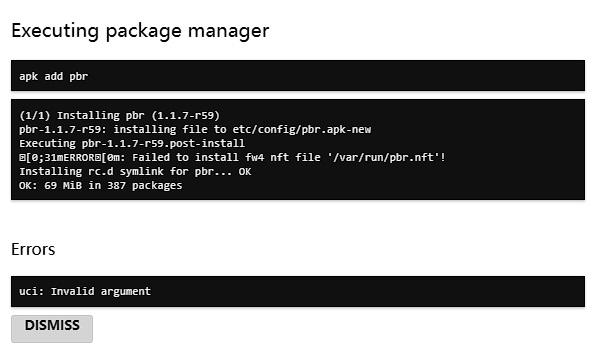
Im trying to set up pbr on a brand new router, but when I test a simple rule to send a given IP (192.168.0.5, using 'test' rule in PBR) over a Wireguard tunnel nothing works on that machine.
ubus call system board
{
"kernel": "6.6.61",
"hostname": "MT6000",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT6000",
"board_name": "glinet,gl-mt6000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "SNAPSHOT",
"revision": "r28320-e01af5e8d6",
"target": "mediatek/filogic",
"description": "OpenWrt SNAPSHOT r28320-e01af5e8d6",
"builddate": "1732212090"
}
}
uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
uci export firewall
package firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'
config zone
option name 'wg_taa'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wg_taa'
config forwarding
option src 'wg_taa'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'wg_taa'
uci export network
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd3e:252a:bdf0::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1.911'
option proto 'pppoe'
option username 'XXXXXXXXXXXXXX'
option password 'YYYYYYYYYYYYYY'
option ipv6 'auto'
option sourcefilter '0'
option delegate '0'
config interface 'wg_taa'
option proto 'wireguard'
option private_key 'XXXXXXXXXXXXXXXXXXXXXXXXXXX'
list addresses '10.8.0.3/24'
list dns '1.1.1.1'
option route_allowed_ips '0'
config wireguard_wg_taa
option description 'YYYYY'
option public_key 'XXXXXXXXXXXXXX'
option preshared_key 'XXXXXXXXXXXXXXXXXXXXX'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option endpoint_host 'xxxxxxxx.org'
option endpoint_port '51820'
uci export pbr
package pbr
config pbr 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'dnsmasq.nftset'
list resolver_instance '*'
option ipv6_enabled '0'
list ignored_interface 'vpnserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_boot_delay '0'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
option nft_rule_counter '0'
option nft_set_auto_merge '1'
option nft_set_counter '0'
option nft_set_flags_interval '1'
option nft_set_flags_timeout '0'
option nft_set_policy 'performance'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '0'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '0'
config dns_policy
option name 'Redirect Local IP DNS'
option src_addr '192.168.1.5'
option dest_dns '1.1.1.1'
option enabled '0'
config policy
option name 'Ignore Local Requests'
option interface 'ignore'
option dest_addr '10.0.0.0/24 10.0.1.0/24 192.168.100.0/24 192.168.1.0/24'
option enabled '0'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
option enabled '0'
config policy
option name 'test'
option src_addr '192.168.0.5'
option interface 'wg_taa'
option enabled '0'
/etc/init.d/pbr status
pbr - environment
pbr 1.1.7-47 running on OpenWrt SNAPSHOT.
Dnsmasq version 2.90 Copyright (c) 2000-2024 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP conntrack no-ipset nftset auth cryptohash DNSSEC no-ID loop-detect inotify dumpfile
pbr fw4 nft file: /usr/share/nftables.d/ruleset-post/30-pbr.nft
add chain inet fw4 pbr_mark_0x010000
add rule inet fw4 pbr_mark_0x010000 mark set mark and 0xff00ffff xor 0x010000
add rule inet fw4 pbr_mark_0x010000 return
add chain inet fw4 pbr_mark_0x020000
add rule inet fw4 pbr_mark_0x020000 mark set mark and 0xff00ffff xor 0x020000
add rule inet fw4 pbr_mark_0x020000 return
pbr chains - policies
chain pbr_forward { # handle 37
}
chain pbr_input { # handle 38
}
chain pbr_output { # handle 39
}
chain pbr_postrouting { # handle 41
}
chain pbr_prerouting { # handle 40
}
chain pbr_dstnat { # handle 36
}
pbr chains - marking
chain pbr_mark_0x010000 { # handle 1193
meta mark set meta mark & 0xff01ffff | 0x00010000 # handle 1194
return # handle 1195
}
chain pbr_mark_0x020000 { # handle 1196
meta mark set meta mark & 0xff02ffff | 0x00020000 # handle 1197
return # handle 1198
}
pbr nft sets
IPv4 table 256 route: default via 84.65.64.1 dev pppoe-wan
IPv4 table 256 rule(s):
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
IPv4 table 257 route: default via 10.8.0.3 dev wg_taa
IPv4 table 257 rule(s):
29998: from all fwmark 0x20000/0xff0000 lookup pbr_wg_taa
/etc/init.d/pbr reload
Loading environment (on_start) Using wan interface (on_start): wan
Found wan gateway (on_start): 84.11.11.1
Setting up routing for 'wan/pppoe-wan/84.11.11.1' [✓]
Setting up routing for 'wg_taa/10.8.0.3' [✓]
Installing fw4 nft file [✓]
pbr 1.1.7-47 monitoring interfaces: wan wg_taa
pbr 1.1.7-47 (fw4 nft file mode) started with gateways:
wan/pppoe-wan/84.65.64.1 [✓]
wg_taa/10.8.0.3
WARNING: Please set 'dhcp.lan.force=1' to speed up service start-up.
/etc/init.d/pbr status
pbr - environment
pbr 1.1.7-47 running on OpenWrt SNAPSHOT.
Dnsmasq version 2.90 Copyright (c) 2000-2024 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP conntrack no-ipset nftset auth cryptohash DNSSEC no-ID loop-detect inotify dumpfile
pbr fw4 nft file: /usr/share/nftables.d/ruleset-post/30-pbr.nft
add chain inet fw4 pbr_mark_0x010000
add rule inet fw4 pbr_mark_0x010000 mark set mark and 0xff00ffff xor 0x010000
add rule inet fw4 pbr_mark_0x010000 return
add chain inet fw4 pbr_mark_0x020000
add rule inet fw4 pbr_mark_0x020000 mark set mark and 0xff00ffff xor 0x020000
add rule inet fw4 pbr_mark_0x020000 return
pbr chains - policies
chain pbr_forward { # handle 37
}
chain pbr_input { # handle 38
}
chain pbr_output { # handle 39
}
chain pbr_postrouting { # handle 41
}
chain pbr_prerouting { # handle 40
}
chain pbr_dstnat { # handle 36
}
pbr chains - marking
chain pbr_mark_0x010000 { # handle 1278
meta mark set meta mark & 0xff01ffff | 0x00010000 # handle 1279
return # handle 1280
}
chain pbr_mark_0x020000 { # handle 1281
meta mark set meta mark & 0xff02ffff | 0x00020000 # handle 1282
return # handle 1283
}
pbr nft sets
IPv4 table 256 route: default via 84.65.64.1 dev pppoe-wan
IPv4 table 256 rule(s):
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
IPv4 table 257 route: default via 10.8.0.3 dev wg_taa
IPv4 table 257 rule(s):
29998: from all fwmark 0x20000/0xff0000 lookup pbr_wg_taa
This is a very simple scenario, so im sure its something silly I have/havent done..
I've had it set up for a similar scenario before and it worked fine then.
Any advice as to what is going wrong?