OK - here's the info as requested in the ReadMe - sorry I hadn't spotted that. (Btw - ReadMe says "the output of /etc/init.d/pbr support" but the help for pbr said /etc/init.d/pbr status so I used that.)
Report Info
- content of
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option cachesize '10000'
list notinterface 'pppoe-wan'
list server '127.0.0.1#5053'
list server '/mask.icloud.com/'
list server '/mask-h2.icloud.com/'
list server '/use-application-dns.net/'
list server '127.0.0.1#5054'
option doh_backup_noresolv '-1'
option noresolv '1'
list doh_backup_server '127.0.0.1#5053'
list doh_backup_server '/mask.icloud.com/'
list doh_backup_server '/mask-h2.icloud.com/'
list doh_backup_server '/use-application-dns.net/'
list doh_backup_server '127.0.0.1#5054'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option leasetime '2h'
option ra_default '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
- content of
/etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
list network 'vodem'
list network 'van'
list network 'modem'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect 'dns_int'
option name 'Intercept-DNS'
option src 'lan'
option src_dport '53'
option proto 'tcp udp'
option target 'DNAT'
option family 'all'
option enabled '1'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
- content of
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc9:0a26:3e41::/48'
config device
option name 'br-lan'
option type 'bridge'
option ports 'eth2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0'
option proto 'pppoe'
option username '********'
option password '********'
option pppd_options 'debug'
option ipv6 '1'
option metric '10'
option peerdns '0'
list dns '45.90.28.123'
list dns '45.90.30.123'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2a07:a8c0::31:527d'
list dns '2a07:a8c1::31:527d'
option device 'pppoe-wan'
config interface 'van'
option device 'eth1'
option proto 'dhcp'
option ipv6 '0'
option peerdns '0'
list dns '45.90.28.181'
list dns '45.90.30.181'
option metric '20'
config interface 'modem'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.2.2'
option netmask '255.255.255.0'
config interface 'vodem'
option proto 'static'
option ipaddr '192.168.100.20'
option netmask '255.255.255.0'
option device 'eth1'
- content of
/etc/config/pbr
config pbr 'config'
option verbosity '2'
option resolver_set 'none'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
option strict_enforcement '1'
option ipv6_enabled '1'
option enabled '1'
config policy
option name 'C2VQF93F24'
option interface 'van'
option src_addr 'C2VQF93F24 2001:8b0:dc1b:1da1:1c50:a07d:4155:2869 2001:8b0:dc1b:1da1:6c61:5686:72b0:4ae1 fdc9:a26:3e41:0:1c9e:966c:7c49:733d 2001:8b0:dc1b:1da1::2d7'
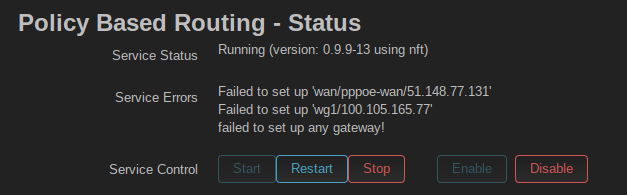
- the output of
/etc/init.d/pbr status
# /etc/init.d/pbr status -d
============================================================
pbr - environment
pbr 0.9.9-14 running on OpenWrt 22.03.2. WAN (IPv4): van/eth1/86.16.56.1. WAN (IPv6): wan6/pppoe-wan/2001:8b0:1111:1111:0:ffff:51bb:a8f9.
============================================================
Dnsmasq version 2.86 Copyright (c) 2000-2021 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-cryptohash no-DNSSEC no-ID loop-detect inotify dumpfile
============================================================
pbr chains - policies
chain pbr_forward {
}
chain pbr_input {
}
chain pbr_output {
}
chain pbr_prerouting {
ip saddr @pbr_van_4_src_ip_cfg026ff5 goto pbr_mark_0x020000 comment "C2VQF93F24"
ip6 saddr @pbr_van_6_src_ip_cfg026ff5 goto pbr_mark_0x020000 comment "C2VQF93F24"
ip6 saddr 2001:8b0:dc1b:1da1:1c50:a07d:4155:2869 goto pbr_mark_0x020000 comment "C2VQF93F24"
ip6 saddr 2001:8b0:dc1b:1da1:6c61:5686:72b0:4ae1 goto pbr_mark_0x020000 comment "C2VQF93F24"
ip6 saddr fdc9:a26:3e41:0:1c9e:966c:7c49:733d goto pbr_mark_0x020000 comment "C2VQF93F24"
ip6 saddr 2001:8b0:dc1b:1da1::2d7 goto pbr_mark_0x020000 comment "C2VQF93F24"
}
chain pbr_postrouting {
}
============================================================
pbr chains - marking
chain pbr_mark_0x010000 {
counter packets 0 bytes 0 meta mark set meta mark & 0xff01ffff | 0x00010000
return
}
chain pbr_mark_0x020000 {
counter packets 1042 bytes 147893 meta mark set meta mark & 0xff02ffff | 0x00020000
return
}
============================================================
pbr nft sets
set pbr_van_4_src_ip_cfg026ff5 {
type ipv4_addr
flags interval
auto-merge
comment "C2VQF93F24"
elements = { 192.168.1.208 }
}
set pbr_van_6_src_ip_cfg026ff5 {
type ipv6_addr
flags interval
auto-merge
comment "C2VQF93F24"
elements = { 2001:8b0:dc1b:1da1::2d7,
2001:8b0:dc1b:1da1:1c50:a07d:4155:2869,
2001:8b0:dc1b:1da1:6c61:5686:72b0:4ae1,
fdc9:a26:3e41:0:1c9e:966c:7c49:733d }
}
- the output of
/etc/init.d/pbr reload with verbosity setting set to 2
Activating traffic killswitch [✓]
Setting up routing for 'wan/pppoe-wan/81.187.81.187/2001:8b0:1111:1111:0:ffff:51bb:a8f9/128
fe80::3c14:6728:be16:7f79' [✓]
Setting up routing for 'van/eth1/86.16.56.1/2001:8b0:1111:1111:0:ffff:51bb:a8f9/128
fe80::3c14:6728:be16:7f79' [✓]
Routing 'C2VQF93F24' via van [✗]
Deactivating traffic killswitch [✓]
pbr 0.9.9-14 monitoring interfaces: wan
pbr 0.9.9-14 (nft) started with gateways:
wan/pppoe-wan/81.187.81.187/2001:8b0:1111:1111:0:ffff:51bb:a8f9/128
fe80::3c14:6728:be16:7f79 [✓]
van/eth1/86.16.56.1/2001:8b0:1111:1111:0:ffff:51bb:a8f9/128
fe80::3c14:6728:be16:7f79
ERROR: nft 'add rule inet fw4 pbr_prerouting ip saddr 2001:8b0:dc1b:1da1:1c50:a07d:4155:2869 goto pbr_mark_0x020000 comment "C2VQF93F24"'
ERROR: nft 'add rule inet fw4 pbr_prerouting ip saddr 2001:8b0:dc1b:1da1:6c61:5686:72b0:4ae1 goto pbr_mark_0x020000 comment "C2VQF93F24"'
ERROR: nft 'add rule inet fw4 pbr_prerouting ip saddr fdc9:a26:3e41:0:1c9e:966c:7c49:733d goto pbr_mark_0x020000 comment "C2VQF93F24"'
ERROR: nft 'add rule inet fw4 pbr_prerouting ip saddr 2001:8b0:dc1b:1da1::2d7 goto pbr_mark_0x020000 comment "C2VQF93F24"'
So I think I'm actually reporting two problems - the first occurred only after the move to 0.9.9-14 but the second is the important one for my use case and exists on both versions.
- On 0.9.9-14 when I create a rule explicitly containing the IPv6 addresses of a device, as well as the device name, routing works correctly (the device is forced onto
van and IPv4) and nft list ruleset gives a stanza correctly populated with the ipv6 addresses
set pbr_van_6_src_ip_cfg026ff5 {
type ipv6_addr
flags interval
auto-merge
comment "C2VQF93F24"
elements = { 2001:8b0:dc1b:1da1::2d7,
2001:8b0:dc1b:1da1:1c50:a07d:4155:2869,
2001:8b0:dc1b:1da1:6c61:5686:72b0:4ae1,
fdc9:a26:3e41:0:1c9e:966c:7c49:733d }
}
However with this rule I also get Service Errors in the luci app of this form for each v6 address
nft 'add rule inet fw4 pbr_prerouting ip saddr 2001:8b0:dc1b:1da1:1c50:a07d:4155:2869 goto pbr_mark_0x020000 comment "C2VQF93F24"'
Entering this command at the CLI gives
Error: Could not resolve hostname: Name does not resolve
add rule inet fw4 pbr_prerouting ip saddr 2001:8b0:dc1b:1da1::2d7 goto pbr_mark_0x020000 comment "C2VQF93F24"
^^^^^^^^^^^^^^^^^^^^^^^
I think this is because the generated command should be ip6 saddr not ip saddr?
- Contrariwise, if I create a rule just using the device name
C2VQF93F24 but no explicit IP addresses, then there are no errors, but the v6 addresses of the device are not added to the firewall rules and the elements section of the v6 stanza is left unpopulated like this:
set pbr_van_6_src_ip_cfg026ff5 {
type ipv6_addr
flags interval
auto-merge
comment "C2VQF93F24"
}
I think the main problem is the second one - adding a device name to the rule would ideally populate the pbr_van_6_src_ip_cfg026ff5 fully in the same way as it does for v4.