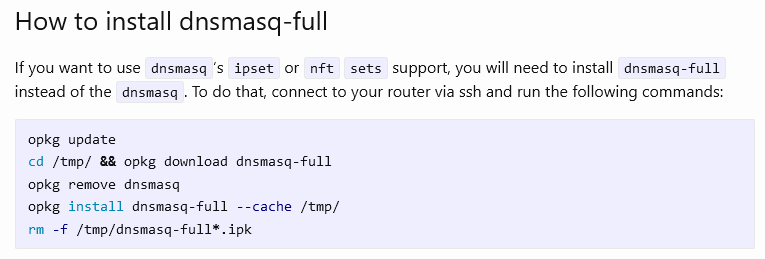
I just updated to OpenWRT 21.02.6, set up my dhcp and openvpn. Then I did dnsmasq-full, configured your repo and installed pbr-iptables and luci-app-pbr (after accidentally installing the "normal" pbr and then removing it). I then enabled pbr and set up a single policy for ipchicken.com so I could test it.
Unfortunately the service did not appear to work. It kept telling me:
user.notice pbr: Reload on interface status aborted: service not running.
On the Luci page it states:
Invalid OpenVPN config for nordvpn interface.
The VPN works fine, I'm connected just fine. The exact same configuration also worked on a test-router I did yesterday, where I installed OpenWRT 22.03. Exact same labels, names, tunnel configuration.
I did notice there's no IP listed:
Failed to set up 'nordvpn/tun0/0.0.0.0'!
In the log it stated:
daemon.notice procd: /etc/rc.d/S94pbr: Object "-full" is unknown, try "ip help".
So I tried starting it manually through /etc/rc.d/pbr (changed the IPs):
Activating traffic killswitch [✓]
Object "-full" is unknown, try "ip help".
Setting up routing for 'wan/111.222.333.444' Object "-full" is unknown, try "ip help".
Object "-full" is unknown, try "ip help".
[✗]
Object "-full" is unknown, try "ip help".
Setting up routing for 'nordvpn/tun0/0.0.0.0' Object "-full" is unknown, try "ip help".
Object "-full" is unknown, try "ip help".
[✗]
Routing 'IP Chicken' via wan [✓]
Deactivating traffic killswitch [✓]
pbr 1.1.0-21 monitoring interfaces: wan nordvpn
ERROR: Failed to set up 'wan/111.222.333.444'!
ERROR: Failed to set up 'nordvpn/tun0/0.0.0.0'!
ERROR: Failed to set up any gateway!
WARNING: Invalid OpenVPN config for 'nordvpn' interface.
This annoyed the heck out of me.
I noticed this line:
cat /etc/init.d/pbr | grep '\-full'
readonly ip_full='/usr/libexec/ip-full'
Which did exist:
ls -l /usr/libexec/
-rwxr-xr-x 1 root root 426308 Oct 27 2021 ip-full
But gave me the same error as in the logs:
/usr/libexec/ip-full
Object "-full" is unknown, try "ip help".
So on a whim I changed the line to /sbin/ip and tried starting pbr again:
Activating traffic killswitch [✓]
Setting up routing for 'wan/111.222.333.444' [✓]
Setting up routing for 'nordvpn/tun0/222.333.444.555' [✓]
Routing 'IP Chicken' via wan [✓]
Deactivating traffic killswitch [✓]
pbr 1.1.0-21 monitoring interfaces: wan nordvpn
pbr 1.1.0-21 (iptables) started with gateways:
wan/111.222.333.444
nordvpn/tun0/222.333.444.555 [✓]
WARNING: Invalid OpenVPN config for 'nordvpn' interface.
Apart from that odd error about the OpenVPN config (which comes straight from them) the service reports no further errors.
IPChicken still thinks I'm NordVPN though.
I'm just about out of ideas. Here's hoping somebody can help me over the weekend, otherwise connecting to work on Monday will be a challenge without a bypass.
EDIT: Yay, my browser forgot a few things and ipchicken now reports my ISP. So I guess it's working - sort of?