Because you need to add domains to an ipset/nft set, you have two people telling you the same thing.
First you say you don't want to use WebUI, now you "repeat" that your question is about WebUI?
Which one is it?
¯_(ツ)_/¯
where did i say that?
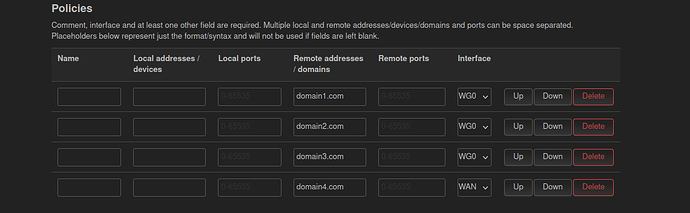
You can add them as a space delimited list: domain1.com domain2.com, etc.
i would like make like software dumaos
add source port and destination port 1-65535 dstination 3074
for the vpn
So what's stopping you?
i has the message
my vpn block internet
but my destination is changed well
other thread speak port forward pbr
Good morning 
I can´t install last pbr release 
Currently running: SNAPSHOT - r21950-90dbdb4941
Thanks ![]()
![]()
Snapshots are know to have issues every now and then, please flash latest stable release firmware on your router.
thx allot that is awesome
@stangri talking about domain lists does anyone have a list of domains that are ad/tracking related but blocking them would break websites so is betetr to send them on a VPN?
for example google fonts, fontawesome, etc
Hello,
First of all, thanks for pbr package.
I have a Wireguard client, installed on OpenWRT 22.03, and I want to set a global rule in PBR, that would route all requests, coming to http/https ports directly through WAN.
I've set a rule in pbr, and when I check on one of the websites ("what is my ip" google query) - it shows my WAN IP (https://whatismyipaddress.com/ and https://www.myip.com/), but other website is showing as WG IP (https://www.whatismyip.com/).
And that is happening quite often, when I try to enter some website and CloudFlare saying that I'm from banned IP, and shows WG IP there.
cat /etc/config/dhcp
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
option doh_backup_noresolv '-1'
option noresolv '1'
list doh_backup_server ''
list doh_backup_server '/mask.icloud.com/'
list doh_backup_server '/mask-h2.icloud.com/'
list doh_backup_server '/use-application-dns.net/'
list doh_backup_server '127.0.0.1#5054'
list doh_backup_server '127.0.0.1#5053'
list server '/mask.icloud.com/'
list server '/mask-h2.icloud.com/'
list server '/use-application-dns.net/'
list server '127.0.0.1#5054'
list server '127.0.0.1#5053'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
cat /etc/config/firewall
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
config zone
option name 'wg0'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'wg0'
option forward 'ACCEPT'
option masq '1'
config forwarding
option src 'lan'
option dest 'wg0'
cat /etc/config/network
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb8:ffac:1a2b::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.1'
config device
option name 'wan'
option macaddr '5c:02:14:30:3c:dc'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'wg0'
option proto 'wireguard'
option private_key 'GCArjaYCOjeD+RZE8lJmcC5d+/MV1oxxOvCapuvV8Vk='
list addresses '10.65.27.70/32'
list addresses 'fc00:bbbb:bbbb:bb01::2:1b45/128'
option peerdns '0'
config wireguard_wg0
option public_key 'nJEWae9GebEY7yJONXQ1j4gbURV4QULjx388woAlbDs='
list allowed_ips '0.0.0.0/1'
list allowed_ips '::0/1'
list allowed_ips '128.0.0.1/1'
option route_allowed_ips '1'
option endpoint_host '45.134.212.79'
option persistent_keepalive '25'
config wireguard_wg0
option public_key 'XwFAczY5LdogFwE9soDecXWqywSCDGuRyJhr/0psI00='
list allowed_ips '0.0.0.0/1'
list allowed_ips '::0/1'
list allowed_ips '128.0.0.1/1'
option route_allowed_ips '1'
option endpoint_host '45.128.38.226'
option persistent_keepalive '25'
cat /etc/config/pbr
root@OpenWrt:~# cat /etc/config/pbr
config pbr 'config'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'none'
option ipv6_enabled '0'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
option enabled '1'
list supported_interface 'wg0'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '1'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '1'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
option enabled '0'
config policy
option name 'direct'
option dest_port '7 53 80 443'
option interface 'wan'
config policy
option name 'dns-google'
option dest_addr '1.1.1.1'
option interface 'wan'
config policy
option name 'dns-cloud'
option dest_addr '8.8.8.8'
option interface 'wan'
config policy
option name 'direct-citrix'
option dest_port '1494 2598 8080 8008 16500-16509'
option interface 'wan'
/etc/init.d/pbr status
Does not let that big log paste - https://pastebin.com/3VfYSsaj
/etc/init.d/pbr reload
root@OpenWrt:~# /etc/init.d/pbr reload
Activating traffic killswitch [✓]
# Warning: iptables-legacy tables present, use iptables-legacy-save to see them
Setting up routing for 'wan/87.207.100.1' [✓]
Setting up routing for 'wg0/10.65.27.70' [✓]
Routing 'direct' via wan [✓]
Routing 'libtorrent' via wg0 [✓]
Routing 'dns-google' via wan [✓]
Routing 'dns-cloud' via wan [✓]
Routing 'direct-4a' via wan [✓]
Routing 'direct-4a-5g' via wan [✓]
Routing 'direct-mipad' via wan [✓]
Routing 'direct-citrix' via wan [✓]
Running /usr/share/pbr/pbr.user.aws [✓]
Running /usr/share/pbr/pbr.user.netflix [✓]
Deactivating traffic killswitch [✓]
pbr 1.0.1-16 monitoring interfaces: wan wg0
pbr 1.0.1-16 (nft) started with gateways:
wan/87.207.100.1
wg0/10.65.27.70 [✓]
root@OpenWrt:~#
I don't see anything obviously wrong with your config (except that when you stop https-dns-proxy you should have no DNS resolution on your network), however I can't help you avoid GeoIP blocking beyond what's written in the README, partially because most services taking GeoIP blocking seriously also block known/most commercial VPN providers.
I am not sure that is a GeoIP, I think they restrict access, because they see I'm going from a VPN provider.
The question is how they see it.
Whether request is actually going through wg0 interface or they somehow know that I can also use other IP.
I guess the only way to deal with this problem is to revert my configuration to route by default through WAN and selectively through wg0? I think I was trying to configure that way in vpn-bypass with torrent client, and I think I was not sure I did it right way, and was not sure it does not leak through wan interface.
I thought it would be easier to do the other way and just select devices that go directly or ports I don't want to route in wg0.
Is it possible that the pbr.user.aws is set to WAN as most website are hosted via Amazon's EC2? elgatito
Try and disable pbr.user.aws under Luci by unticking it and apply.
After upgrading from version 16 to 21 no Internet on the router. Uninstall 21 and back to 16 and Internet is back.
Can't reporduce.
mwan3 was the reason. strange that in version 16 it works fine.
Is there a way to make mwan3 and pbr work together?
Possibly. README has information for you in the Getting Help section.
AWS IS enabled and selected to route through WAN. But how it can influence that Cloudflare detects Wireguard IP when I expect to access 80/443 ports only through WAN?