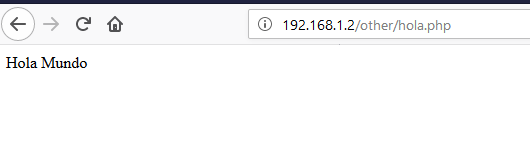
Adding this information maybe could be useful
root@OpenWrt:~# php-cgi -v
PHP 7.2.16 (cgi-fcgi)
Copyright (c) 1997-2018 The PHP Group
Zend Engine v3.2.0, Copyright (c) 1998-2018 Zend Technologies
php.ini
[PHP]
zend.ze1_compatibility_mode = Off
; Language Options
engine = On
;short_open_tag = Off
precision = 12
y2k_compliance = On
output_buffering = Off
;output_handler =
zlib.output_compression = Off
;zlib.output_compression_level = -1
;zlib.output_handler =
implicit_flush = Off
unserialize_callback_func =
serialize_precision = 100
;open_basedir =
disable_functions =
disable_classes =
; Colors for Syntax Highlighting mode. Anything that's acceptable in
; <span style="color: ???????"> would work.
;highlight.string = #DD0000
;highlight.comment = #FF9900
;highlight.keyword = #007700
;highlight.bg = #FFFFFF
;highlight.default = #0000BB
;highlight.html = #000000
;ignore_user_abort = On
;realpath_cache_size = 16k
;realpath_cache_ttl = 120
; Miscellaneous
expose_php = On
; Resource Limits
max_execution_time = 30 ; Maximum execution time of each script, in seconds.
max_input_time = 60 ; Maximum amount of time each script may spend parsing request data.
;max_input_nesting_level = 64
memory_limit = 8M ; Maximum amount of memory a script may consume.
; Error handling and logging
; Error Level Constants:
; E_ALL - All errors and warnings (includes E_STRICT as of PHP 6.0.0)
; E_ERROR - fatal run-time errors
; E_RECOVERABLE_ERROR - almost fatal run-time errors
; E_WARNING - run-time warnings (non-fatal errors)
; E_PARSE - compile-time parse errors
; E_NOTICE - run-time notices (these are warnings which often result
; from a bug in your code, but it's possible that it was
; intentional (e.g., using an uninitialized variable and
; relying on the fact it's automatically initialized to an
; empty string)
; E_STRICT - run-time notices, enable to have PHP suggest changes
; to your code which will ensure the best interoperability
; and forward compatibility of your code
; E_CORE_ERROR - fatal errors that occur during PHP's initial startup
; E_CORE_WARNING - warnings (non-fatal errors) that occur during PHP's
; initial startup
; E_COMPILE_ERROR - fatal compile-time errors
; E_COMPILE_WARNING - compile-time warnings (non-fatal errors)
; E_USER_ERROR - user-generated error message
; E_USER_WARNING - user-generated warning message
; E_USER_NOTICE - user-generated notice message
; E_DEPRECATED - warn about code that will not work in future versions
; of PHP
; E_USER_DEPRECATED - user-generated deprecation warnings
;
; Common Values:
; E_ALL & ~E_NOTICE (Show all errors, except for notices and coding standards warnings.)
; E_ALL & ~E_NOTICE | E_STRICT (Show all errors, except for notices)
; E_COMPILE_ERROR|E_RECOVERABLE_ERROR|E_ERROR|E_CORE_ERROR (Show only errors)
; E_ALL | E_STRICT (Show all errors, warnings and notices including coding standards.)
; Default Value: E_ALL & ~E_NOTICE
error_reporting = E_ALL & ~E_NOTICE & ~E_STRICT
display_errors = On
display_startup_errors = Off
log_errors = Off
log_errors_max_len = 1024
ignore_repeated_errors = Off
ignore_repeated_source = Off
report_memleaks = On
;report_zend_debug = 0
track_errors = Off
;html_errors = Off
;docref_root = "/phpmanual/"
;docref_ext = .html
;error_prepend_string = "<font color=#ff0000>"
;error_append_string = "</font>"
; Log errors to specified file.
;error_log = /var/log/php_errors.log
; Log errors to syslog.
;error_log = syslog
; Data Handling
;arg_separator.output = "&"
;arg_separator.input = ";&"
variables_order = "EGPCS"
request_order = "GP"
register_globals = Off
register_long_arrays = Off
register_argc_argv = On
auto_globals_jit = On
post_max_size = 8M
;magic_quotes_gpc = Off
magic_quotes_runtime = Off
magic_quotes_sybase = Off
auto_prepend_file =
auto_append_file =
default_mimetype = "text/html"
;default_charset = "iso-8859-1"
;always_populate_raw_post_data = On
; Paths and Directories
; UNIX: "/path1:/path2"
;include_path = ".:/php/includes"
doc_root = "/etc/nodogsplash/htdocs"
user_dir =
extension_dir = "/usr/lib/php"
enable_dl = On
cgi.force_redirect = 1
cgi.nph = 1
cgi.redirect_status_env = ;
cgi.fix_pathinfo=1
fastcgi.impersonate = 1;
fastcgi.logging = 0
cgi.rfc2616_headers = 0
; File Uploads
file_uploads = On
upload_tmp_dir = "/tmp"
upload_max_filesize = 2M
max_file_uploads = 20
; Fopen wrappers
allow_url_fopen = On
allow_url_include = Off
;from="john@doe.com"
;user_agent="PHP"
default_socket_timeout = 60
;auto_detect_line_endings = Off
uhttpd
# Server configuration
config uhttpd main
# HTTP listen addresses, multiple allowed
list listen_http 0.0.0.0:80
list listen_http [::]:80
# HTTPS listen addresses, multiple allowed
list listen_https 0.0.0.0:443
list listen_https [::]:443
# Redirect HTTP requests to HTTPS if possible
option redirect_https 1
# Server document root
option home /www
# Reject requests from RFC1918 IP addresses
# directed to the servers public IP(s).
# This is a DNS rebinding countermeasure.
option rfc1918_filter 1
# Maximum number of concurrent requests.
# If this number is exceeded, further requests are
# queued until the number of running requests drops
# below the limit again.
option max_requests 3
# Maximum number of concurrent connections.
# If this number is exceeded, further TCP connection
# attempts are queued until the number of active
# connections drops below the limit again.
option max_connections 100
# Certificate and private key for HTTPS.
# If no listen_https addresses are given,
# the key options are ignored.
option cert /etc/uhttpd.crt
option key /etc/uhttpd.key
# CGI url prefix, will be searched in docroot.
# Default is /cgi-bin
option cgi_prefix /cgi-bin
# List of extension->interpreter mappings.
# Files with an associated interpreter can
# be called outside of the CGI prefix and do
# not need to be executable.
list interpreter ".php=/usr/bin/php-cgi"
# list interpreter ".cgi=/usr/bin/perl"
# Lua url prefix and handler script.
# Lua support is disabled if no prefix given.
option lua_prefix /luci
option lua_handler /usr/lib/lua/luci/sgi/uhttpd.lua
# Specify the ubus-rpc prefix and socket path.
# option ubus_prefix /ubus
# option ubus_socket /var/run/ubus.sock
# CGI/Lua timeout, if the called script does not
# write data within the given amount of seconds,
# the server will terminate the request with
# 504 Gateway Timeout response.
option script_timeout 60
# Network timeout, if the current connection is
# blocked for the specified amount of seconds,
# the server will terminate the associated
# request process.
option network_timeout 30
# HTTP Keep-Alive, specifies the timeout for persistent
# HTTP/1.1 connections. Setting this to 0 will disable
# persistent HTTP connections.
option http_keepalive 20
# TCP Keep-Alive, send periodic keep-alive probes
# over established connections to detect dead peers.
# The value is given in seconds to specify the
# interval between subsequent probes.
# Setting this to 0 will disable TCP keep-alive.
option tcp_keepalive 1
# Basic auth realm, defaults to local hostname
# option realm OpenWrt
# Configuration file in busybox httpd format
# option config /etc/httpd.conf
# Do not follow symlinks that point outside of the
# home directory.
# option no_symlinks 0
# Do not produce directory listings but send 403
# instead if a client requests an url pointing to
# a directory without any index file.
# option no_dirlists 0
# Do not authenticate any ubus-rpc requests against
# the ubus session/access procedure.
# This is dangerous and should be always left off
# except for development and debug purposes!
# option no_ubusauth 0
# For this instance of uhttpd use the listed httpauth
# sections to require Basic auth to the specified
# resources.
# list httpauth prefix_user
# Defaults for automatic certificate and key generation
config cert defaults
# Validity time
option days 730
# RSA key size
option bits 2048
# Location
option country ZZ
option state Somewhere
option location Unknown
# Common name
option commonname 'OpenWrt'
# config httpauth prefix_user
# option prefix /protected/url/path
# option username user
# option password 'plaintext_or_md5_or_$p$user_for_system_user'
config uhttpd 'fusionpbx'
list listen_http '0.0.0.0:2050'
list listen_http '[::]:2050'
option redirect_https '1'
option home '/etc/nodogsplash/htdocs'
option index_page 'splash.html'
option rfc1918_filter '1'
option max_requests '3'
option max_connections '100'
option cert '/etc/uhttpd.crt'
option key '/etc/uhttpd.key'
list interpreter '.php=/usr/bin/php-cgi'
option script_timeout '60'
option network_timeout '30'
option http_keepalive '20'
option tcp_keepalive '1'
option realm 'GoFLEX'
option no_symlinks '0'
nodogsplash file
# The options available here are an adaptation of the settings used in nodogsplash.conf.
# See https://github.com/nodogsplash/nodogsplash/blob/master/resources/nodogsplash.conf
config nodogsplash
# Set to 0 to disable nodogsplash
option enabled 1
# Set to 0 to disable hook that makes nodogsplash restart when the firewall restarts.
# This hook is needed as a restart of Firewall overwrites nodogsplash iptables entries.
option fwhook_enabled '1'
# Serve the file splash.html from this directory
option webroot '/etc/nodogsplash/htdocs'
# Use plain configuration file
#option config '/etc/nodogsplash/nodogsplash.conf'
# Use this option to set the device nogogsplash will bind to.
# The value may be an interface section in /etc/config/network or a device name such as br-lan.
option gatewayinterface 'br-lan'
option gatewayname 'BIDERBOST_HOTSPOT'
option maxclients '30'
# Enables debug output (0-7)
#option debuglevel '7'
# Client timeouts in minutes
option preauthidletimeout '30'
option authidletimeout '120'
# Session Timeout is the interval after which clients are forced out (a value of 0 means never)
option sessiontimeout '1200'
# The interval in seconds at which nodogsplash checks client timeout status
option checkinterval '600'
# Enable BinAuth Support.
# If set, a program is called with several parameters on authentication (request) and deauthentication.
# Request for authentication:
# $<BinAuth> auth_client <client_mac> '<username>' '<password>'
#
# The username and password values may be empty strings and are URL encoded.
# The program is expected to output the number of seconds the client
# is to be authenticated. Zero or negative seconds will cause the authentification request
# to be rejected. The same goes for an exit code that is not 0.
# The output may contain a user specific download and upload limit in KBit/s:
# <seconds> <upload> <download>
#
# Called on authentication or deauthentication:
# $<BinAuth> <*auth|*deauth> <incoming_bytes> <outgoing_bytes> <session_start> <session_end>
#
# "client_auth": Client authenticated via this script.
# "client_deauth": Client deauthenticated by the client via splash page.
# "idle_deauth": Client was deauthenticated because of inactivity.
# "timeout_deauth": Client was deauthenticated because the session timed out.
# "ndsctl_auth": Client was authenticated manually by the ndsctl tool.
# "ndsctl_deauth": Client was deauthenticated by the ndsctl tool.
# "shutdown_deauth": Client was deauthenticated by Nodogsplash terminating.
#
# Values session_start and session_start are in seconds since 1970 or 0 for unknown/unlimited.
#
#option binauth '/bin/myauth.sh'
# Enable Forwarding Authentication Service (FAS)
# If set redirection is changed from splash.html to a FAS (provided by the system administrator)
# The value is the IP port number of the FAS
#option fasport '80'
# Option: fasremoteip
# Default: GatewayAddress (the IP of NDS)
# If set, this is the remote ip address of the FAS.
#option fasremoteip '46.32.240.41'
# Option: faspath
# Default: /
# This is the path from the FAS Web Root to the FAS login page
# (not the file system root).
#option faspath '/onboard-wifi.net/nodog/fas.php'
# Option: fas_secure_enabled
# Default: 1
# If set to "1", authaction and the client token are not revealed and it is the responsibility
# of the FAS to request the token from NDSCTL.
# If set to "0", the client token is sent to the FAS in clear text in the query string of the
# redirect along with authaction and redir.
#option fas_secure_enabled '0'
# Your router may have several interfaces, and you
# probably want to keep them private from the network/gatewayinterface.
# If so, you should block the entire subnets on those interfaces, e.g.:
#list authenticated_users 'block to 192.168.0.0/16'
#list authenticated_users 'block to 10.0.0.0/8'
# Typical ports you will probably want to open up.
#list authenticated_users 'allow tcp port 22'
#list authenticated_users 'allow tcp port 53'
#list authenticated_users 'allow udp port 53'
#list authenticated_users 'allow tcp port 80'
#list authenticated_users 'allow tcp port 443'
# Or for happy customers allow all
list authenticated_users 'allow all'
# For preauthenticated users to resolve IP addresses in their
# initial request not using the router itself as a DNS server,
# Leave commented to help prevent DNS tunnelling
#list preauthenticated_users 'allow tcp port 53'
#list preauthenticated_users 'allow udp port 53'
# Allow ports for SSH/Telnet/DNS/DHCP/HTTP/HTTPS
list users_to_router 'allow tcp port 22'
list users_to_router 'allow tcp port 23'
list users_to_router 'allow tcp port 53'
list users_to_router 'allow udp port 53'
list users_to_router 'allow udp port 67'
list users_to_router 'allow tcp port 80'
# MAC addresses that are / are not allowed to access the splash page
# Value is either 'allow' or 'block'. The allowedmac or blockedmac list is used.
#option macmechanism 'allow'
#list allowedmac '00:00:C0:01:D0:0D'
#list allowedmac '00:00:C0:01:D0:1D'
#list blockedmac '00:00:C0:01:D0:2D'
# MAC addresses that do not need to authenticate
#list trustedmac '00:00:C0:01:D0:1D'
# Nodogsplash uses specific HEXADECIMAL values to mark packets used by iptables as a bitwise mask.
# This mask can conflict with the requirements of other packages such as mwan3, sqm etc
# Any values set here are interpreted as in hex format.
#
# List: fw_mark_authenticated
# Default: 30000 (0011|0000|0000|0000|0000 binary)
#
# List: fw_mark_trusted
# Default: 20000 (0010|0000|0000|0000|0000 binary)
#
# List: fw_mark_blocked
# Default: 10000 (0001|0000|0000|0000|0000 binary)
#
#list fw_mark_authenticated '30000'
#list fw_mark_trusted '20000'
#list fw_mark_blocked '10000'
option redirecturl 'https://www.tdtlatinoamerica.com.ar/'
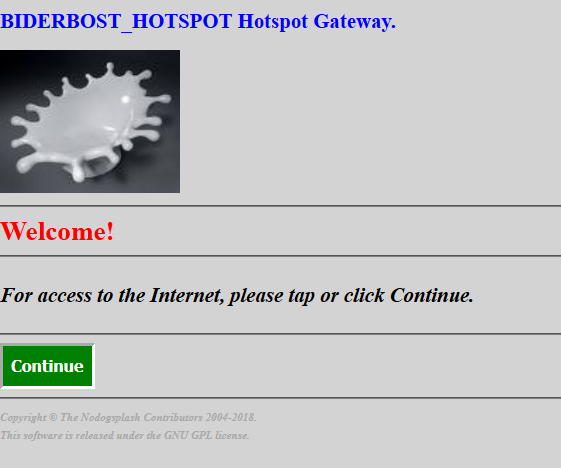
 So there is no way to do a PHP code captcha before to have access to internet?
So there is no way to do a PHP code captcha before to have access to internet?