I'm not good with the terminology so don't really what to look for, but I'll explain, and sorry if too off topic I will seek elsewere.
On my network I have the ISP router (lan1) to which are connected many different people. Then there is a switch and my router running openwrt (lan2) connected to it.
I want to have a server (running http ssh) connected to the switch, so on lan1, but have it completely isolated and tunneled to my router in lan2.
What is the best way for doing this? Vpn?
If it's already tunneled. you're OK.
I surmise you're seeking Port Forwarding.
Now it's not configured yet. Is tunneling what I want?
Port forwarding is just for selected ports, I want the server to be like as if it was connected to lan2 and not lan1.
What does that exactly mean?
Also, what exactly does this mean?
Because, I'd just say connect it to LAN2...(i.e. tell us the importance of you wanting it physically on LAN1).
 Have it not accessible and hidden from users of lan1.
Have it not accessible and hidden from users of lan1.
Also have it part of lan2 so when I'm out I can access it with a vpn tunnel to lan2.
Because the location where the switch is is much cooler than where my lan2 is, which is near literally in an oven. Also because it's out of the way with no access to people, close to the electrical panels.
- Assign a another LAN IP to the WAN of the OpenWrt
- NAT all ports on that IP - to the server (i.e. a DMZ)
I don't believe i can do that, the ISP router I don't have much control over.
That is if I correctly understand how to do that.
OK...I'm lost.
I said:
And you responded:
I never mentioned your ISP's router. Perhaps you should better explain what your concept is - and how it relates to the OpenWrt device.
Or...are you saying you cannot control the ISP router to make port forwards...?
If so, you need a VPN service that allows you to have inbound network traffic - then. They're not common.
Your server is connected to a switch on LAN1, but you want it to be inaccessible from other devices on LAN1... Is it a "managed switch"? Can you configure VLANs on it?
No I'ts a Netgear GS108
Yes port forwards I can do on the ISP router but that's about it.
I try to reformulate: I have lan1 which is under the ISP router, where many different unknown people connect.
Connected to lan1 I have the switch, from where my OpenWRT device is connected, creating my lan 2 with printer etc.
I have already setup a wireguard vpn to access my lan2 from outside because I had sftp server and motion setup on the openwrt device.
Now i've setup this little server which I really would like to connect to the switch so on lan1, mainly for heat reasons and to have it hidden out of the way but I don't want it to be accessible from lan1 and part of lan2.
When I access it from the vpn it's easier to have it on lan2.
Also my main pc on lan2 is most of the time connected to a vpn service, which lets me still contact local traffic, but not if it's on lan1.
Hope it makes sense
So, you have a server plus a bunch of other devices connected to the same dumb switch, but you want to separate the server from the other devices... I do not think this is possible, perhaps someone else can come up with an imaginative solution.
No I have a server and a OpenWRT router connected to the dumb switch, and I want to tunnel the server into the OpenWRT lan without it being accessible from the lan where it's physically connected.
What I can think of is run wireguard server on the openwrt and connect the server to it.
- I would tag the ports and see if the dumb switch will pass the tags. Most that are capable of jumbo frames will.
- Yes, Wireguard will work too; but this seems elaborate - and I'm confused, as you told me above it's not setup - then later, it is. If a VPN is setup, you should be OK now.
- The real solution is to plug this server physically into the correct LAN; but you noted that in order to do so, you'd have to put the server into an oven.
- The other option is to use a managed switch, then you're not trying to rig-up an un-managed one
(Also, we can all see you - no need to make 2 posts to respond to each person.)
If you can't physically move the server, two "reasonable" options are
- Long Ethernet cable
- Managed switch
Either one seems to be a much better choice than running a VPN to it in terms of bandwidth, power/resource consumption, and ease of installation and ongoing maintenance.
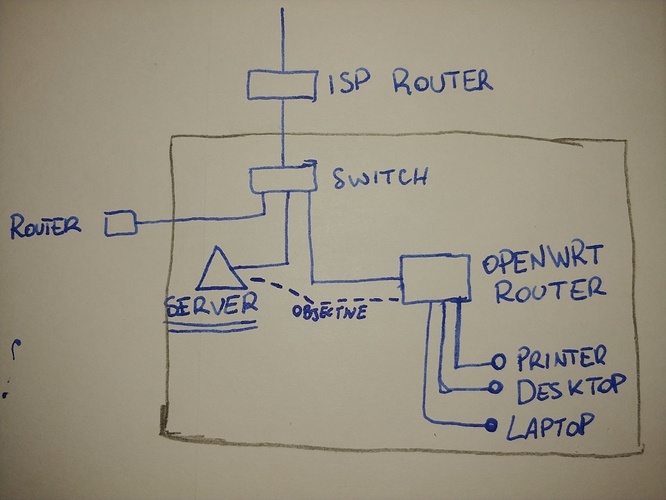
I think you should draw a diagram of your network.
Connecting an OpenWrt router to the switch does not change the fact that both the server and the other clients are connected to the same dumb switch.
Hope it's more clear. The grey rectangle is the area I have access to.
@lleachii I will look deeper into this port tagging which i don't know of.
Wireguard is set up at the moment so I can connect to my router from my phone eg. on my data plan and have access to my network.
I had started making a second interface on the router especially for the server, but I suppose I just need the one.
Also @jeff yes a cable is an option I thought of as the existing one connecting the openwrt router and the switch I threaded it. But I no longer have crimping tool nor cable nor the plastic thing to thread, I would much prefer something without buying more stuff.