This is expected behavior... the downstream network can access the upstream network unless specific firewall rules have been put in place to block it.
Put a cell phone in hotspot mode then connect the Surface Pro to it. That will be a truly "outside" Internet connection to simulate being away from home.
Another option would be a commercial VPN service linked on the travel router, so everything from the travel router's LAN tunnels outside the house then comes back in from the VPN service's IP.
New info:
- WG client app installed on phone (android Note20 if it matters)
- New phone peer defined in OWRT, as 192.168.9.3, and also configured on phone
Connection results:
- Endpoint = mydomain.com:51280
- connection failed with phone connected, and disconnected, from home wifi
- Endpoint = 72.212.x.y:51280
- connection successful, with phone connected to home wifi
- connection failed, with phone disconnected from home wifi
From the home LAN, go to any "what's my IP" site and confirm the result is the same 72.XXXX.
Confirmed match
Since WG is sensitive to what the external IP address is, here is a pile of very confusing and conflicting info on what my external IP address is:
- OWRT / Status / Overview: 72.212.x.y
- OWRT / Services / Dynamic DNS: 104.21.a.b172.67.c.d
- this is populated by myddns_ipv4 service, running on OWRT, connected to a cloudflare.com service
- ping mydomain.com: replies from 172.67.c.d
- whatismyip.com: 72.212.x.y
- ISP modem: 68.104.e.f
I am struggling to connect all those dots. My suspicion is this confusing picture is contributing to my WG connection issues.
It's pretty simple -- wireguard is working, but the ddns service has an incorrect (old?) IP address for your OpenWrt endpoint.
This is obviously wrong.
this doesn't make sense either.
Try forcing your dynamic dns client to update the record.
I used this tutorial on GL-MT6000 it works on wrt1900acs v2 it doesn't work
At this point, I have success. I am able to connect from peers outside my home network.
By and large, I have circled back to the configuration I had in the initial post. Key differences:
- found and neutered the ISP router of which I was unaware, by placing it into bridge mode
- discovered that my DDNS setup is flawed, and relying on it was injecting other problems. I'll fix that later.
- discovered that my attempt to simulate a remote peer by connecting to a travel router in my home, was not really giving me the true remote-simulation I was going for, and that fact was masking other problems
Just as a reset and completeness, here are the dumps of the relevant config files:
edited to capture final tweaks / comments in later posts
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda3:0542:98ba::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'wan'
option macaddr '16:91:82:28:da:2b'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'wg0'
option proto 'wireguard'
option private_key 'redacted'
option listen_port '51820'
list addresses '192.168.9.1/24'
config wireguard_wg0
option description 'Surface Pro'
option public_key 'v7DLLH8XE9V+JtCUxulrlVHVEX8lCfrw8gs2AHKoAgA='
option private_key 'redacted'
list allowed_ips '192.168.9.2/32'
option route_allowed_ips '1'
config wireguard_wg0
option description 'Note20'
option public_key 'CNR+W3Iefkb1uAckgDu7xTpWojK+P+YyWrbJmhrATFA='
option private_key 'redacted'
option preshared_key 'redacted'
option route_allowed_ips '1'
list allowed_ips '192.168.9.3/32'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
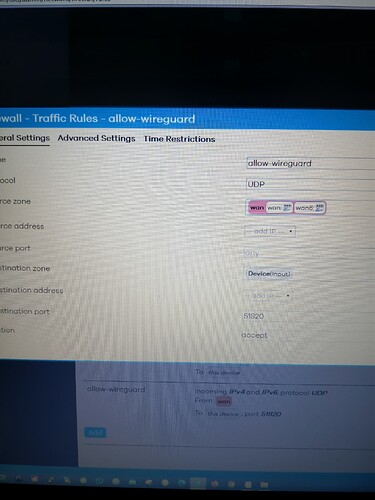
option name 'Allow-Wireguard'
list proto 'udp'
option src 'wan'
option target 'ACCEPT'
option dest_port '51820'
I hope that the keys have been obfuscated in some way -- if you've just used your actual keys, please destroy those keys and generate new ones because they should be considered compromised now that they've been exposed to the internet.
That said, I maintain that you should be using a rule, not a redirect. Delete this:
and add this:
config rule
option name 'Allow-WireGuard'
list proto 'udp'
option src 'wan'
option src_port '51820'
option target 'ACCEPT'
Then restart your router. It should work.
Thanks advice. Yeah I copy pasted the entire keys, I edited them, but they were exposed for a few minutes.
To your main point - it was dropping the traffic rule and adding back the port forward redirect that finally got things working. That's the part that flies in the face of the advice received today.
I'll put it back and reboot and see.
I just confirmed that dropping the redirect and adding the rule breaks it.
How are you testing? From inside (i.e. on the lan) or outside (i.e. cellular) your network?
oh... my bad... typo... source port should be destination port
config rule
option name 'Allow-WireGuard'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
Try that. Sorry for the mixup.
Boom! That fixed it. I've dropped that port forward and added the traffic rule.
It's worth noting that a LOT of the online tutorials on this topic, written or on YouTube, set it up with the port forward.
Since they both work, can you say more about why the traffic rule is the better solution than the port forward? I suspect it has to do with the "right" way to treat interfaces and zones, and my mind is still fuzzy on those topics.
The port forward is intended for the situation where you are forwarding the inbound traffic to another device, whereas the traffic rule is for local (i.e. the router itself).
If you ever change your lan IP address, the port forward rule would fail. But the traffic rule will always work.
Awesome. I really appreciate your truly valuable insights today!
Now to fix my borked DDNS....
@oli you are posting to an already solved thread.
If you have questions about setting up WireGuard, I suggest you start a new thread with your configuration and your questions
Ooooo, I missed this yesterday in the flurry, but that's a great idea, thanks!