Dear all,
I am seeking your help after several hours trying to get my wireguard server working. I followed several guides and digging into other posts but nothing helped me.
Please see here my configuration:
WireGuard section of /etc/config/network on 'server':
config interface 'wg0'
option proto 'wireguard'
option private_key 'YMW*********kW8='
option listen_port '51820'
list addresses '10.200.200.1/24'
option force_link '1'
config wireguard_wg0
option description 'iphone14'
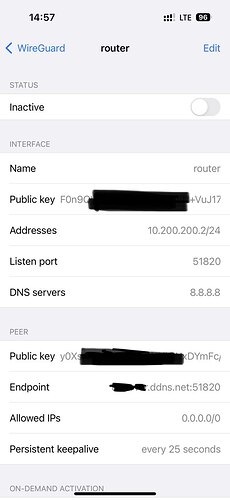
option public_key 'F0n9QW*********WBy+Dgo='
option private_key '8M2YBn*********ROHw9Vc='
option route_allowed_ips '1'
option endpoint_host 'server.ddns.net'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.200.200.2/32'
WireGuard section of /etc/config/firewall
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
And my iPhone wireguard client is:
Some troubleshooting:
wg show:
interface: wg0
public key: y0X****N/4RQ=
private key: (hidden)
listening port: 51820
peer: F0n9QW**y+Dgo=
endpoint: 37.185.249.61:47396
allowed ips: 10.200.200.2/32
latest handshake: 2 minutes, 55 seconds ago
transfer: 39.53 KiB received, 6.16 KiB sent
persistent keepalive: every 25 seconds
Tcpdump:
root@OpenWrt:~# tcpdump -i any -vvn udp port 51820
tcpdump: listening on any, link-type LINUX_SLL (Linux cooked v1), capture size 262144 bytes
15:00:59.188677 IP (tos 0x0, ttl 51, id 13693, offset 0, flags [none], proto UDP (17), length 176)
37.185.249.61.47396 > 192.168.7.1.51820: [udp sum ok] UDP, length 148
15:00:59.188677 IP (tos 0x0, ttl 51, id 13693, offset 0, flags [none], proto UDP (17), length 176)
37.185.249.61.47396 > 192.168.7.1.51820: [udp sum ok] UDP, length 148
15:00:59.199831 IP (tos 0x88, ttl 64, id 51483, offset 0, flags [none], proto UDP (17), length 120)
192.168.7.48.51820 > 37.185.249.61.47396: [udp sum ok] UDP, length 92
Thanks in advance, looking forward to hearing from you.
T