You can hijack the unencrypted dns queries tcpudp/53 and then you can forward the queries to some DoT or DoH, if that is what you ask me.
Sorry @trendy I have not been so clear.
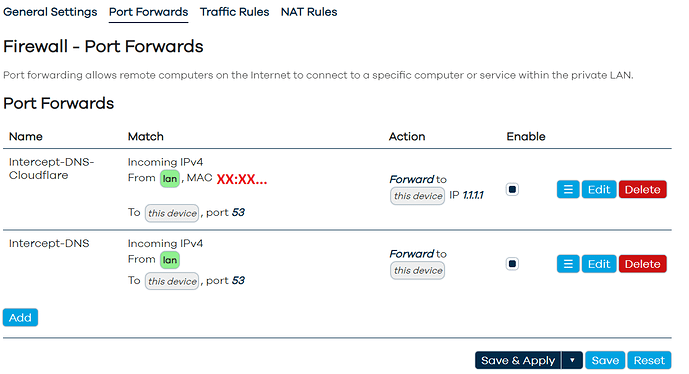
At present I have DNS hijacking setup such that by default everything goes to the DNS server IP I have set in WAN (CleanBrowsing), but that requests from certain MAC addresses instead go to an alternative DNS server IP (CloudFlare):
Is it possible to keep this setup, but such that for both types of DNS requests they are sent via stubby (to either CloudFlare or CleanBrowsing in accordance with my rules)? Would this potentially require two instances of stubby, one setup with CleanBrowsing and one setup with CloudFlare? And then for my DNS hijacking forward rules they are sent to either stubby instance address?
Because if I understand correctly, stubby is set to use one DNS provider.
Multiple stubby instances seems a bit messy though.
The alternative is to route CleanBrowsing and CloudFlare through VPN, but I found that problematic because Prime and Netflix complained about proxy/vpn use.
I suppose a compromise would be to just use stubby for the normal stuff and let the CloudFlare through stuff for Netflix and Prime through as normal DNS?
there is bit of an easier way. Setup AdGuardHome and then setup the clients to use different dns upstreams. Bonus is you also get adfiltering too. Assigning different DNS for different clients allows different filtering as well. (eg kids get safe search. adults dont)
I have DNS hijacking on port 53 to redirect to my AGH to stop devices on my network bypassing the blocking. (some IOT and other devices have hardcoded DNS servers and this forces them to go via my AGH)
Thank you for this suggestion @mercygroundabyss. I am not sure what to make of ad filtering as the last time I tried it on an Asus Merlin router random stuff didn't work so well and so it ended up feeling like more trouble than it is worth. I wonder if you have experienced that a little or not at all?
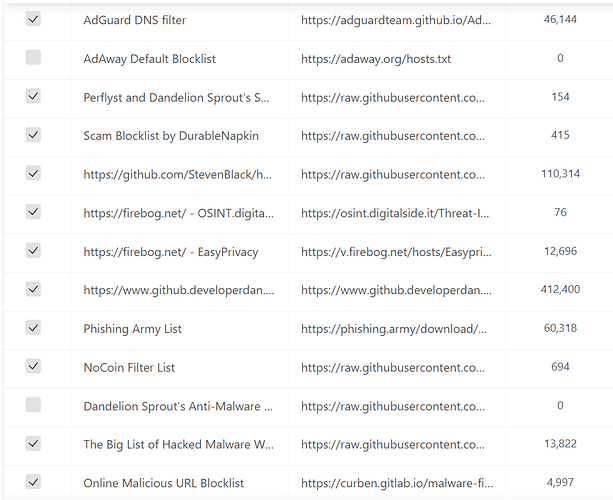
filtering pretty much depends on what lists you use. you can throw in loads or just start simple. The basic lists that AGH include are reasonably good. (i dont enable the Dandelion Sprout's Anti-Malware list but their smart tv one is good) If you use shopping referral links then you will need to whitelist them or use a list that will do that for you. Another thing to think about is your router resources.
I'm using roughly 660k of filters. But i am using that on an R4S with 4gb of ram. My old BT Hub5 managed about 120k before it ran out of ram (128mb) so you have to be selective.
Whitelists - https://github.com/anudeepND/whitelist he has some referral link ones too
Blocklists
https://github.com/StevenBlack/hosts - his is the key one i use and is in AGH by default.
https://firebog.net/ - have a few lists i use too. Easy Privacy and the OSINT lists.
Start small and add more as you see fit. I essentially run a main blocklist and then have separate "hostile" lists, confirmed malware servers, hacked servers etc. blocking them helps keep your network safe.
There are some who use PiHoles with 4mil plus filters... That is in my view somewhat excessive.
Perhaps you think my blocklist is excessive too. lol
My list targets not just ads, spams, scams, and malicious domains... but also pornography as well.
It's 3,000,000+ domains and growing. I do remove certain problematic-to-block domains though.
CleanBrowsing Family filter deals with that very well.
CleanBrowsing is a DNS service run by other people (and therefore not in your control).
My list can be downloaded and edited by anyone for their own use (which puts the control in their hands)... of course they can just use it "as is" also.
PiHole's are great because you can customize which lists you use. ![]()
You can hijack them to dnsmasq and then forward them to stubby, which will forward them to some other resolver.
You'd probably need 2 instances and you'll divert the traffic accordingly to the right stubby resolver.
To be clear DoT and DoH don't use the same port (53/udp).
So you can hijack all clients using cleartext 53/udp and allow OpenWrt to use DoT or DoH - with all other enabled clients using DoT/DoH on thier own.
Basically: your firewall setting for 53/udp will not cause a port conflict for DoT/DoH requests to go as normal.
Gotcha, and if I want to conditionally forward to different DoT servers I need multiple instances of stubby I think? I this something that is easy to setup I wonder?
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.