Finally official support, handsome!
Do you think this firmware will work on the ASUS RT-AC3100? My understanding is they are the same router except the AC3100 only has 5 ethernet ports.
RT-AC3100, RT-AC88U and RT-AC88R models are the same product with slight differences. AFAIK, RT-AC3100 doesn't include the realtek switch and has a few cosmetic differences. GPIO structure for LEDs, buttons and USB power might be different too.
I'm not sure whether the image would work. If you have an RT-AC3100, let me know. I can write the devicetree for it.
I just tried it. It flashes and reboots, but never boots. I can ping it, but can not access it via http. I have a RT-AC3100, what do you need from me to write the devicetree? Thanks.
Alright, let's make a speedrun of new device support. First of all, snapshot doesn't include luci so try SSH instead. If that doesn't work too, I'll send you a test image.
My bad, I should have tried ssh. This is my first time using openwrt and assumed luci was installed. I am able to ssh and I was able to install luci. I normally use VyOS, but am sick of running it as a VM. It looks like I can start playing around with it now. I will let you know if I find anything strange. Thanks for you help.
Make sure the buttons, LEDs and USB work as intended. It will still need its own devicetree for proper support.
22.03.0-rc4 stable release is up for RT-AC88U. Download link is on the device page. Stable releases include LuCI by default.
Unfortunately I shelved my RT-AC88U. 5Ghz radio is definetilvey dead (most probably a harware issue since it does not work with sotck firmware as well).
does it support both radios?
It does yes
This is awesome news. I will give the rc version a try when I am home next week.
Everything except VLANs seems to work in OpenWrt 22.03.0-rc4. I will revert back to 21.02.2.
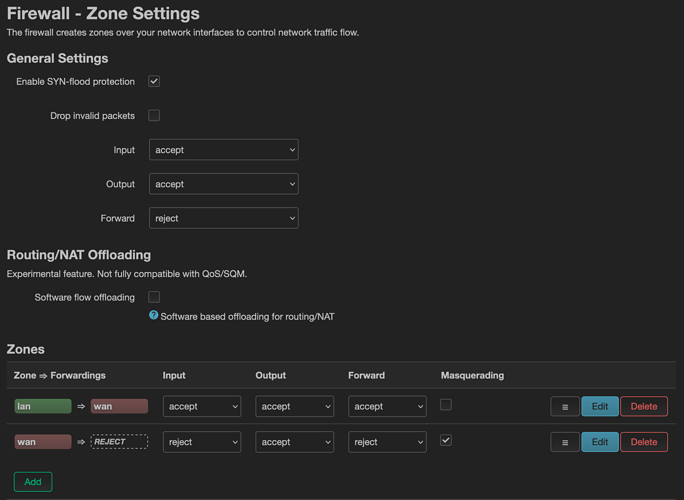
I finally have some spare time to mess around. I'd like to reproduce your issue. Can you send your config and screenshots from the interfaces, firewall and the bridge VLAN filtering page?
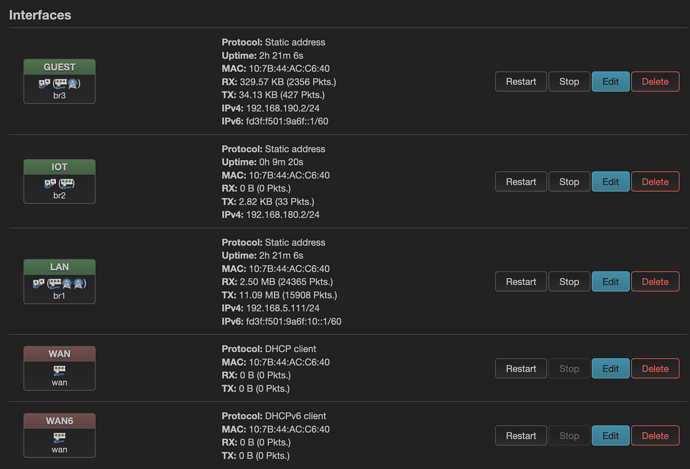
Sure, no problem at all. Network IoT is not used at present, so just ignore it. DHCP services for clients of the different networks come from external Server (OPNsense), which operates as gateway and DNS server.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd3f:f501:9a6f::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
option igmp_snooping '1'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1:u*'
list ports 'lan2'
config brigde-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan1:t'
list ports 'lan4'
config bridge-vlan
option device 'br-lan'
option vlan '3'
list ports 'lan1:t'
list ports 'lan3'
config device
option type 'bridge'
option name 'br1'
list ports 'br-lan.1'
option igmp_snooping '1'
config device
option type 'bridge'
option name 'br2'
list ports 'br-lan.2'
option igmp_snooping '1'
config device
option type 'bridge'
option name 'br3'
list ports 'br-lan.3'
option igmp_snooping '1'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.5.111'
option gateway '192.168.5.1'
option broadcast '192.168.5.255'
list dns '192.168.5.1'
option device 'br1'
option metric '50'
config interface 'iot'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.180.2'
option gateway '192.168.180.1'
option broadcast '192.168.180.255'
list dns '192.168.180.1'
option device 'br2'
option metric '100'
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.190.2'
option gateway '192.168.190.1'
option broadcast '192.168.190.255'
list dns '192.168.190.1'
option device 'br3'
option metric '150'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config device
option type '8021q'
option ifname 'br-lan'
option vid '2'
option name 'br-lan.2'
config device
option name 'br-lan.1'
option type '8021q'
option ifname 'br-lan'
option vid '1'
config device
option name 'br-lan.3'
option type '8021q'
option ifname 'br-lan'
option vid '3'
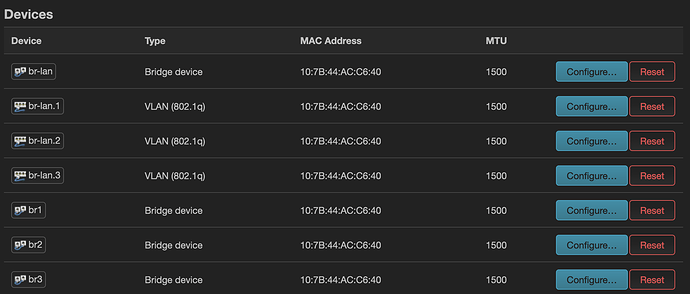
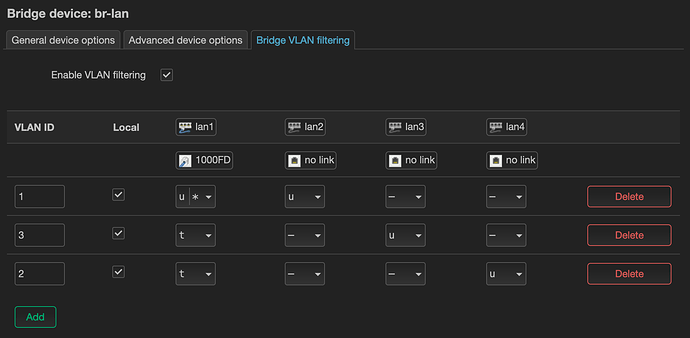
Hmm, ok. If I remember correctly, there were some problems with adding the WiFi interfaces to a bridge with VLAN filtering enabled. So this is why you have created new bridges, br1 and br3, with VLAN filtering off, correct? Other than that, this setup is pretty simple, remind me what does not work on versions newer than 21.02?
Yes, you are right, br1 and br3 were created due to Wifi issues with vlans. And yes apart from that the router is only a plain access point. With kernel versions >5.4 I had no luck. As you advised me I filed that issue as a bug. But till today it is still open, yet it was flagged with "kernel".
I'm currently replicating your network setup, why do lan and guest networks both have the gateway specified? You're supposed to put only one default route to a router and that is if you want the router to route all IP(v4) addresses through the host (router) that has got the specified IP address on that network.
Same goes for DNS. Though not a necessity, you should specify a single DNS server. Don't specify a different DNS server on each network. The router sends queries to that DNS server for traffic only from the router itself since the router only works as an AP, meaning it only switches frames between hosts.
What I'm going to say next might differ by your use case, instead of changing the DNS server on the router, you can configure it on dnsmasq running on the router so you have dnsmasq locally caching queries as well. Just put the desired DNS server on the "DNS forwarding" section under "Network -> DHCP and DNS" on LuCI.
And please send Nevermind, if this device acts as an AP you must not have configured DHCP at all./etc/config/dhcp.
First of all, thank you very much for your ongoing efforts on my problem and your valuable advice. I agree with you that my approach is not very common, even a bit strange. The main goals were to keep the configuration of the APs as simple as possible and to make the clients of the VLAN feel like they were in a simple network structure.
I did this mainly because of the IoT VLAN configured on the other APs, because those devices always collect whatever data they can get there. Firewalling helps a bit, but in the end you have to let them communicate or you won't be comfortable. If a replacement is economically feasible, I will definitely go with a cloud-free solution.
Of course, I could transfer a bit of intelligence to the Asus router. However, I don't see the big advantage, since the Asus router is connected to the OPNsense server via cable without VPNs or other narrow-band connections in between.
Cheers. Putting multiple default routes makes no sense in any sort of networking structure. Netifd (the network interface daemon OpenWrt uses) is going to bring the interfaces up, one by one, by retrieving information from /etc/config/network. Only the default route on the last interface brought up will stick. So, the ones before won't even have an impact on the router. You can confirm this by running ip route.
Although this likely has nothing to do with the problem at hand, it still is a huge discrepancy that you should address. Because this may cause all sorts of issues on different OpenWrt versions (21.02 vs 22.03). You can just keep the one for the OPNsense server (192.168.5.1) as I suppose is the upstream router in your case. This way, the Asus router will have internet access.
I have no idea what you're pointing at on the second and third paragraphs.
I'm going to set up the guest network (192.168.190.0/24) and try to connect to it via Wi-Fi and see if I get DHCP to give me an IP address.
My PC will be connected to lan1, the interface on the PC will be eth0.1 (VLAN ID 1 tagged interface) and will set 192.168.190.1/24 on it. DHCP will listen on that interface. That should completely replicate your guest network.
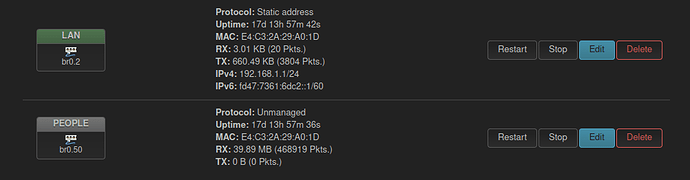
One more thing you can do to simplify your networking setup is to set the protocol on the guest network on the Asus router to unmanaged, you don't need the router to have an IP address on the guest network as all it does is switch frames between the WLAN and DSA interfaces. And you already have an IP address on LAN to reach the router.
This is how my AP (TP-Link, WiFi bridge issue is nonexistent) with guest network works. There's a WLAN interface on br0 set to VLAN 50 untagged, but LuCI doesn't show that on the page.