I really like the very simple pbr based approach I described above. You just set up the routing table names, then assign those to the interfaces, then set up rules to direct traffic based on source IP to either VPN or wan. You can set up VPN to wan failover and VPN exceptions based on source IP.
I would like to try your solution but I have a couple questions. Thanks.
First is all I have to do for the table part is add a WAN and VPN like you did here under local? No additional routings?
root@OpenWrt:~# cat /etc/iproute2/rt_tables
reserved values
128 prelocal
255 local
254 main
253 default
0 unspec
local
#1 inr.ruhep
1 br-lan
2 br-guest
3 vpn
4 wan
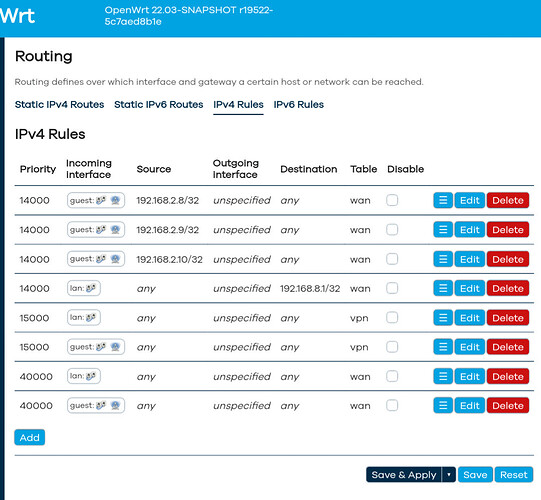
Second I cannot find this section anywhere on my router. Closest is a section called "Static Routes". I am guessing I am either missing and add-on or something has changed in the firmware over time?
Yes correct.
Which OpenWrt version do you have? @vgaetera which OpenWrt versions support the funky new IPv4 rules section you helped develop?
It looks like version OpenWrt 21.02.3 r16554-1d4dea6d4f / LuCI openwrt-21.02 branch git-22.083.69138-0a0ce2a
Does that use netifd?
If not would you consider upgrading to 22.03 snapshot branch?
22.03 release is around the corner.
I was able to locate the latest version I believe. Being new to OpenWRT I am assuming I just use the Sysupgrade download?
The big question I have is will this method you are proposing work with my double NAT setup? For example the traffic will start on my Omada system say 192.168.2.X and out that WAN into the OpenWRT LAN 192.168.1.1 and through the VPN out to the internet.
Yes if you are also OpenWrt installed you will do download sysupgrade ![]()
@Lynx you think the 22.03 is soon out ??
I am not very familiar with vlan setups but doesn't OpenWrt have visibility of the source IPs such that you can just specify e.g. that 192.168.2.0/24 is to go out through WAN just like in my example with 192.168.1.8/32 (television) to go out through WAN?
I think you might also just be able to use 'auc' using the appropriate switches:
auc -b 22.03 -B 22.03-SNAPSHOT
That's the latest snapshot build so slightly more up to date than rc5. @hnyman will this work ok for the OP here? Can he keep settings? Am I right about the VPN pbr working in this context?
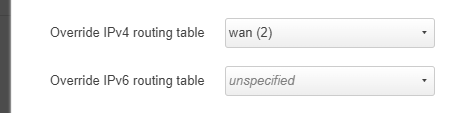
So I have the new version up and running with the Routing option now available. It seems to half work. I can route things through the VPN but when I tried to set the WAN IP4v4 Override and apply it crashes the router. Any suggestions for the WAN overide? Thanks.
I haven't had the chance to play with the 22.03 settings yet.
However there is an example in the Wiki.
@hartman44 hmm. So I really am not sure why you are seeing this crash. You shouldn't and beyond @trendy I don't know who else to ask. Are you able to output crash data to see what is happening by any chance? Sorry about this glitch, and I am sure we can get it fixed. Ultimately moving over to netifd is the way forward - so this pain now should pay dividends later.
I have been playing around with this technique and a couple of packages (VPN Bypass and Policy Based Routing). What I am noticing is what I feared. I don't think the OpenWRT router is recognizing the IP addresses from the traffic coming through from my Omada system.
Again my setup is like this:
ISP -> OpenWRT Router (192.168.1.1) running WireGuard -> TP-Link Omada Setup with VLANS i.e.192.168.0.X, 192.168.2.X, 192.168.3.X (ER605) (Managed Switch) and (EAPs)
As I am not well versed in networking any suggestions on how to pass these subnets through so OpenWRT and the policies based on these subnets is recognized?
Start for scratch.. again
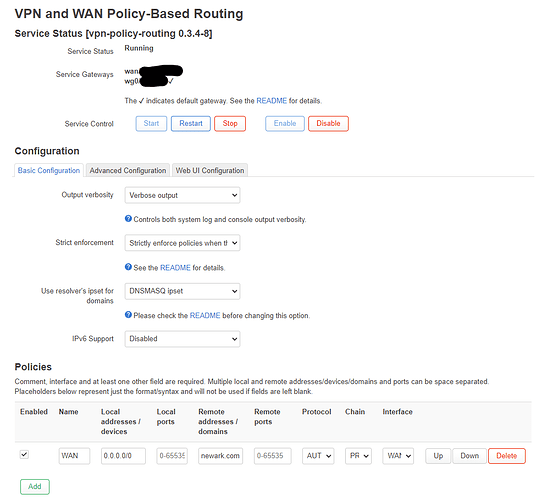
If the Wireguard client is not used as default routing and you create policies to selectively use the Wireguard client, make sure your settings are as following (three dots on the line imply other options can be listed in the section as well). Make sure that the policy mentioned below is at the top of your policies list.
The author has his own thread and is active. The ReadMe has troubleshooting tips and ways to push details to the project.
I can see that keeping the Omada untouched is a primary goal and that working on the WAN facing OpenWrt hardware is where you'd like to concentrate.
I just don't understand vlans well enough, but to me the simple LuCi netifd approach seems vastly preferable to the alternative vpn pbr solution.
Sadly not all tunnels are netifd compatible.
So here's a little update on my PBR adventure. After a complete factory reset and installation of 22.03 I am able to at least have a policy to reroute to the WAN from VPN on certain domains via all subnets with VPN being the default route. I still cannot get this to work based on a single IP address or subnet via "Local addresses / devices".
Maybe someone who is familiar with my type of setup can chime in with suggestions on how to get PBR to recognize my subnets behind the OpenWRT router. Thanks.
Again my setup is like this:
ISP -> OpenWRT Router (192.168.1.1) running WireGuard -> TP-Link Omada Setup with VLANS i.e.192.168.0.X, 192.168.2.X, 192.168.3.X (ER605) (Managed Switch) and (EAPs)
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option src_ipset '0'
option dest_ipset '0'
option resolver_ipset 'dnsmasq.ipset'
option ipv6_enabled '0'
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option webui_enable_column '1'
option webui_protocol_column '1'
option webui_chain_column '1'
option enabled '1'
config include
option path '/etc/vpn-policy-routing.netflix.user'
option enabled '0'
config include
option path '/etc/vpn-policy-routing.aws.user'
option enabled '0'
config policy
option interface 'wan'
option name 'WAN'
option src_addr '0.0.0.0/0'
option dest_addr 'newark.com www.kroger.com kroger.com heilind.com'
So I am still kind of struggling as PBRs domain name functions don't always seem to work and sites get blocked. I foresee I may need more split tunneling capabilities in the future and wanted to run this by everyone. Thanks.
What if I were to cascade my routers in the below fashion? Would it allow the IPs to be seen by OpenWRT? I think the only way for it to work would to turn off DHCP on the OpenWRT to allow Omada to set the IPs. What is the proper way to turn off DHCP in OpenWRT?
ISP -> (WAN port) OpenWRT Router (change IP to 192.168.0.1 turn off DHCP) running WireGuard -> (LAN port) TP-Link Omada Setup with VLANS i.e.(main Omada router 192.168.0.2/24), 192.168.2.X, 192.168.3.X (ER605) (Managed Switch) and (EAPs)
Hi @hartman44, i just came across this old topic of yours which caught my attention, as i am in the middle of researching implementing a similar setup, and I have a feeling your setup might be exactly what I was about to settle on.
I am have been using omada for some time due to the ease of the multiwan setup - and i have also been playing with GLI-net routers for their privacy and vpn feaures. The plan was to do something like ISP 1 + ISP 2 -> Omada multiwan -> GLI Brume 2 gateway -> omada switch/ap/clients etc. The reason, simply, to add network level PIA Wireguard and also run a wireguard server for remote access (which i was planing to connect to with gli travel routers where needed).
Is this similar to your current setup and requirements? if so, im keen to know if you managed to get this working and if you have any other advice.