Hi, I have a working ipsec tunnel between openwrt and fritzbox with ipsec.
This was quite easy to setup.
This is Konfiguration:
root@OpenWrt:/etc/config# opkg update
root@OpenWrt:~# opkg install strongswan-default
root@OpenWrt:~# opkg install strongswan-mod-kernel-libipsec
VPN File for Fritzbox
vpncfg {
connections {
enabled = yes;
conn_type = conntype_lan;
name = "VOIP01 Heidkamp VPN";
always_renew = yes;
reject_not_encrypted = no;
dont_filter_netbios = yes;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remoteip = 0.0.0.0;
remote_virtualip = 0.0.0.0;
remotehostname = "voip01.profi-itservice.de";
localid {
fqdn = "fritzbox.barthelmes-architekten.de";
}
remoteid {
fqdn = "voip01.profi-itservice.de";
}
mode = phase1_mode_aggressive;
phase1ss = "dh14/aes/sha";
keytype = connkeytype_pre_shared;
key = "XXXXXXXXXXXXXXXXX";
cert_do_server_auth = no;
use_nat_t = yes;
use_xauth = no;
use_cfgmode = no;
phase2localid {
ipnet {
ipaddr = 192.168.51.0;
mask = 255.255.255.0;
}
}
phase2remoteid {
ipnet {
ipaddr = 192.168.134.0;
mask = 255.255.255.0;
}
}
phase2ss = "esp-all-all/ah-none/comp-all/pfs";
accesslist = "permit ip any 192.168.134.0 255.255.255.0";
}
ike_forward_rules = "udp 0.0.0.0:500 0.0.0.0:500",
"udp 0.0.0.0:4500 0.0.0.0:4500";
}
/etc/ipsec.conf
# basic configuration
version 2
config setup
#charondebug="dmn 0, mgr 0, ike 0, chd 0, job 0, cfg 0, knl 0, net 0, asn 0, enc 0, lib 0, esp 0, tls 0, tnc 0, imc 0, imv 0, pts 0"
charondebug="ike 2, knl 0, cfg 0"
conn %default
keyingtries=%forever
conn Barthelmes
left=voip01.profi-itservice.de
leftsubnet=192.168.134.0/24
leftfirewall=yes
lefthostaccess=yes
right=fritzbox.barthelmes-architekten.de
rightsubnet=192.168.51.0/24
rightallowany=yes
leftid="@openwrt.XXXXXXX.de"
leftauth=psk
rightid="@fritzbox.XXXXXXX.de"
rightauth=psk
ike=aes192-sha1-modp2048!
esp=aes192-sha1-modp2048!
keyexchange=ikev1
aggressive=no
#ikelifetime=1h
#margintime=9m
#rekey=yes
#reauth=yes
#keylife=8h
#compress=yes
#dpddelay=30
#dpdtimeout=60
dpdaction=none
authby=secret
auto=start
/etc/init.d/ipsec start
root@OpenWrt:/etc# logread -f
Wed Sep 29 23:03:20 2021 daemon.info : 17[IKE] sending retransmit 1 of request message ID 0, seq 2
Wed Sep 29 23:03:20 2021 daemon.info : 17[NET] sending packet: from 87.123.61.80[500] to 188.96.3.22[500] (372 bytes)
Wed Sep 29 23:03:21 2021 daemon.info : 10[NET] received packet: from 188.96.3.22[500] to 87.123.61.80[500] (356 bytes)
Wed Sep 29 23:03:21 2021 daemon.info : 10[ENC] parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
Wed Sep 29 23:03:22 2021 daemon.info : 10[IKE] faking NAT situation to enforce UDP encapsulation
Wed Sep 29 23:03:22 2021 daemon.info : 10[IKE] reinitiating already active tasks
Wed Sep 29 23:03:22 2021 daemon.info : 10[IKE] ISAKMP_VENDOR task
Wed Sep 29 23:03:22 2021 daemon.info : 10[IKE] MAIN_MODE task
Wed Sep 29 23:03:22 2021 daemon.info : 10[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
Wed Sep 29 23:03:22 2021 daemon.info : 10[NET] sending packet: from 87.123.61.80[4500] to 188.96.3.22[4500] (124 bytes)
Wed Sep 29 23:03:22 2021 daemon.info : 11[NET] received packet: from 188.96.3.22[4500] to 87.123.61.80[4500] (108 bytes)
Wed Sep 29 23:03:22 2021 daemon.info : 11[ENC] parsed ID_PROT response 0 [ ID HASH ]
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] IKE_SA Barthelmes[1] established between 87.123.61.80[openwrt.xxxxxxxx.de]...188.96.3.22[fritzbox.XXXXXXXXX.de]
Wed Sep 29 23:03:22 2021 authpriv.info : 11[IKE] IKE_SA Barthelmes[1] established between 87.123.61.80[openwrt.XXXXXX.de]...188.96.3.22[fritzbox.XXXXXXXXXX.de]
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] IKE_SA Barthelmes[1] state change: CONNECTING => ESTABLISHED
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] scheduling reauthentication in 9862s
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] maximum IKE_SA lifetime 10402s
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] activating new tasks
Wed Sep 29 23:03:22 2021 daemon.info : 11[IKE] activating QUICK_MODE task
Wed Sep 29 23:03:23 2021 daemon.info : 11[ENC] generating QUICK_MODE request 1664917690 [ HASH SA No KE ID ID ]
Wed Sep 29 23:03:23 2021 daemon.info : 11[NET] sending packet: from 87.123.61.80[4500] to 188.96.3.22[4500] (444 bytes)
Wed Sep 29 23:03:27 2021 daemon.info : 14[IKE] sending retransmit 1 of request message ID 1664917690, seq 4
Wed Sep 29 23:03:27 2021 daemon.info : 14[NET] sending packet: from 87.123.61.80[4500] to 188.96.3.22[4500] (444 bytes)
Wed Sep 29 23:03:28 2021 daemon.info : 15[NET] received packet: from 188.96.3.22[4500] to 87.123.61.80[4500] (428 bytes)
Wed Sep 29 23:03:28 2021 daemon.info : 15[ENC] parsed QUICK_MODE response 1664917690 [ HASH SA No KE ID ID ]
Wed Sep 29 23:03:29 2021 daemon.info : 15[IKE] CHILD_SA Barthelmes{1} established with SPIs c1165f74_i 87325a2d_o and TS 192.168.134.0/24 === 192.168.51.0/24
Wed Sep 29 23:03:29 2021 authpriv.info : 15[IKE] CHILD_SA Barthelmes{1} established with SPIs c1165f74_i 87325a2d_o and TS 192.168.134.0/24 === 192.168.51.0/24
Wed Sep 29 23:03:29 2021 local0.notice vpn: + fritzbox.XXXXXXXXXX.de 192.168.51.0/24 == 188.96.3.22 -- 87.123.61.80 == 192.168.134.0/24
Wed Sep 29 23:03:29 2021 daemon.info : 15[IKE] reinitiating already active tasks
Wed Sep 29 23:03:29 2021 daemon.info : 15[IKE] QUICK_MODE task
Wed Sep 29 23:03:29 2021 daemon.info : 15[ENC] generating QUICK_MODE request 1664917690 [ HASH ]
Wed Sep 29 23:03:29 2021 daemon.info : 15[NET] sending packet: from 87.123.61.80[4500] to 188.96.3.22[4500] (60 bytes)
Wed Sep 29 23:03:29 2021 daemon.info : 15[IKE] activating new tasks
Wed Sep 29 23:03:29 2021 daemon.info : 15[IKE] nothing to initiate
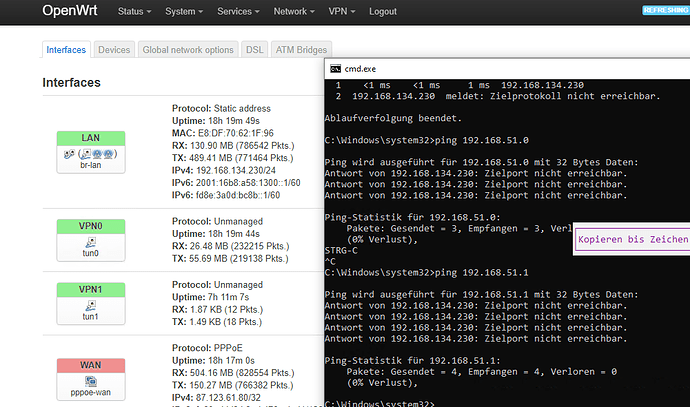
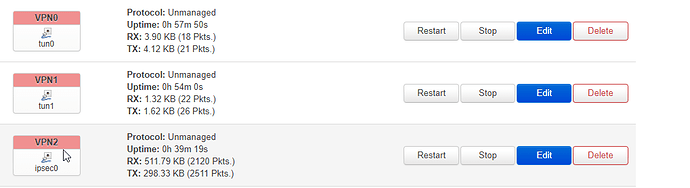
OK the tunnel is up and both sites are available.
check by ping from my openwrt box.
root@OpenWrt:/etc# ^C
root@OpenWrt:/etc# ping 192.168.51.1
PING 192.168.51.1 (192.168.51.1): 56 data bytes
64 bytes from 192.168.51.1: seq=0 ttl=63 time=35.128 ms
64 bytes from 192.168.51.1: seq=1 ttl=63 time=32.652 ms
64 bytes from 192.168.51.1: seq=2 ttl=63 time=35.646 ms
64 bytes from 192.168.51.1: seq=3 ttl=63 time=33.163 ms
^C
--- 192.168.51.1 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 32.652/34.147/35.646 ms
root@OpenWrt:/etc#
And ifconfig shows my interface
ipsec0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet6 addr: fe80::525e:6b41:79d2:fc1/64 Scope:Link
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1400 Metric:1
RX packets:11 errors:0 dropped:0 overruns:0 frame:0
TX packets:15 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:924 (924.0 B) TX bytes:1228 (1.1 KiB)
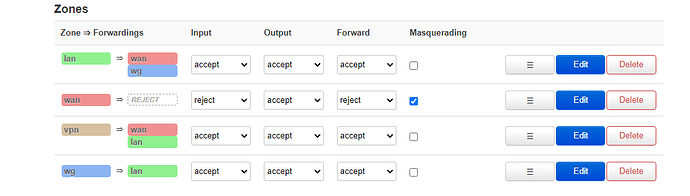
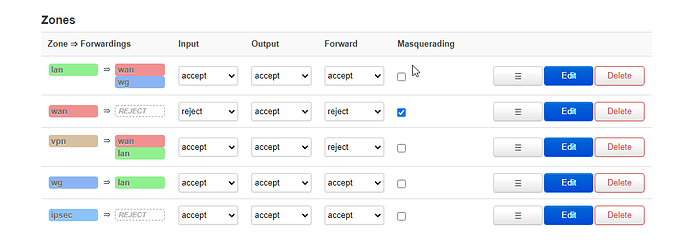
Now to my question:
from my Internal LAN 192.168.134.0/24 I am not able to ping to remote side 192.168.51.0/24.
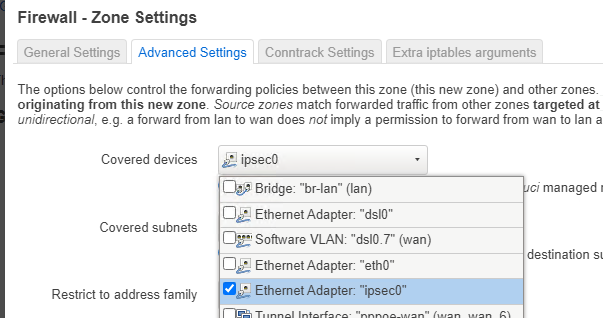
So I have to do the following:
a.