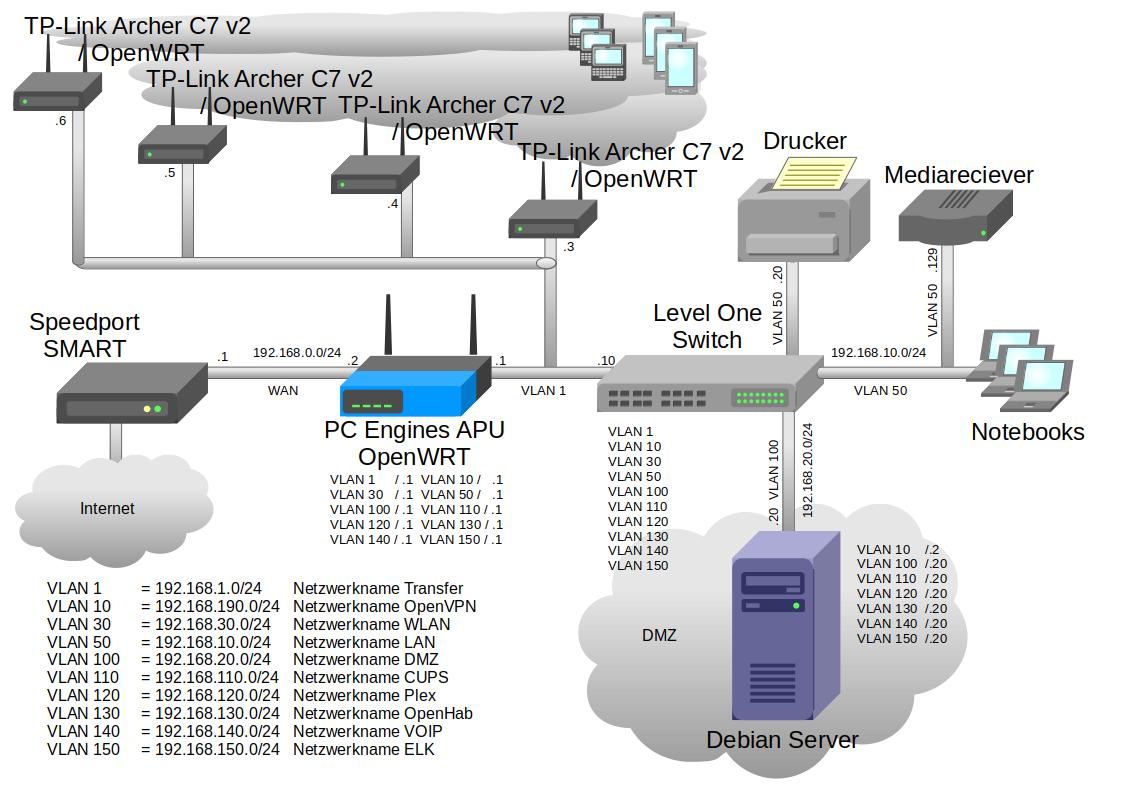
Hello,
after I set the firewall zone OpenVPN / input to reject on my central OpenWRT router (IP 192.168.1.1). I am facing a strange problem. But first, more about my network topology:
I'm building an OpenVPN tunnel into my network from a smartphone. My smartphone and OpenVPN server have the following IP addresses: Smartphone: sgsthtme01 = 192.168.190.65 OpenVPN-Server: dstme01 = 192.168.190.2 My OpenVPN server is bonded to the switch. The OpenVPN server has the following network settings:
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
# allow-hotplug eth0
# auto eth0
iface eth0 inet manual
# The scondery network interface
# allow-hotplug eth1
# auto eth1
iface eth1 inet manual
# The thirty network interface
# allow-hotplug eth2
# auto eth2
iface eth2 inet manual
# The bond dmz network interface
auto bond0
iface bond0 inet static
address 192.168.20.20
netmask 255.255.255.0
network 192.168.20.0
gateway 192.168.20.1
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
slaves eth1 eth2
bond_mode 802.3ad
bond_miimon 100
bond_downdelay 200
bond_updelay 200
up ip addr add 192.168.20.25 brd + dev bond0
up ip addr add 192.168.20.26 brd + dev bond0
up ip addr add 192.168.20.28 brd + dev bond0
up ip addr add 192.168.20.30 brd + dev bond0
# The bond cups network
auto bond0.110
iface bond0.110 inet static
address 192.168.110.20
netmask 255.255.255.0
network 192.168.110.0
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
# The bond plex network
auto bond0.120
iface bond0.120 inet static
address 192.168.120.20
netmask 255.255.255.0
network 192.168.120.0
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
# The bond openhub network
auto bond0.130
iface bond0.130 inet static
address 192.168.130.20
netmask 255.255.255.0
network 192.168.130.0
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
# The bond voip network
auto bond0.140
iface bond0.140 inet static
address 192.168.140.20
netmask 255.255.255.0
network 192.168.140.0
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
# The bond elk network
auto bond0.150
iface bond0.150 inet static
address 192.168.150.20
netmask 255.255.255.0
network 192.168.150.0
dns-search intern.harnet.de
dns-nameservers 192.168.20.20
# The bond openvpn network
auto bond0.10
iface bond0.10 inet manual
up ip link set $IFACE up promisc on
down ip link set $IFACE down promisc off
The OpenVPN connection is established via the TAP interface. The up script looks like this:
#################################
# Set up Ethernet bridge on Linux
# Requires: bridge-utils
#################################
# Define Bridge Interface
br="br0"
# Define list of TAP interfaces to be bridged,
# for example tap="tap0 tap1 tap2".
tap="tap0"
# Define physical ethernet interface to be bridged
# with TAP interface(s) above.
eth="bond0.10"
eth_ip="192.168.190.2"
eth_netmask="255.255.255.0"
eth_gateway="192.168.190.1"
eth_broadcast="192.168.190.255"
for t in $tap; do
openvpn --mktun --dev $t
done
brctl addbr $br
brctl addif $br $eth
for t in $tap; do
brctl addif $br $t
done
for t in $tap; do
ifconfig $t 0.0.0.0 promisc up
done
ifconfig $eth 0.0.0.0 promisc up
ifconfig $br $eth_ip netmask $eth_netmask broadcast $eth_broadcast
I will also post the routes from my central router:
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 192.168.0.1 0.0.0.0 UG 0 0 0 eth2
192.168.0.0 * 255.255.255.248 U 0 0 0 eth2
192.168.1.0 * 255.255.255.0 U 0 0 0 eth0.1
192.168.10.0 * 255.255.255.0 U 0 0 0 eth0.50
192.168.20.0 * 255.255.255.0 U 0 0 0 eth0.100
192.168.30.0 * 255.255.255.0 U 0 0 0 br-wlan
192.168.110.0 * 255.255.255.0 U 0 0 0 eth0.110
192.168.120.0 * 255.255.255.0 U 0 0 0 eth0.120
192.168.130.0 * 255.255.255.0 U 0 0 0 eth0.130
192.168.140.0 * 255.255.255.0 U 0 0 0 eth0.140
192.168.150.0 * 255.255.255.0 U 0 0 0 eth0.150
192.168.190.0 * 255.255.255.0 U 0 0 0 eth0.10
And my network settings:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd11:971c:e6b2::/48'
config interface 'dmz'
option proto 'static'
option ifname 'eth0.100'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config interface 'wlan'
option proto 'static'
option ipaddr '192.168.30.1'
option netmask '255.255.255.0'
option type 'bridge'
option _orig_ifname 'wlan wlan0 wlan3'
option _orig_bridge 'true'
option ifname 'eth0.30'
config interface 'lan'
option proto 'static'
option ifname 'eth0.50'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
config interface 'transfer'
option proto 'static'
option ifname 'eth0.1'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'static'
option ifname 'eth2'
option ipaddr '192.168.0.2'
option netmask '255.255.255.248'
option gateway '192.168.0.1'
config interface 'openvpn'
option proto 'static'
option ifname 'eth0.10'
option ipaddr '192.168.190.1'
option netmask '255.255.255.0'
config interface 'plex'
option proto 'static'
option ifname 'eth0.120'
option ipaddr '192.168.120.1'
option netmask '255.255.255.0'
option dns '192.168.20.20'
config interface 'cups'
option proto 'static'
option ifname 'eth0.110'
option netmask '255.255.255.0'
option dns '192.168.20.20'
option ipaddr '192.168.110.1'
config interface 'openhab'
option proto 'static'
option ifname 'eth0.130'
option netmask '255.255.255.0'
option ipaddr '192.168.130.1'
config interface 'VOIP'
option proto 'static'
option ifname 'eth0.140'
option netmask '255.255.255.0'
option ipaddr '192.168.140.1'
config interface 'elk'
option proto 'static'
option ifname 'eth0.150'
option ipaddr '192.168.150.1'
option netmask '255.255.255.0'
I have activated the following traffic rule so that I can access all routers in the transfer network (192.168.1.0/24) from the OpenVPN network via ICMP, SSH and HTTPS:
IPv4-ICMP mit type echo-request
Von beliebiger Rechner in openvpn
Zu beliebiger Rechner in transfer
Accept forward
IPv4-UDP
Von beliebiger Rechner in openvpn
Zu IP 192.168.20.20, port 68 in dmz
Accept forward
IPv4-TCP
Von beliebiger Rechner in openvpn
Zu IP 192.168.20.20, port 53 in dmz
Accept forward
IPv4-TCP
Von beliebiger Rechner in openvpn
Zu beliebiger Rechner, port 80 in transfer
Accept forward
IPv4-TCP
Von beliebiger Rechner in openvpn
Zu IP range 192.168.1.0/24, port 443 in transfer
Accept forward
IPv4-TCP
Von beliebiger Rechner in openvpn
Zu IP 192.168.140.20, port 5070 in voip
Accept forward
IPv4-TCP
Von beliebiger Rechner in openvpn
Zu IP range 192.168.1.0/24, port 8022 in transfer
Accept forward
IPv4-UDP
Von beliebiger Rechner in openvpn
Zu IP 192.168.140.20, ports 30000-30099 in voip
Accept forward
I can establish all communication relationships to the routers with the IP addresses 192.168.1.3/.5 and .6 via ICMP, SSH and HTTPS. Just not to my central router with the IP address 192.168.1.1. I do not know why? Does it have anything to do with ARP or bonding?
I would be very happy about your support. Greetings from SH