Hi everyone!
I experience weird issue I've never had before. I recently moved to a new place and recreated the setup I used for years without any problems, but facing the networking issue this time.
My setup is the following: Pfsense router (VLANS enabled) + OpenWRT Dummy Access Point (VLANS enabled). The devices are connected LAN-to-LAN and the DHCP provides the correct addresses from the defined scope. Internet Access is working.
VLANS: IOT, LAN, GUEST, DMZ. Wifi for each vlan. The issue is that the clients on LAN (192.168.20.0/24) have Internet access, but cannot discover each other, so my MacBookPro (192.168.20.20) cannot ping neither my MacPro (192.168.20.10) nor my Android phone (192.168.20.21)... And vice versa...
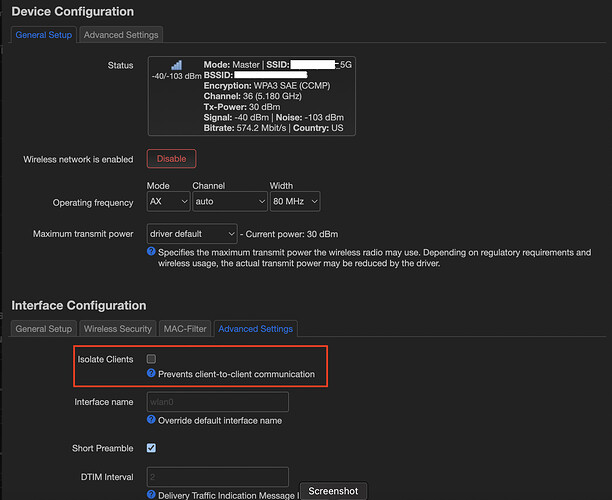
They seem to be isolated, but the "Isolate Clients" checkbox is not ticked:
The Firewall is disabled on the OpenWRT.
The Pfsense firewall at this point should not even matter as the traffic on the same subnet should not even touch the router, but in case you ask - it has "Allow all traffic" rule on LAN vlan.
The firewall on MacOS clients is Disabled too.
❯ sudo pfctl -d
No ALTQ support in kernel
ALTQ related functions disabled
pfctl: pf not enabled
Routing table on my laptop:
❯ ip r
default via 192.168.20.254 dev en0
127.0.0.0/8 via 127.0.0.1 dev lo0
127.0.0.1/32 via 127.0.0.1 dev lo0
169.254.0.0/16 dev en0 scope link
192.168.20.0/24 dev en0 scope link
192.168.20.20/32 dev en0 scope link
192.168.20.254/32 dev en0 scope link
224.0.0.0/4 dev en0 scope link
255.255.255.255/32 dev en0 scope link
So I guess 192.168.20.0/24 dev en0 scope link - is the route that must work in case of current inter-subnet communication.
Again, ICMP is not blocked, as client firewalls are disabled. I'm not a networking guy, so I thought, maybe it's some weird ICMP issue, so tried to check the TCP... I've enabled VNC and SSH on my Desktop(192.168.20.10) and scanned ports from this same machine on its LAN interface and all seems good:
❯ nmap -Pn -p5900,22 192.168.20.10
Starting Nmap 7.92 ( https://nmap.org ) at 2022-12-25 17:22 PST
Nmap scan report for desktop.home.lan (192.168.20.10)
Host is up (0.00040s latency).
PORT STATE SERVICE
22/tcp open ssh
5900/tcp open vnc
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds
But when scanning same Desktop's ports from my Laptop (192.168.20.20):
❯ nmap -Pn -p5900,22 192.168.20.10
Starting Nmap 7.93 ( https://nmap.org ) at 2022-12-25 17:53 PST
Nmap scan report for desktop.home.lan (192.168.20.10)
Host is up.
PORT STATE SERVICE
22/tcp filtered ssh
5900/tcp filtered vnc
Nmap done: 1 IP address (1 host up) scanned in 3.04 seconds
And my Android device (192.168.20.21) cannot ping both 192.168.20.20 and 192.168.20.10... At this point I am out of ideas, but I am almost sure there is something to do with the wireless connection on my OpenWRT AP... Just have not clue how to troubleshoot this... Please help. Thank you.