Hi there,
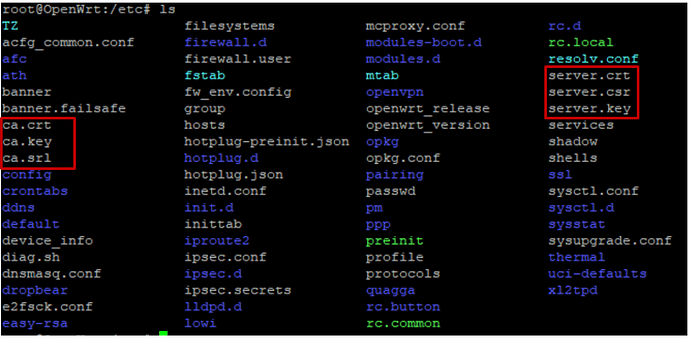
I have completed the steps according to the official website to configure https, generated the key and crt then put them to the corresponding location.
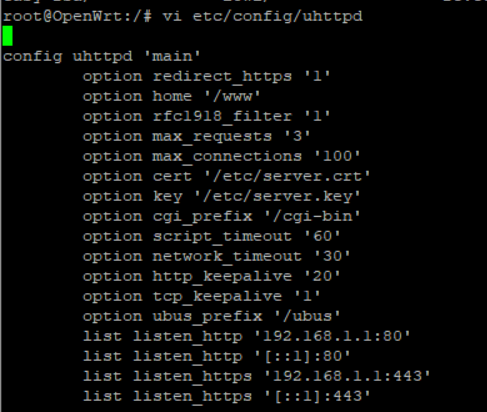
However , I can't connect https successfully. Below is the configure I set:
Please us the preformatted text option when posting configuration output.
Select the icon highlighted in red...
![]()
root@OpenWrt:/tmp# ubus call system board; \uci export firewall; head -n -0 /etc/firewall.user
{
"kernel": "4.4.60",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 4 (v7l)",
"model": "Qualcomm Technologies, Inc. IPQ5018\/AP-MP03.6-C1",
"release": {
"distribution": "OpenWrt",
"version": "Chaos Calmer",
"revision": "2c69625+r49254",
"codename": "chaos_calmer",
"target": "ipq\/ipq50xx",
"description": "OpenWrt Chaos Calmer 15.05.1"
}
}
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option disabled '0'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '547'
option dest_ip 'fe80::/10'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'map'
option type 'script'
option path '/etc/firewall.d/map_firewall'
option family 'any'
option reload '1'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'qcanssecm'
option type 'script'
option path '/etc/firewall.d/qca-nss-ecm'
option family 'any'
option reload '1'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
time to upgrade ....
This is an ancient, unsupported, and vulnerable version of OpenWrt. It should not be used at all, especially on the internet.
Hi frollic,
because of some special needs, this version must be used .
In that case I doubt you will find a lot of support here, release's simply to old ...
Hi psherman,
because of some special needs, this version must be used .
As @frollic said, you’re unlikely to find support here. It is so old that few people remember how to use it (many things have changed and the syntax is quite different now, among other things). But it is also known to have numerous major security vulnerabilities and is simply not safe to use in any context anymore.
Also, it is worth pointing out the irony here: you are trying to enable https, theoretically to improve the security posture of the device, yet that version of OpenWrt has many more major security vulnerabilities that are likely to be exploited. It is like using a screen door as the hatch for a submarine.
What are the special needs/requirements for this device?
Hi psherman,
due to the partner only provide this version on the hardware.
then you should probably ask your partner, about setting up the https ...
Perhaps you can tell us what is special about this system? What are the requirements or special features?
You do realize that the (browser side-) requirements for SSL/ HTTPS have changed significantly over the last 6.5 years? What was accepted by browsers back then, isn't necessarily deemed secure enough to be accepted anymore. 15.05.x is EoL for half a decade now.
Hi slh,
however, there is the setting to listen https with the default configuration in uhttpd.lua file in version 15.05, so I think 15.05 might have this function. There may be some preset configurations of https that I have not enabled .
21.02.1 version -
-- Copyright 2010 Jo-Philipp Wich <jow@openwrt.org>
-- Licensed to the public under the Apache License 2.0.
require "nixio.util"
require "luci.http"
require "luci.sys"
require "luci.dispatcher"
require "luci.ltn12"
function handle_request(env)
exectime = os.clock()
local renv = {
CONTENT_LENGTH = env.CONTENT_LENGTH,
CONTENT_TYPE = env.CONTENT_TYPE,
REQUEST_METHOD = env.REQUEST_METHOD,
REQUEST_URI = env.REQUEST_URI,
PATH_INFO = env.PATH_INFO,
SCRIPT_NAME = env.SCRIPT_NAME:gsub("/+$", ""),
SCRIPT_FILENAME = env.SCRIPT_NAME,
SERVER_PROTOCOL = env.SERVER_PROTOCOL,
QUERY_STRING = env.QUERY_STRING,
DOCUMENT_ROOT = env.DOCUMENT_ROOT,
HTTPS = env.HTTPS,
REDIRECT_STATUS = env.REDIRECT_STATUS,
REMOTE_ADDR = env.REMOTE_ADDR,
REMOTE_NAME = env.REMOTE_NAME,
REMOTE_PORT = env.REMOTE_PORT,
REMOTE_USER = env.REMOTE_USER,
SERVER_ADDR = env.SERVER_ADDR,
SERVER_NAME = env.SERVER_NAME,
SERVER_PORT = env.SERVER_PORT
}
local k, v
for k, v in pairs(env.headers) do
k = k:upper():gsub("%-", "_")
renv["HTTP_" .. k] = v
end
local len = tonumber(env.CONTENT_LENGTH) or 0
local function recv()
if len > 0 then
local rlen, rbuf = uhttpd.recv(4096)
if rlen >= 0 then
len = len - rlen
return rbuf
end
end
return nil
end
local send = uhttpd.send
local req = luci.http.Request(
renv, recv, luci.ltn12.sink.file(io.stderr)
)
local x = coroutine.create(luci.dispatcher.httpdispatch)
local hcache = { }
local active = true
while coroutine.status(x) ~= "dead" do
local res, id, data1, data2 = coroutine.resume(x, req)
if not res then
send("Status: 500 Internal Server Error\r\n")
send("Content-Type: text/plain\r\n\r\n")
send(tostring(id))
break
end
if active then
if id == 1 then
send("Status: ")
send(tostring(data1))
send(" ")
send(tostring(data2))
send("\r\n")
elseif id == 2 then
hcache[data1] = data2
elseif id == 3 then
for k, v in pairs(hcache) do
send(tostring(k))
send(": ")
send(tostring(v))
send("\r\n")
end
send("\r\n")
elseif id == 4 then
send(tostring(data1 or ""))
elseif id == 5 then
active = false
elseif id == 6 then
data1:copyz(nixio.stdout, data2)
end
end
end
end
sorry , the file I mean is etc/config/uhttpd
@yuxiuhuang - I think that you really need to look at the big picture...
- OpenWrt 15.05 is very old and has many serious vulnerabilities, making it unsuitable for use.
- Making the web server use https instead of http represents a meaningless security improvement given the fact that there are significant known issues with the old version.
- As several of us have stated already, 15.05 is obsolete and unsupported, and it has been so for over 5 years (and as a result, the "institutional knowledge/memory" of how it works is generally lost)
- The inner workings of OpenWrt are significantly different now than they were back then -- shoehorning files from a recent version will likely break your current installation.
- And even if you don't break your install from trying to use recent files, the underlying crypto libraries are obsolete and may not be trusted by modern browsers (5-7 years newer than the OpenWrt version you are using).
I have asked repeatedly about what makes this specific installation so important. If we know what packages are running and/or what function this device serves, we may be able to help you migrate to a newer version with all of the same functionality and (critically) up-to-date security and support. I'm not sure why this has gone unanswered... I'm not trying to get secret or proprietary information, just trying to understand your needs so that I/we can recommend a better solution.
Hi psherman,
because the partner who provide hardware and chip only support us to 15.05 version.
is this some custom hardware that is not otherwise supported by OpenWrt?