Nothing is using the tunnel.
Oh... nothing. Ok... misunderstood. That's better, though, because it suggests we don't have some odd behavior.
Is OpenVPN up and running? What does the log say?
OpenVPN is definitely up and running. I have made numerous changes over time and now don't know where to start in terms of diagnosing a problem with it.
I know for sure that at one point, my LAN connected device was connected to the VPN for a short while.
The system log doesn't seem to really say much about why the VPN isn't working. All tht I can think of is that when I configured wireless and altered the custom "tun" interface suggested in the openvpn guide, something happened. Sorry, I am not familiar enough with wireless internet connectivity to really know what I am doing here.
```Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: OPTIONS IMPORT: route options modified
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: OPTIONS IMPORT: peer-id set
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: OPTIONS IMPORT: adjusting link_mtu to 1626
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: OPTIONS IMPORT: data channel crypto options modified
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: Preserving previous TUN/TAP instance: tun0
Tue Jan 10 22:57:15 2023 daemon.notice openvpn(VPNSpecial)[1563]: Initialization Sequence Completed
Tue Jan 10 22:57:24 2023 authpriv.info dropbear[12724]: Exit (root) from <192.168.2.128:50298>: Disconnect received
Tue Jan 10 22:57:32 2023 authpriv.info dropbear[19623]: Child connection from 192.168.2.128:50304
Tue Jan 10 22:57:36 2023 authpriv.notice dropbear[19623]: Password auth succeeded for 'root' from 192.168.2.128:50304
Tue Jan 10 22:58:31 2023 authpriv.info dropbear[19623]: Exit (root) from <192.168.2.128:50304>: Disconnect received
Tue Jan 10 22:58:32 2023 authpriv.info dropbear[21590]: Exit (root) from <192.168.2.128:50292>: Disconnect received
Tue Jan 10 22:58:33 2023 authpriv.info dropbear[2836]: Exit (root) from <192.168.2.128:50284>: Disconnect received
Tue Jan 10 22:58:40 2023 authpriv.info dropbear[20950]: Child connection from 192.168.2.128:50310
Tue Jan 10 22:58:45 2023 authpriv.notice dropbear[20950]: Password auth succeeded for 'root' from 192.168.2.128:50310
Tue Jan 10 23:00:04 2023 daemon.warn odhcpd[1146]: A default route is present but there is no public prefix on lan thus we don't announce a default route!
Tue Jan 10 23:04:55 2023 daemon.warn odhcpd[1146]: A default route is present but there is no public prefix on lan thus we don't announce a default route!
Tue Jan 10 23:08:21 2023 daemon.warn odhcpd[1146]: A default route is present but there is no public prefix on lan thus we don't announce a default route!
Tue Jan 10 23:16:02 2023 daemon.warn odhcpd[1146]: A default route is present but there is no public prefix on lan thus we don't announce a default route!
ok... let's take a look at the openvpn config file (likely /etc/config/openvpn)
Ok here it is below
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list device 'tun0'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
root@OpenWrt:~# cat /etc/config/openvpn
config openvpn 'custom_config'
option config '/etc/openvpn/my-vpn.conf'
config openvpn 'sample_server'
option port '1194'
option proto 'udp'
option dev 'tun'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/server.crt'
option key '/etc/openvpn/server.key'
option dh '/etc/openvpn/dh2048.pem'
option server '10.8.0.0 255.255.255.0'
option ifconfig_pool_persist '/tmp/ipp.txt'
option keepalive '10 120'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option status '/tmp/openvpn-status.log'
option verb '3'
config openvpn 'sample_client'
option client '1'
option dev 'tun'
option proto 'udp'
list remote 'my_server_1 1194'
option resolv_retry 'infinite'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/client.crt'
option key '/etc/openvpn/client.key'
option verb '3'
config openvpn 'VPNSpecial'
option config '/etc/openvpn/VPNSpecial.ovpn'
option enabled '1'
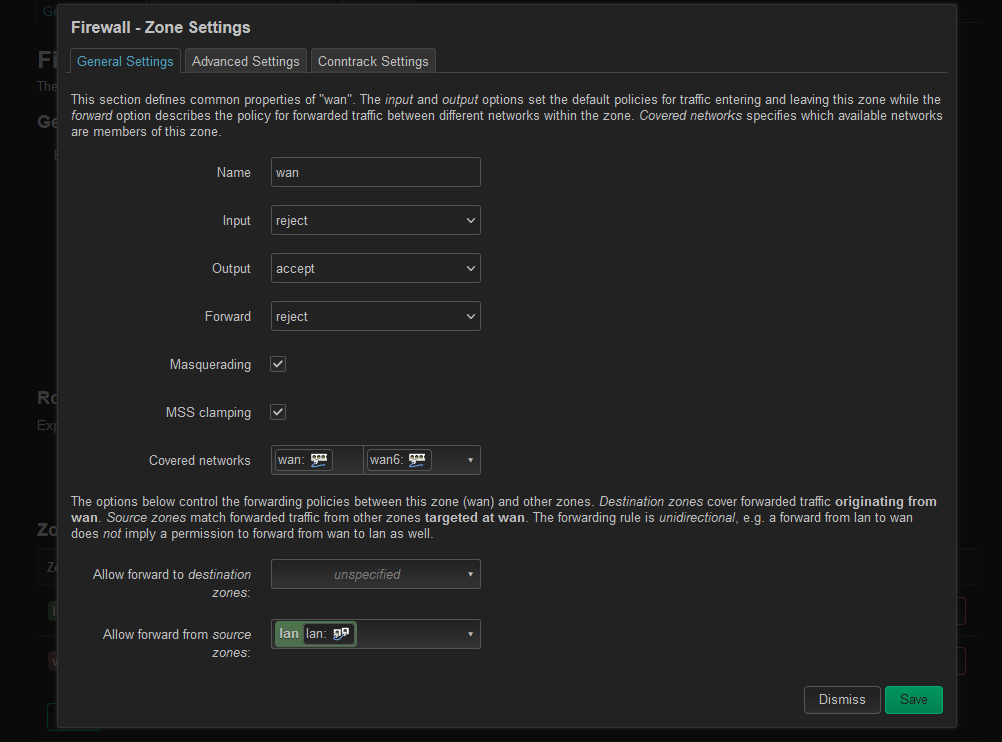
Also, something I recently did, as per the guide here, for firewall, is visit Network->Firewall and Edit WAN to have the following
I don't really know if this is correct or not and wish I understood the proper relationships between the interfaces, WAN, LAN and my VPN server. It's confusing to me to understand why it was working at one point and why traffic no longer seems to be going through the VPN.
Apologies but your suggestion about making a new zone I am not able to understand. What should I be researching and learning about so that I can understand your instructions about a new zone? Access and egress are not evident to me in this context.
The block of code you cited there with 'zone', am I supposed to replace zone with a different zone name? Where should that config be placed?
Obviousy I have haphazardly been making changes without realling understanding things and this appears to be setting me back quite a bit.
In the above guide there are steps 4.1a & 4.1b <- Both in the guide linked here are for earlier versions of operwrt so perhaps that's the issue.
I have attempted both, neither of which to much success. Part A is to create a create a new interface as per their guidelines and the other one is to go into firewall settings, which I have captured in the screenshot above.
Can you show the contents of this file?
Simplified explanation (forgive me if this is obvious):
-
Everything in the
/etc/config/networkfile relates to network interfaces and devices (devices are associated with the physical or virtual interfaces such as ethernet ports or VPN tunnels; this actually does not include the wifi radios, though).- Basically all 'standard' network environments with OpenWrt will have 2 networks of interest lan and wan.
- The "wan" interface is typically your upstream network (i.e. the internet) and it is typically untrusted
- The "lan" is your local area network.This network is usually trusted.
- A network can be associated with a virtual device like a VPN tunnel (tun0), but is not required in the case of OpenVPN tunnels which can be directly referenced in the firewall).
-
The firewall defines the paths traffic is allowed/not allowed to take (but doesn't necessarily mean it will -- there is another component called routing that is involved).
- OpenWrt uses a Zone Based Firewall
- zones contain at least one network each, may have multiple networks associated -- you can treat each zone as a collection of networks that have similar "trust" and permissions profiles (i.e. untrusted like the internet, trusted like your own network, a guest network should have access to the internet just like your lan, but should not be able to talk to your personal trusted devices, etc.)
- The firewall can allow traffic to flow from one zone to another (or not)
- It is possible to have very generic or very granular rules that govern what is allowd/prohibited on a network.
In my earlier comments, I was suggesting that you associate the tun0 device (i.e. the OpenVPN tunnel) with its own zone so that you can control lan > wan forwarding and lan > vpn forwarding separately. This involves removing the wan zone from the lan zone's "allow forward to destination zone" field, and removing the tun0 device from the covered networks in the wan zone. Then, you'll create a new zone that is very similar to the wan zone, but has a new name (vpn) and covers the network device tun0. Then allow lan to forward to vpn.
Thank you again for taking the time to explain this to me. I am not sure I fully get the suggestion yet. I will read it over a few times and try to see if I can make sense of what I need to change.
Below is the heavily redacted ovpn file which I have tested to great success on other devices (and, on this device, managed to get it working once upon a time earlier today for LAN... now, none of the VPN appears to be working, and I don't think it's based on the ovpn contents below.)
# Client
client
tls-client
dev tun
# this will connect with whatever proto DNS tells us (https://community.openvpn.net/openvpn/ticket/934)
proto tcp
remote vpn.tested-and-working-vpn-server.com 7494
resolv-retry infinite
cipher AES-256-CBC
auth SHA256
script-security 2
keepalive 10 120
remote-cert-tls server
# Keys
<ca>
-----BEGIN CERTIFICATE-----
JUSTTRUSTMETHISISOKANDWORKINGANDTESTEDLESEWHERE
-----END CERTIFICATE-----
</ca>
<cert>
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
SOMETHING:IS:GOING:HERE
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=IssuerKing
Validity
Not Before: Sep 9 20:24:39 2022 GMT
Not After : Sep 6 20:24:39 2032 GMT
Subject: CN=WHATEVER
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
1337:6969:123:456
45:3b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
ID:GOES:HERE:123
X509v3 Authority Key Identifier:
keyid:UNIQUE:ID
DirName:/CN=IMPORTANTDIR
serial:SE:RI:AL
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
CR:AZY:SIG
71:91:f4:10
-----BEGIN CERTIFICATE-----
CRAZYCERT
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
CRAZYKEY
-----END PRIVATE KEY-----
</key>
key-direction 1
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
STATICKEY
-----END OpenVPN Static key V1-----
</tls-auth>
# Security
nobind
persist-key
persist-tun
verb 3
I'm not seeing any obvious issues with your openvpn file, although I've always worked with the keys setup as separate files. Should be fine, though, as long a the system reports that the initialization sequence completed.
So when you write the block below,
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list device 'tun0'
config forwarding
option src 'lan'
option dest 'vpn'
That's a block of code for /etc/config/openvpn
Should the same block be added to firewall also?
no, this belongs in the firewall (this is just an excerpt). As compared to the file you posted earlier, I edited the wan zone (removed the device tun0), I created the zone called vpn, I added forwarding from lan > vpn, and I deleted forwarding from lan > wan.
Thanks for the help. Later today when I get back from work I will give this a shot.
Hi @psherman thank you very much for your time assisting me to get traffic through to the VPN tunnel. All is well and working.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.