Hi All,
I hope you are doing well.
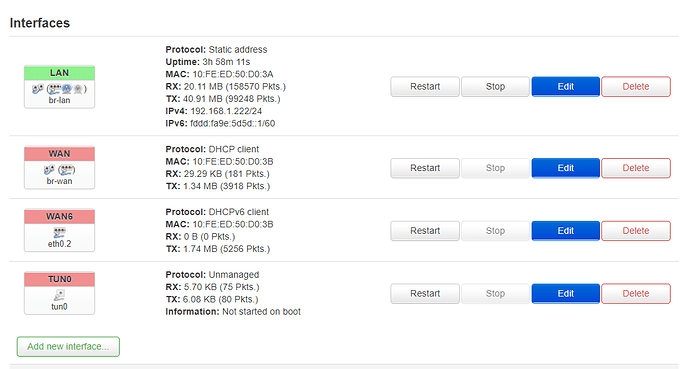
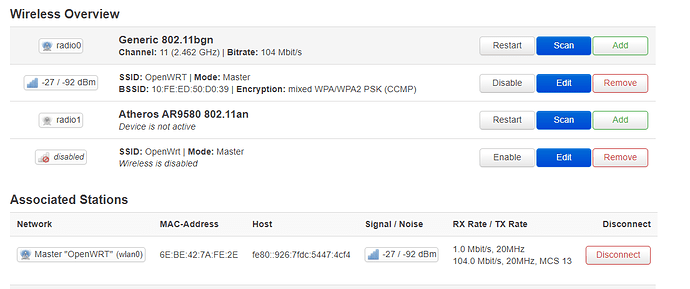
I have setup OpenVPN on my TPlink router and connected succesfully ethernet port is plugged into the LAN as per the image below. what I am trying to do is the following;
- connect to the TPlink AP via wifi with all data going through OpenVPN.
- still connected to the same wifi network I need to cast from the device (phone) to the TV through the google cast dongle.
I have tried a few different things with little success, I am thinking from my reading a heap of firum posts is I would have to make a seperate WLAN (say 192.168.2.x with DHCP and route the traffic to the vpn while also allowing traffic to the 192.168.1.x network.)
Maybe I have overthought and there is a simpler way... Thanks for taking the time to read this, any help links etc would be appreciated.
Please see a rough drawing of the network below and config;
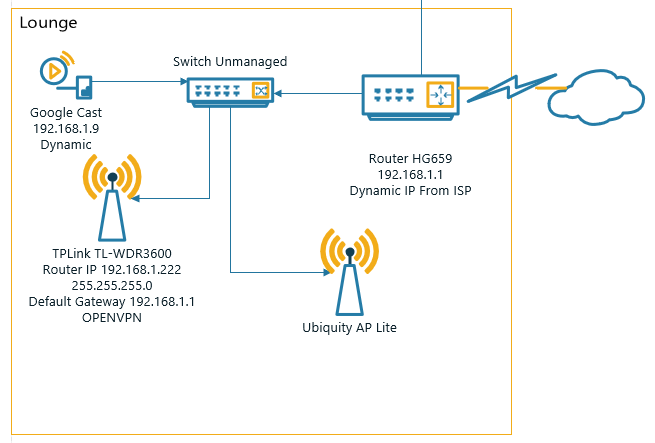
Network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fddd:fa9e:5d5d::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.222'
option gateway '192.168.1.1'
list dns '192.168.1.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option type 'bridge'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '10:fe:ed:50:d0:3b'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config interface 'tun0'
option ifname 'tun0'
option proto 'none'
option auto '0'
DHCP
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wifi_vpn'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'wifi_vpn'
Firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'wan wan6 tun0'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option name 'wifi_vpn'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
option network ' '
config forwarding
option dest 'wan'
option src 'wifi_vpn'
config forwarding
option dest 'wifi_vpn'
option src 'wan'
More outputs
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fddd:fa9e:5d5d::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.222'
option gateway '192.168.1.1'
list dns '192.168.1.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option type 'bridge'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '10:fe:ed:50:d0:3b'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config interface 'tun0'
option ifname 'tun0'
option proto 'none'
option auto '0'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option country 'AU'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option key '#######'
option ssid 'OpenWRT'
option encryption 'psk-mixed+ccmp'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
option disabled '1'
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wifi_vpn'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'wifi_vpn'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'wan wan6 tun0'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option name 'wifi_vpn'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
option network ' '
config forwarding
option dest 'wan'
option src 'wifi_vpn'
config forwarding
option dest 'wifi_vpn'
option src 'wan'
package openvpn
config openvpn 'custom_config'
option config '/etc/openvpn/my-vpn.conf'
config openvpn 'sample_server'
option port '1194'
option proto 'udp'
option dev 'tun'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/server.crt'
option key '/etc/openvpn/server.key'
option dh '/etc/openvpn/dh1024.pem'
option server '10.8.0.0 255.255.255.0'
option ifconfig_pool_persist '/tmp/ipp.txt'
option keepalive '10 120'
option compress 'lzo'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option status '/tmp/openvpn-status.log'
option verb '3'
config openvpn 'sample_client'
option client '1'
option dev 'tun'
option proto 'udp'
list remote 'my_server_1 1194'
option resolv_retry 'infinite'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/client.crt'
option key '/etc/openvpn/client.key'
option compress 'lzo'
option verb '3'
config openvpn 'VPN_Finland'
option config '/etc/openvpn/VPN_Finland.ovpn'
option enabled '1'
head: /etc/openvpn/*.conf: No such file or directory
###############################################################################
###############################################################################
dev tun
###############################################################################
proto tcp
###############################################################################
remote fi.trust.zone 443
###############################################################################
;http-proxy-retry
;http-proxy [proxy server] [proxy port]
###############################################################################
cipher AES-256-CBC
auth SHA512
#auth-nocache
###############################################################################
resolv-retry infinite
nobind
persist-key
client
verb 3
auth-user-pass /etc/openvpn/VPN_Finland.auth
verify-x509-name *.trust.zone name
ping 3
ping-restart 10
#remote-cert-tls server
#remote-cert-ku f6
dhcp-option DNS 109.236.87.2
dhcp-option DNS 144.217.75.55
#uncomment next line if you want your OpenVPN client to ignore DNS settings pushed from VPN server
#pull-filter ignore "dhcp-option DNS "
setenv CLIENT_CERT 0
###############################################################################
<ca>
-----BEGIN CERTIFICATE-----
--the certifcate is in here delete just in-case
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
*--the certifcate is in here delete just in-case*
-----END CERTIFICATE-----
</ca>
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
11: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.222/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
default via 192.168.1.1 dev br-lan
185.117.119.8 via 192.168.1.1 dev br-lan
192.168.1.0/24 dev br-lan scope link src 192.168.1.222
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.222
local 192.168.1.222 dev br-lan table local scope host src 192.168.1.222
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.222
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Feb 28 08:05 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 May 7 20:39 /tmp/resolv.conf
-rw-r--r-- 1 root root 39 Feb 28 08:15 /tmp/resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
Thanks again in advance