A newly flashed OpenWrt (18.06.8 on a MiWiFi mini) and pi-hole setup, the things I changed from OpenWrt are:
- Turn off all ipv6 settings
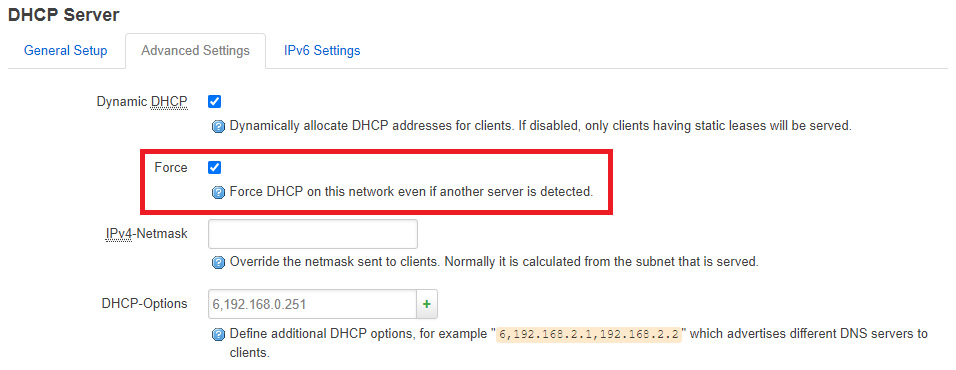
- Force the router as DHCP
- Turn-off rebind protection (it's spamming the log)
- Add an advanced DHCP option to offer pi-hole (
192.168.0.251) as default DNS server.
But now whenever I try to connect to external DNS over TLS from android's private DNS, the phone is telling me that there is no internet available. For my rooted phone, I can use tasker to seamlessly switch on and off the private DNS based on my network status (wifi = off, mobile = on), but I cannot realistically demand all of my network client to do this.
Any ideas why and how can I mitigate this?
Here's my /etc/config/dhcp content:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option leasetime '12h'
option limit '250'
option force '1'
list dhcp_option '6,192.168.0.251'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
and /etc/config/network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option ipaddr '192.168.0.1'
option dns '192.168.0.251'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr 'f2:b4:29:2c:15:5a'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'f0:b4:29:2c:15:5a'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0 1 6t'
config interface 'wwan'
option proto 'dhcp'
option delegate '0'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '2 3 4 6t'