dana44
May 9, 2022, 4:45pm
122
Can you run flent rrul -p all_scaled -l 60 -H netperf-west.bufferbloat.net -o results.png on both the 2.4 and 5GHz radios and share the results? If you're on windows you'll need to install wsl ubuntu first.
The 2.4GHz radio has had issues for years https://github.com/openwrt/mt76/issues/487
Yes, I had to rebuild my install from scratch as suggested. It then works well except firewall4 needing an older version of software! and the fact that it boots - eventually..... both brought up by elizan.
Sure! I will update you with the info later, need some time.
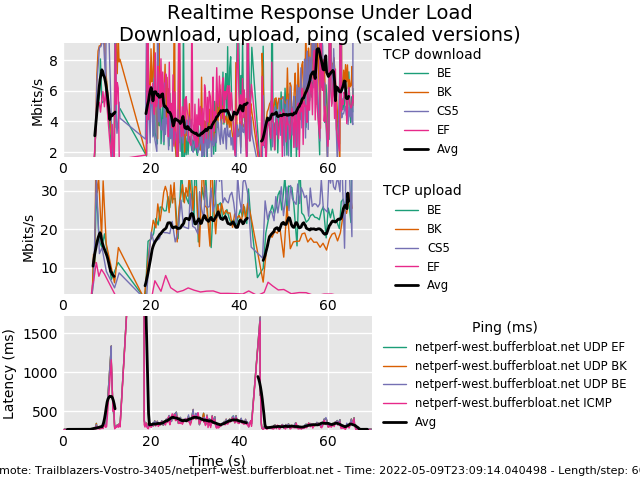
Archer C50 V3 2.4Ghz
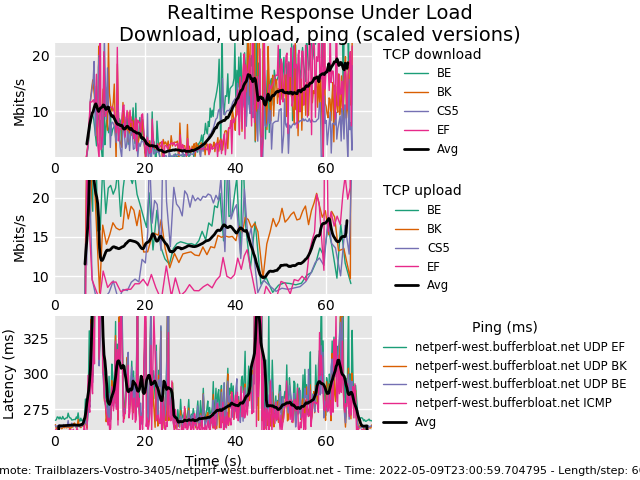
Archer C50 V3 5Ghz
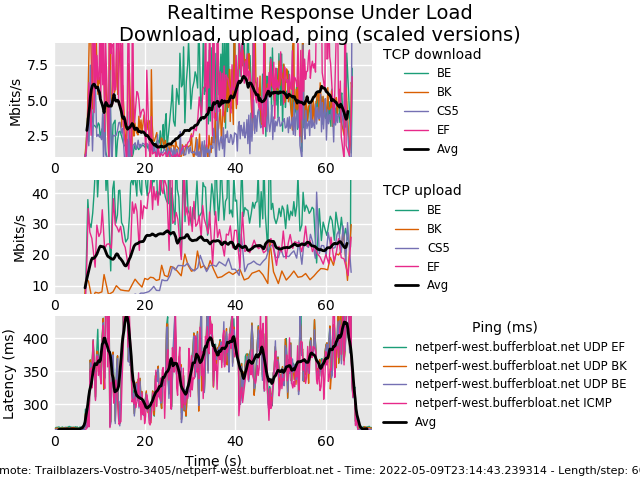
Netgear R6220 2.4Ghz
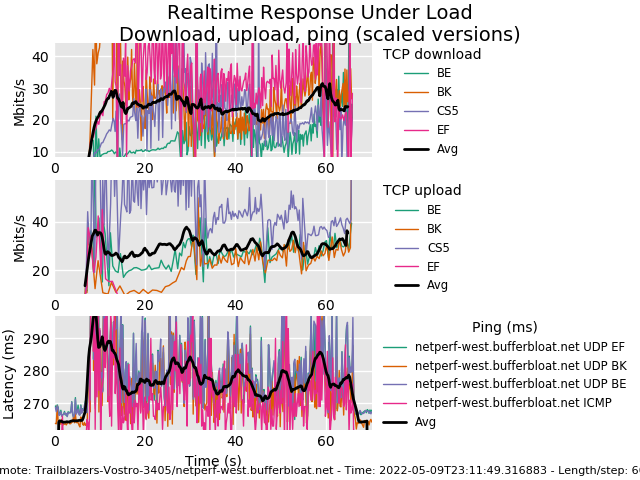
Netgear R6220 5Ghz
I have igmp_snooping enabled for 2.4Ghz radio on both the routers and enbled Software Flow offloading only on Archer C50.
Do tell me your analysis.
dana44
May 9, 2022, 8:19pm
126
trailblazer:
Archer C50 V3 2.4Ghz
This looks like a disconnect to me. I don't have any advice to solve it. I suggest adding this to the github bug report so anybody interested can see the 2.4GHz radio still has reproducible issues, even on the latest version.
There might be clues in syslog.
logread | grep STA
i confirm too the bug,
disconnect wirelless by intermitence on 2'4ghz
Belkin rt3200 22.03 rc1 19302
1 Like
I see this few times. This is the 2.4Ghz device that frequently shows "Connectd but no internet".
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.11: authentication OK (open system)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxMLME: MLME-AUTHENTICATE.indication(36:9e:68:xx:xx:xx, OPEN_SYSTEM)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxMLME: MLME-DELETEKEYS.request(36:9e:68:xx:xx:xx)
Tue May 10 00:57:15 2022 daemon.info hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.11: authenticated
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.11: association OK (aid 3)
Tue May 10 00:57:15 2022 daemon.info hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.11: associated (aid 3)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxMLME: MLME-ASSOCIATE.indication(36:9e:68:xx:xx:xx)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxMLME: MLME-DELETEKEYS.request(36:9e:68:xx:xx:xx)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.11: binding station to interface 'wlan0'
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: event 1 notification
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: start authentication
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.1X: unauthorizing port
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: sending 1/4 msg of 4-Way Handshake
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: received EAPOL-Key frame (2/4 Pairwise)
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: sending 3/4 msg of 4-Way Handshake
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: received EAPOL-Key frame (4/4 Pairwise)
Tue May 10 00:57:15 2022 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 36:9e:68:xx:xx:xx
Tue May 10 00:57:15 2022 daemon.debug hostapd: wlan0: STA 36:9e:68:xx:xx:xxIEEE 802.1X: authorizing port
Tue May 10 00:57:15 2022 daemon.info hostapd: wlan0: STA 36:9e:68:xx:xx:xxWPA: pairwise key handshake completed (RSN)
Run logread | grep 'warn\|err'
No wlan0 errors!
root@ArcherC50:~# logread | grep 'warn\|err'
Mon May 9 21:55:13 2022 daemon.err nlbwmon[1706]: The netlink receive buffer size of 524288 bytes will be capped to 180224 bytes
Mon May 9 21:55:13 2022 daemon.err nlbwmon[1706]: by the kernel. The net.core.rmem_max sysctl limit needs to be raised to
Mon May 9 21:55:13 2022 daemon.err nlbwmon[1706]: at least 524288 in order to sucessfully set the desired receive buffer size!
Tue May 10 08:17:25 2022 authpriv.warn dropbear[3890]: Pubkey auth bad signature for 'root' with key SHA256:xxxxxxxxxx from 10.0.2.30:25536
Run cat /etc/config/wireless, redact the passwords in the option key sections, and post.
Looks like you have some other stuff going on with nlbwmon receive buffers and dropbear as well.
root@ArcherC50:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option htmode 'HT40'
option noscan '1'
option hwmode '11g'
option cell_density '0'
option channel '10'
option country 'IN'
option log_level '1'
option igmp_snooping '1'
config wifi-device 'radio1'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'VHT80'
option noscan '1'
option hwmode '11a'
option cell_density '0'
option channel '48'
option txpower '22'
option country 'IN'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option key 'password'
option ssid 'Hellblazer_EXT'
option encryption 'psk2'
option disassoc_low_ack '0'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'ap'
option ssid 'ThunderBird_EXT'
option key 'password'
option network 'lan'
option encryption 'psk2'
option disassoc_low_ack '0'
trailblazer:
option htmode 'HT40'
This can cause problems on 2.4 GHz.
I would suggest using 20 MHz, unless you live in area with virtually no neighbors.
trailblazer:
option channel '10'
Channels 1, 6, and 11 are the non-overlapping channels for 2.4 GHz
1 Like
Well changing the settings as per your advice did improve the performance:
But changing the channel width reduced the speeds over 2.4Ghz.
Did you test with channels 1, 6, and 11?
The above screenshot is on channel 11. But I will edit this reply after testing on channels 1 and 6
Edit: Tested on all the three channels, speeds are about 40mbps down and 57mbps up.
Your neighbors, however, will appreciate you running with a 20 MHz channel width.
What are you using to test?
Try the Ookla Speedtest app and Waveform's bufferbloat/speed test.
1 Like
I use channel 1 and 20mhz on my router
Is possible thzn if my router box of fai isp use too 1 he creage go interference ??
I has never this problem before this update
I'm not sure I understand what you're saying...
Lots of people use 1, 6, and 11...so channel overcrowding can occur.
A good WiFi analyzer app will tell you who is using what channels in your area, your signal strength, and your signal-to-noise ratio (SNR).
I meant I use channel 1 on my OpenWrt router but I have a modem router from my ISP before that also uses Wi-Fi if they both use the same channel is it possible that is interference in my French country we also use 1 6 11 before the switch to 22.03 with the belkin rt3200 no problem encountered with wifi