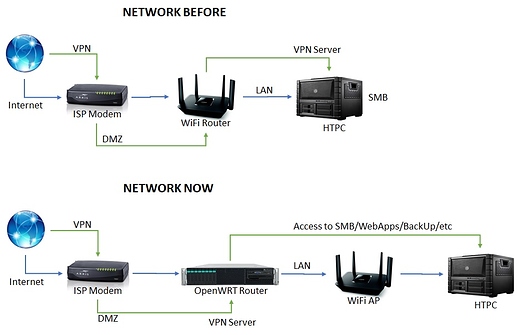
Hi everyone,
I'm trying to get my VPN Server to work correctly, my goal is to have both LAN and WAN access, I'm migrating a couple of services from an Arch HTPC (this serves everything from SMB, Owncloud, VPN, Kodi, CUPS, etc) to a x86_64 OpenWRT router, in my HTPC all services work fine (and I'm using it as a reference for configs), but it's been a few days now and I can't find a solution to this (after reading several how-tos and posts).
My LAN is working fine and with internet access, and I have other small services working fine (adblock, ddns, etc,), its just my VPN which has no LAN nor WAN.
My current network setup is like this: ISP(router)---->[DMZ]x86Router(OpenWRT)[OpenVPN]----->LAN
I'm unable to put my ISP router in bridge mode because of my current contract, thus the DMZ (I'll change my contract once I have a fully funtional router).
I hope you can help me, it feels like its something stupid and obvious but I can't pin it.
Thank you.
I leave the config details, if you need more info let me know.
ISP (gateway): 192.168.1.254
Router:
eth0 (WAN): 192.168.1.150
eth1 & eth2 (LAN): 10.209.1.0/24
tun0 (VPN): 10.8.0.0/24
network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdaa:4d3d:746e::/48'
network.LAN1=interface
network.LAN1.igmp_snooping='1'
network.LAN1.stp='1'
network.LAN1.type='bridge'
network.LAN1.proto='static'
network.LAN1.ipaddr='10.209.1.1'
network.LAN1.netmask='255.255.255.0'
network.LAN1.ip6assign='64'
network.LAN1.gateway='192.168.1.150'
network.LAN1.ifname='eth1 eth2'
network.wan=interface
network.wan.ifname='eth0'
network.wan.persist='true'
network.wan.maxfail='0'
network.wan.holdoff='10'
network.wan.proto='static'
network.wan.netmask='255.255.255.0'
network.wan.dns='8.8.8.8'
network.wan.ipaddr='192.168.1.150'
network.wan.gateway='192.168.1.254'
network.wan_dev=device
network.wan_dev.name='eth0'
network.wan_dev.macaddr='FC:AA:14:C6:95:7D'
network.vpn=interface
network.vpn.ifname='tun0'
network.vpn.proto='none'
firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='LAN1'
firewall.@zone[1]=zone
firewall.@zone[1].name='VPN'
firewall.@zone[1].network='vpn'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='wan'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].network='wan'
firewall.@zone[2].masq='1'
firewall.@zone[2].input='DROP'
firewall.@zone[2].forward='DROP'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='lan'
firewall.@forwarding[1].dest='VPN'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].target='DROP'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@redirect[0]=redirect
firewall.@redirect[0].dest_port='443'
firewall.@redirect[0].src='wan'
firewall.@redirect[0].name='Owncloud'
firewall.@redirect[0].src_dport='443'
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].dest_ip='10.209.1.101'
firewall.@redirect[0].dest='lan'
firewall.@rule[11]=rule
firewall.@rule[11].src='*'
firewall.@rule[11].target='ACCEPT'
firewall.@rule[11].name='Allow-VPN'
firewall.@rule[11].dest_port='834'
firewall.@rule[11].proto='udp'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].dest='lan'
firewall.@forwarding[2].src='VPN'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].dest='wan'
firewall.@forwarding[3].src='VPN'
iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
input_rule all -- anywhere anywhere /* !fw3: Custom input rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
syn_flood tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN /* !fw3 */
ACCEPT udp -- anywhere anywhere udp dpt:834 /* !fw3: Allow-VPN */
zone_lan_input all -- anywhere anywhere /* !fw3 */
zone_VPN_input all -- anywhere anywhere /* !fw3 */
zone_wan_input all -- anywhere anywhere /* !fw3 */
Chain FORWARD (policy DROP)
target prot opt source destination
ACCEPT all -- anywhere anywhere
ACCEPT all -- 10.8.0.0/24 Server.lan
forwarding_rule all -- anywhere anywhere /* !fw3: Custom forwarding rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_forward all -- anywhere anywhere /* !fw3 */
zone_VPN_forward all -- anywhere anywhere /* !fw3 */
zone_wan_forward all -- anywhere anywhere /* !fw3 */
reject all -- anywhere anywhere /* !fw3 */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
output_rule all -- anywhere anywhere /* !fw3: Custom output rule chain */
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */
zone_lan_output all -- anywhere anywhere /* !fw3 */
zone_VPN_output all -- anywhere anywhere /* !fw3 */
zone_wan_output all -- anywhere anywhere /* !fw3 */
Chain forwarding_VPN_rule (1 references)
target prot opt source destination
Chain forwarding_lan_rule (1 references)
target prot opt source destination
Chain forwarding_rule (1 references)
target prot opt source destination
Chain forwarding_wan_rule (1 references)
target prot opt source destination
Chain input_VPN_rule (1 references)
target prot opt source destination
Chain input_lan_rule (1 references)
target prot opt source destination
Chain input_rule (1 references)
target prot opt source destination
Chain input_wan_rule (1 references)
target prot opt source destination
Chain output_VPN_rule (1 references)
target prot opt source destination
Chain output_lan_rule (1 references)
target prot opt source destination
Chain output_rule (1 references)
target prot opt source destination
Chain output_wan_rule (1 references)
target prot opt source destination
Chain reject (2 references)
target prot opt source destination
REJECT tcp -- anywhere anywhere /* !fw3 */ reject-with tcp-reset
REJECT all -- anywhere anywhere /* !fw3 */ reject-with icmp-port-unreachable
Chain syn_flood (1 references)
target prot opt source destination
RETURN tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN limit: avg 25/sec burst 50 /* !fw3 */
DROP all -- anywhere anywhere /* !fw3 */
Chain zone_VPN_dest_ACCEPT (3 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_VPN_forward (1 references)
target prot opt source destination
forwarding_VPN_rule all -- anywhere anywhere /* !fw3: Custom VPN forwarding rule chain */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone VPN to lan forwarding policy */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone VPN to wan forwarding policy */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_VPN_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_VPN_input (1 references)
target prot opt source destination
input_VPN_rule all -- anywhere anywhere /* !fw3: Custom VPN input rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_VPN_src_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_VPN_output (1 references)
target prot opt source destination
output_VPN_rule all -- anywhere anywhere /* !fw3: Custom VPN output rule chain */
zone_VPN_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_VPN_src_ACCEPT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */
Chain zone_lan_dest_ACCEPT (5 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_forward (1 references)
target prot opt source destination
forwarding_lan_rule all -- anywhere anywhere /* !fw3: Custom lan forwarding rule chain */
zone_wan_dest_REJECT all -- anywhere anywhere MAC 00:D9:D1:B0:96:34 TIME from 20:00:00 to 10:00:00 on Mon,Tue,Wed,Thu,Sun /* !fw3: Niños-Escuela */
zone_wan_dest_REJECT all -- anywhere anywhere MAC 00:D9:D1:B0:96:34 TIME from 22:00:00 to 10:00:00 on Fri,Sat /* !fw3: Niños-Finde */
zone_wan_dest_REJECT all -- anywhere anywhere MAC 70:3A:51:30:49:C6 TIME from 23:00:00 to 09:00:00 /* !fw3: Goran-Parental */
zone_wan_dest_REJECT all -- anywhere anywhere MAC EE:C6:FC:24:3F:CD TIME from 23:00:00 to 09:00:00 /* !fw3: Goran-Parental */
zone_wan_dest_REJECT all -- anywhere anywhere MAC 00:F4:8D:59:99:91 TIME from 23:00:00 to 09:00:00 /* !fw3: Goran-Parental */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone lan to wan forwarding policy */
zone_VPN_dest_ACCEPT all -- anywhere anywhere /* !fw3: Zone lan to VPN forwarding policy */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_input (1 references)
target prot opt source destination
input_lan_rule all -- anywhere anywhere /* !fw3: Custom lan input rule chain */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_lan_src_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_output (1 references)
target prot opt source destination
output_lan_rule all -- anywhere anywhere /* !fw3: Custom lan output rule chain */
zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_lan_src_ACCEPT (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */
Chain zone_wan_dest_ACCEPT (3 references)
target prot opt source destination
DROP all -- anywhere anywhere ctstate INVALID /* !fw3: Prevent NAT leakage */
ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_dest_DROP (1 references)
target prot opt source destination
DROP all -- anywhere anywhere /* !fw3 */
Chain zone_wan_dest_REJECT (5 references)
target prot opt source destination
reject all -- anywhere anywhere /* !fw3 */
Chain zone_wan_forward (1 references)
target prot opt source destination
forwarding_wan_rule all -- anywhere anywhere /* !fw3: Custom wan forwarding rule chain */
zone_lan_dest_ACCEPT esp -- anywhere anywhere /* !fw3: Allow-IPSec-ESP */
zone_lan_dest_ACCEPT udp -- anywhere anywhere udp dpt:isakmp /* !fw3: Allow-ISAKMP */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */
zone_wan_dest_DROP all -- anywhere anywhere /* !fw3 */
Chain zone_wan_input (1 references)
target prot opt source destination
input_wan_rule all -- anywhere anywhere /* !fw3: Custom wan input rule chain */
ACCEPT udp -- anywhere anywhere udp dpt:bootpc /* !fw3: Allow-DHCP-Renew */
DROP icmp -- anywhere anywhere icmp echo-request /* !fw3: Allow-Ping */
ACCEPT igmp -- anywhere anywhere /* !fw3: Allow-IGMP */
ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */
zone_wan_src_DROP all -- anywhere anywhere /* !fw3 */
Chain zone_wan_output (1 references)
target prot opt source destination
output_wan_rule all -- anywhere anywhere /* !fw3: Custom wan output rule chain */
zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */
Chain zone_wan_src_DROP (1 references)
target prot opt source destination
DROP all -- anywhere anywhere /* !fw3 */
VPN Server
openvpn.MardyVPN=openvpn
openvpn.MardyVPN.comp_lzo='yes'
openvpn.MardyVPN.persist_tun='1'
openvpn.MardyVPN.persist_key='1'
openvpn.MardyVPN.cipher='AES-256-CBC'
openvpn.MardyVPN.ca='/etc/openvpn/pki/ca.crt'
openvpn.MardyVPN.dh='/etc/openvpn/pki/dh.pem'
openvpn.MardyVPN.key='/etc/openvpn/pki/private/server.key'
openvpn.MardyVPN.verb='3'
openvpn.MardyVPN.cert='/etc/openvpn/pki/issued/server.crt'
openvpn.MardyVPN.keepalive='10 120'
openvpn.MardyVPN.mode='server'
openvpn.MardyVPN.client_to_client='1'
openvpn.MardyVPN.log='/var/log/openvpn.log'
openvpn.MardyVPN.enabled='1'
openvpn.MardyVPN.compress='lzo'
openvpn.MardyVPN.log_append='/var/log/openvpn.log'
openvpn.MardyVPN.port='834'
openvpn.MardyVPN.proto='udp'
openvpn.MardyVPN.dev='vpn'
openvpn.MardyVPN.dev_type='tun'
openvpn.MardyVPN.user='nobody'
openvpn.MardyVPN.group='nogroup'
openvpn.MardyVPN.mute='5'
openvpn.MardyVPN.tls_server='1'
openvpn.MardyVPN.key_direction='0'
openvpn.MardyVPN.tls_auth='/etc/openvpn/pki/ta.key'
openvpn.MardyVPN.auth='SHA512'
openvpn.MardyVPN.server='10.8.0.0 255.255.255.0'
openvpn.MardyVPN.topology='subnet'
openvpn.MardyVPN.push='redirect-gateway def1' 'dhcp-option DNS 10.209.1.1' 'route 10.209.1.0 255.255.255.0'
ip a; ip r; traceroute openwrt.org
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ifb0: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN group default qlen 32
link/ether ae:12:23:87:83:0d brd ff:ff:ff:ff:ff:ff
3: ifb1: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN group default qlen 32
link/ether 06:7b:0a:d7:8b:ec brd ff:ff:ff:ff:ff:ff
4: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether fc:aa:14:c6:95:7d brd ff:ff:ff:ff:ff:ff
inet 192.168.1.150/24 brd 192.168.1.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::feaa:14ff:fec6:957d/64 scope link
valid_lft forever preferred_lft forever
5: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-LAN1 state UP group default qlen 1000
link/ether 50:3e:aa:03:95:83 brd ff:ff:ff:ff:ff:ff
6: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-LAN1 state UP group default qlen 1000
link/ether 50:3e:aa:03:9b:c9 brd ff:ff:ff:ff:ff:ff
7: br-LAN1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 50:3e:aa:03:95:83 brd ff:ff:ff:ff:ff:ff
inet 10.209.1.1/24 brd 10.209.1.255 scope global br-LAN1
valid_lft forever preferred_lft forever
inet6 fdaa:4d3d:746e::1/64 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::523e:aaff:fe03:9583/64 scope link
valid_lft forever preferred_lft forever
9: vpn: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 10.8.0.1/24 brd 10.8.0.255 scope global vpn
valid_lft forever preferred_lft forever
inet6 fe80::efc6:2002:d55a:a184/64 scope link stable-privacy
valid_lft forever preferred_lft forever
default via 192.168.1.254 dev eth0 proto static
10.8.0.0/24 dev vpn proto kernel scope link src 10.8.0.1
10.209.1.0/24 dev br-LAN1 proto kernel scope link src 10.209.1.1
192.168.1.0/24 dev eth0 proto kernel scope link src 192.168.1.150
traceroute to openwrt.org (139.59.209.225), 30 hops max, 46 byte packets
1 192.168.1.254 (192.168.1.254) 1.645 ms 0.436 ms 0.403 ms
2 dsl-servicio-l200.uninet.net.mx (XXX.XXX.XXX.XXX) 3.154 ms 2.332 ms 2.663 ms
3 bb-la-grand-8-be5.uninet.net.mx (XXX.XXX.XXX.XXX) 48.254 ms 47.584 ms 55.923 ms
4 ffm-b11-link.telia.net (62.115.32.37) 56.044 ms 55.504 ms 58.029 ms
5 ash-bb3-link.telia.net (62.115.137.36) 176.074 ms 175.047 ms ash-bb2-link.telia.net (62.115.137.38) 173.927 ms
6 prs-bb3-link.telia.net (62.115.112.243) 176.279 ms prs-bb4-link.telia.net (62.115.122.158) 177.171 ms prs-bb3-link.telia.net (62.115.112.243) 181.895 ms
7 ffm-bb2-link.telia.net (62.115.114.99) 174.759 ms 169.906 ms ffm-bb1-link.telia.net (62.115.123.12) 176.807 ms
8 ffm-b5-link.telia.net (62.115.114.91) 170.929 ms ffm-b5-link.telia.net (62.115.114.89) 178.565 ms 174.662 ms
9 * digitalocean-ic-328178-ffm-b4.c.telia.net (80.239.128.23) 194.863 ms 189.065 ms
10 * * *
11 * * *
12 wiki-01.infra.openwrt.org (139.59.209.225) 193.965 ms 189.302 ms 194.144 ms
 )
)