I am trying to use Policy-Based Routing(PBR) to connect my TV to ProtonVPN. I can install ProtonVPN on the TV, but it has a service which kills the app whenever another app is launched. I can also install put the VPN on my Inseego M2000 hotspot, but I don’t want all of my traffic running through the VPN. There is no way to do PBR on the hotspot.
I’ve gone through all the steps of setting up OpenVPN on the router.
root@OpenWrt:~# openvpn --config /etc/openvpn/protonvpn.ovpn
2025-11-05 05:32:39 OpenVPN 2.6.14 arm-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] [DCO]
2025-11-05 05:32:39 library versions: OpenSSL 3.0.18 30 Sep 2025, LZO 2.10
2025-11-05 05:32:39 DCO version: N/A
Enter Auth Username:<my-email@google.com>
Enter Auth Password:
2025-11-05 05:33:51 TCP/UDP: Preserving recently used remote address: [AF_INET]138.199.50.98:7770
2025-11-05 05:33:51 Attempting to establish TCP connection with [AF_INET]138.199.50.98:7770
2025-11-05 05:33:52 TCP connection established with [AF_INET]138.199.50.98:7770
2025-11-05 05:33:52 TCPv4_CLIENT link local: (not bound)
2025-11-05 05:33:52 TCPv4_CLIENT link remote: [AF_INET]138.199.50.98:7770
2025-11-05 05:33:52 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2025-11-05 05:33:52 [node-us-139.protonvpn.net] Peer Connection Initiated with [AF_INET]138.199.50.98:7770
2025-11-05 05:34:56 No reply from server to push requests in 64s
2025-11-05 05:34:56 SIGUSR1[soft,no-push-reply] received, process restarting
2025-11-05 05:34:57 TCP/UDP: Preserving recently used remote address: [AF_INET]138.199.50.98:8443
2025-11-05 05:34:57 Attempting to establish TCP connection with [AF_INET]138.199.50.98:8443
2025-11-05 05:34:57 TCP connection established with [AF_INET]138.199.50.98:8443
2025-11-05 05:34:57 TCPv4_CLIENT link local: (not bound)
2025-11-05 05:34:57 TCPv4_CLIENT link remote: [AF_INET]138.199.50.98:8443
2025-11-05 05:34:57 [node-us-139.protonvpn.net] Peer Connection Initiated with [AF_INET]138.199.50.98:8443
2025-11-05 05:35:59 No reply from server to push requests in 62s
2025-11-05 05:35:59 SIGUSR1[soft,no-push-reply] received, process restarting
2025-11-05 05:36:00 TCP/UDP: Preserving recently used remote address: [AF_INET]138.199.50.98:443
2025-11-05 05:36:00 Attempting to establish TCP connection with [AF_INET]138.199.50.98:443
2025-11-05 05:36:00 TCP connection established with [AF_INET]138.199.50.98:443
2025-11-05 05:36:00 TCPv4_CLIENT link local: (not bound)
2025-11-05 05:36:00 TCPv4_CLIENT link remote: [AF_INET]138.199.50.98:443
2025-11-05 05:36:00 [node-us-139.protonvpn.net] Peer Connection Initiated with [AF_INET]138.199.50.98:443
2025-11-05 05:37:03 No reply from server to push requests in 63s
2025-11-05 05:37:03 SIGUSR1[soft,no-push-reply] received, process restarting
This is the output when I try to start openvpn.
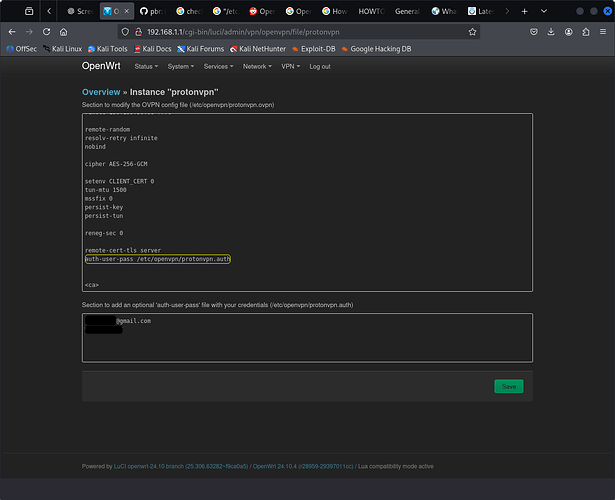
I modified the .ovpn file to include my credentials and that seems to allow me to start the service through LuCI, but it starts failing to authenticate from the command line when running openvpn --config /etc/openvpn/protonvpn.ovpn and the interface tun0 is never created, so I can’t finish setting up the connection. I assume this is because SIGUSR1[soft,no-push-reply] received, process restartingmeans a tunnel is never established.
root@OpenWrt:~# nc -v -z 138.199.50.98 443
Warning: Host 138.199.50.98 isn't authoritative! (direct lookup failed)
138.199.50.98 443 (https) open
I seem to be able to connect to the endpoint over TCP and downloaded the TCP .ovpn file from ProtonVPN:
client
dev tun
proto tcp
remote 138.199.50.98 443
remote 138.199.50.98 8443
remote 138.199.50.98 7770
remote-random
resolv-retry infinite
nobind
cipher AES-256-GCM
setenv CLIENT_CERT 0
tun-mtu 1500
mssfix 0
persist-key
persist-tun
reneg-sec 0
remote-cert-tls server
auth-user-pass
<ca>
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
</ca>
<tls-crypt>
-----BEGIN OpenVPN Static key V1-----
...
-----END OpenVPN Static key V1-----
</tls-crypt>
I did change one line of the .ovpn.
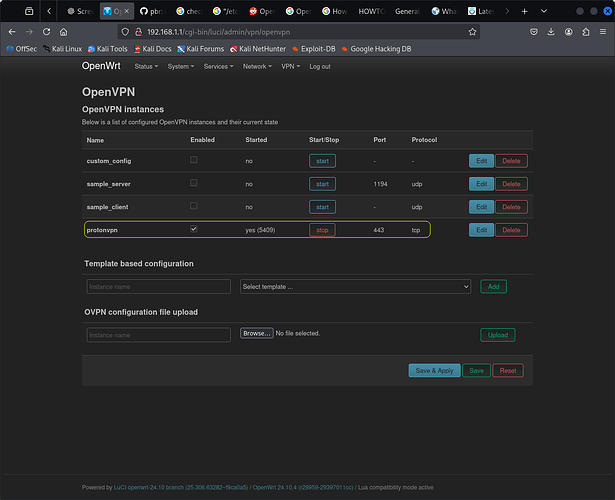
As you can see below, the vpn is running.
But there is no tun0 interface created. Again, I don’t think it’s connecting.
root@OpenWrt:~# ifconfig tun0
ifconfig: tun0: error fetching interface information: Device not found
I can connect to ProtonVPN using their app from my phone from behind the router.
This is what ChatGPT thinks is the issue.
# Why TCP VPN Fails on Your OpenWRT Router Behind the Hotspot
## 1. Setup Context
- **Router:** WRT3200ACM running OpenWRT 24.10.4
- **WAN:** Inseego M2000 LTE hotspot
- **VPN:** ProtonVPN over TCP (ports 443, 8443, 7770)
- **Problem:** OpenWRT cannot establish a `tun0` interface; TCP connection to VPN endpoint fails
- **Observation:** ProtonVPN app on clients behind the same hotspot works fine
---
## 2. Key Differences Between Router and Client App
**ProtonVPN app works because:**
- It handles **NAT traversal automatically**
- Uses **UDP or TCP encapsulation** intelligently
- May use **obfuscated connections** to bypass restrictive NAT/firewalls
**Router behavior:**
- OpenWRT initiates **raw TCP connections** directly to the VPN server
- Router’s WAN IP is **behind carrier NAT (the hotspot)**
- TCP connections fail if the NAT/firewall blocks or drops packets
---
## 3. Likely Primary Issue
**The router is behind a double NAT:**
1. Hotspot NAT
2. Router NAT
**Problems caused by double NAT:**
- TCP sessions may fail
- Hotspot may block or throttle certain outbound TCP ports
- Some carriers actively block VPN traffic
**Why the app works:**
- ProtonVPN app may use **UDP with TCP fallback**, obfuscation, or unusual ports to bypass NAT restrictions
- OpenWRT’s raw TCP connection lacks these advanced techniques
---
## 4. Supporting Evidence
- Multiple TCP ports (443, 8443, 7770) fail
- This is classic behavior for **CGNAT / restrictive hotspot firewall**
---
## 5. Additional Factors
- OpenVPN TCP on OpenWRT may **not handle NAT hairpinning** correctly
- Hotspot may implement **stateful firewall rules** that block unknown TCP connections
- ProtonVPN app may use **packet fragmentation or TLS wrapping** that OpenVPN client does not
---
## 6. Implications
- **Not a router configuration problem**
- **Not a VPN server problem**
- Primary issue: **carrier NAT / hotspot restrictions breaking TCP VPN connections from the router**
**Workarounds:**
1. Use **WireGuard** instead of OpenVPN TCP — often works better through CGNAT
2. Put the router in **bridge mode** behind the hotspot (gets a public IP)
3. Use the **hotspot’s VPN** and implement **policy-based routing** on the router
4. Use a **VPN client on each device** behind the router if router-based VPN fails
I’ve already tried WireGuard, but my provider seems to block all UDP. Option 4 is not really an option for me as I’ve explained. I don’t think bridge mode will work, my hotspot does not have IP Passthrough (though it does have IPv6 Transparent Mode). Option 3 doesn’t seem possible as I think I would need PBR on the hotspot which its firmare does not support.
Sorry for such a long post. Any help is appreciated.