This tutorial is old, but it was pretty easy to follow. You need to create the certificates, so read that section carefully. You can actually do this on your computer if you install easyRSA onto your computer (easiest on a Mac or Linux machine, should also work on Windows with the CLI or WSL).
Now work through the errors one at a time.
Can you explain me what is the right adress on server and 'dhcp-option dns' and 'dhcp-option DOMAIN vpn' ?
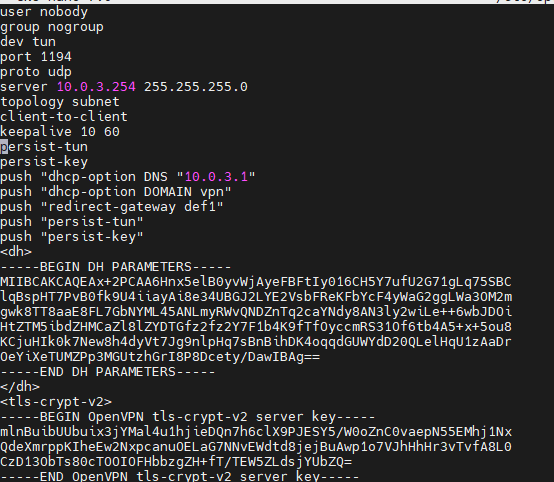
server 10.0.3.254 255.255.255.0
topology subnet
client-to-client
keepalive 10 60
persist-tun
persist-key
push "dhcp-option DNS "10.0.3.1"
push "dhcp-option DOMAIN vpn"
push "redirect-gateway def1"
push "persist-tun"
push "persist-key"
server is a network IP, for a /24 it will always end with .0. The OpenVPN server will take the .1 for its end of the tunnel then issue .2 and so on to clients.
As with most things, the further you stray from the default example configuration, the less likely it is to work.
This is a syntax error, unbalanced quote marks.
Yes, I followed this : https://openwrt.org/docs/guide-user/services/vpn/openvpn/server
But I just changed the IP of interface and server to 192.168.x.x -> 10.0.x.x
That's fine, but stick with the principles in the tutorials.... as @mk24 stated, 10.0.3.0 would be a valid network definition here.
Yes now :
user nobody
group nogroup
dev tun
port 1194
proto udp
server 10.0.3.0 255.255.255.0
topology subnet
client-to-client
keepalive 10 60
persist-tun
persist-key
push "dhcp-option DNS 10.0.3.1"
push "dhcp-option DOMAIN lan"
push "redirect-gateway def1"
push "persist-tun"
push "persist-key"
But same problem :
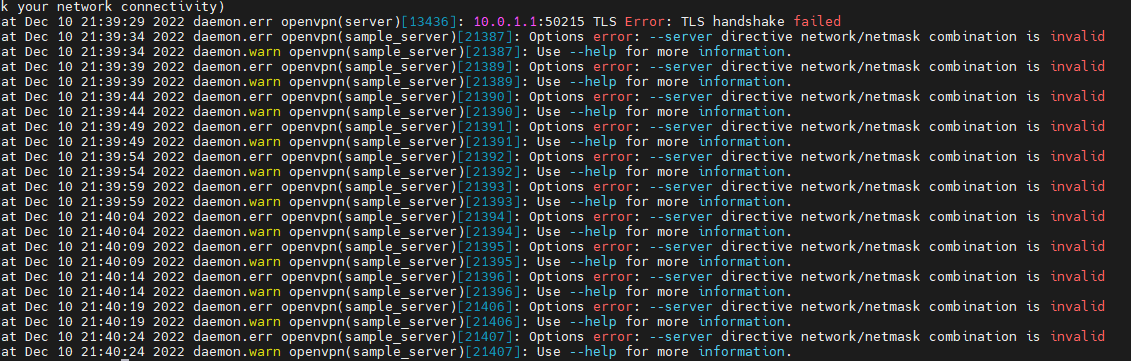
ck your network connectivity)
Sat Dec 10 21:56:56 2022 daemon.err openvpn(server)[13436]: 10.0.1.1:54856 TLS Error: TLS handshake failed
Sat Dec 10 21:56:59 2022 daemon.err openvpn(sample_server)[22710]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:56:59 2022 daemon.warn openvpn(sample_server)[22710]: Use --help for more information.
Sat Dec 10 21:57:04 2022 daemon.err openvpn(sample_server)[22712]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:04 2022 daemon.warn openvpn(sample_server)[22712]: Use --help for more information.
Sat Dec 10 21:57:09 2022 daemon.err openvpn(sample_server)[22713]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:09 2022 daemon.warn openvpn(sample_server)[22713]: Use --help for more information.
Sat Dec 10 21:57:14 2022 daemon.err openvpn(sample_server)[22714]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:14 2022 daemon.warn openvpn(sample_server)[22714]: Use --help for more information.
Sat Dec 10 21:57:19 2022 daemon.err openvpn(sample_server)[22715]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:19 2022 daemon.warn openvpn(sample_server)[22715]: Use --help for more information.
Sat Dec 10 21:57:24 2022 daemon.err openvpn(sample_server)[22716]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:24 2022 daemon.warn openvpn(sample_server)[22716]: Use --help for more information.
Sat Dec 10 21:57:29 2022 daemon.err openvpn(sample_server)[22717]: Options error: --server directive network/netmask combination is invalid
Sat Dec 10 21:57:29 2022 daemon.warn openvpn(sample_server)[22717]: Use --help for more information.
root@OpenWrt:~#
Let's see the following files:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
cat /etc/config/openvpn
Thanks for your time, my network :
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd7d:9daf:db85::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan4'
option ipv6 '0'
option mtu '1500'
option macaddr 'D8:EC:5E:44:01:4B'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'HOME'
option proto 'static'
option device 'lan3'
option ipaddr '10.0.1.254'
option netmask '255.255.255.0'
list dns '208.67.222.222'
list dns '208.67.220.220'
option type 'bridge'
config interface 'DMZ'
option proto 'static'
option ipaddr '10.0.0.254'
option netmask '255.255.255.0'
option device 'DMZ'
list dns '208.67.222.222'
list dns '208.67.220.220'
config device
option type 'bridge'
option name 'DMZ'
list ports 'lan1'
list ports 'lan2'
option ipv6 '0'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'lan1'
option ipv6 '0'
config device
option name 'wan'
option ipv6 '0'
config device
option name 'lan3'
option ipv6 '0'
config device
option name 'lan2'
option ipv6 '0'
config device
option name 'wlan0'
option ipv6 '0'
config device
option name 'wlan1'
option ipv6 '0'
config interface 'WIFI2'
option proto 'static'
list ipaddr '10.0.2.126/25'
option device 'wlan0'
config interface 'WIFI5'
option proto 'static'
list ipaddr '10.0.2.254/25'
option device 'wlan1'
config interface 'VPN'
option proto 'static'
option device 'tun0'
list ipaddr '10.0.3.254/24'
My firewall :
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone 'lan'
option name 'DMZ'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
list network 'DMZ'
list device 'tun+'
config zone 'wan'
option input 'ACCEPT'
option output 'ACCEPT'
option name 'WAN'
option masq '1'
option forward 'ACCEPT'
list network 'wan'
config forwarding
option src 'DMZ'
option dest 'WAN'
config zone
option name 'WIFI'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
config forwarding
option src 'WIFI'
option dest 'WAN'
config rule
option name 'ALL'
option dest 'WAN'
option target 'ACCEPT'
list proto 'all'
option src '*'
config zone
option name 'HOME'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
list network 'HOME'
list network 'WIFI2'
list network 'WIFI5'
config forwarding
option src 'HOME'
option dest 'WAN'
config forwarding
option src 'WAN'
option dest 'DMZ'
config forwarding
option src 'WAN'
option dest 'HOME'
config forwarding
option src 'WAN'
option dest 'WIFI'
config rule
option name 'ALL /'
list proto 'all'
option src 'WAN'
option dest '*'
option target 'ACCEPT'
config forwarding
option src 'DMZ'
option dest 'HOME'
config forwarding
option src 'HOME'
option dest 'DMZ'
config redirect
option dest 'DMZ'
option target 'DNAT'
option name 'REVERSE PROXY'
list proto 'tcp'
option src 'WAN'
option src_dport '443'
option dest_port '443'
option enabled '0'
config redirect
option dest 'WAN'
option target 'DNAT'
option name 'REVERSE PROXY'
list proto 'tcp'
option src 'DMZ'
option src_dport '443'
option dest_port '443'
option enabled '0'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
option src '*'
option dest '*'
config zone
option name 'VPN'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'VPN'
option masq '1'
config forwarding
option src 'VPN'
option dest 'HOME'
config forwarding
option src 'VPN'
option dest 'WAN'
config forwarding
option src 'HOME'
option dest 'VPN'
config forwarding
option src 'WAN'
option dest 'VPN'
I have all accept for test and my openvpn :
config openvpn 'custom_config'
option config '/etc/openvpn/my-vpn.conf'
config openvpn 'sample_server'
option port '1194'
option proto 'udp'
option dev 'tun'
option ifconfig_pool_persist '/tmp/ipp.txt'
option keepalive '10 120'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option status '/tmp/openvpn-status.log'
option verb '3'
option ca '/etc/openvpn/server.conf'
option dh '/etc/openvpn/server.conf'
option cert '/etc/openvpn/server.conf'
option key '/etc/openvpn/server.conf'
option enabled '1'
option server '10.0.3.0 255.255.255.0'
config openvpn 'sample_client'
option client '1'
option dev 'tun'
option proto 'udp'
list remote 'my_server_1 1194'
option resolv_retry 'infinite'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/client.crt'
option key '/etc/openvpn/client.key'
option verb '3'
Sat Dec 10 22:08:27 2022 daemon.warn openvpn(sample_server)[4692]: --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: OpenVPN 2.5.7 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: library versions: OpenSSL 1.1.1s 1 Nov 2022, LZO 2.10
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_best_gw result: via 82.66.85.254 dev wan
Sat Dec 10 22:08:27 2022 daemon.warn openvpn(sample_server)[4692]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: Diffie-Hellman initialized with 2048 bit key
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_best_gw result: via 82.66.85.254 dev wan
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: TUN/TAP device tun1 opened
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_iface_mtu_set: mtu 1500 for tun1
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_iface_up: set tun1 up
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_addr_ptp_v4_add: 10.0.3.1 peer 10.0.3.2 dev tun1
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: /usr/libexec/openvpn-hotplug up sample_server tun1 1500 1621 10.0.3.1 10.0.3.2 init
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_add: 10.0.3.0/24 via 10.0.3.2 dev [NULL] table 0 metric -1
Sat Dec 10 22:08:27 2022 daemon.warn openvpn(sample_server)[4692]: Could not determine IPv4/IPv6 protocol. Using AF_INET
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: Socket Buffers: R=[212992->212992] S=[212992->212992]
Sat Dec 10 22:08:27 2022 daemon.err openvpn(sample_server)[4692]: TCP/UDP: Socket bind failed on local address [AF_INET][undef]:1194: Address in use (errno=98)
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: Exiting due to fatal error
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_route_v4_del: 10.0.3.0/24 via 10.0.3.2 dev [NULL] table 0 metric -1
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: Closing TUN/TAP interface
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: net_addr_ptp_v4_del: 10.0.3.1 dev tun1
Sat Dec 10 22:08:27 2022 daemon.notice openvpn(sample_server)[4692]: /usr/libexec/openvpn-hotplug down sample_server tun1 1500 1621 10.0.3.1 10.0.3.2 init
This is wrong. You don't actually need to declare this here, but if you do, you must use "unmanaged" (proto none) in this locaiton.
You have other issues, too (unrelated to OpenVPN).
the option type 'bridge' declaration does not belong here. If you need a bridge, it must be defined outside the interface stanza.
wlan physical interfaces should never be declared here. You attach the wifi to the desired network in the wireles config file.
remove the device definitions here -- again, this should never be done in the network config file. Only in wireless.
This is very dangerous... you've exposed your entire router to the internet.
Input and forward should be reject (or drop).
Also, the name should be lowercase.
The WIFI zone doesn't have any networks attached.... remove this.
and remove this because it is now useless.
What is this for? This is a very bad rule because it exposes your router to the internet. Remove it.
Why do you have masquerading enabled here?
Delete all of these. NEVER forward from the wan to any of your networks.
Another dangerous/bad rule. Delete it.
There are still other issues.... but do everything I described and then post again.
Thanks you again,
Now :
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd7d:9daf:db85::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan4'
option ipv6 '0'
option mtu '1500'
option macaddr 'D8:EC:5E:44:01:4B'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'HOME'
option proto 'static'
option device 'lan3'
option ipaddr '10.0.1.254'
option netmask '255.255.255.0'
list dns '208.67.222.222'
list dns '208.67.220.220'
config interface 'DMZ'
option proto 'static'
option ipaddr '10.0.0.254'
option netmask '255.255.255.0'
option device 'DMZ'
list dns '208.67.222.222'
list dns '208.67.220.220'
config device
option type 'bridge'
option name 'DMZ'
list ports 'lan1'
list ports 'lan2'
option ipv6 '0'
config device
option name 'eth0'
option ipv6 '0'
config device
option name 'lan1'
option ipv6 '0'
config device
option name 'wan'
option ipv6 '0'
config device
option name 'lan3'
option ipv6 '0'
config device
option name 'lan2'
option ipv6 '0'
config device
option name 'wlan0'
option ipv6 '0'
config device
option name 'wlan1'
option ipv6 '0'
config interface 'WIFI2'
option proto 'static'
list ipaddr '10.0.2.126/25'
option device 'wlan0'
config interface 'WIFI5'
option proto 'static'
list ipaddr '10.0.2.254/25'
option device 'wlan1'
config device
option name 'tun0'
option macaddr 'D8:EC:5E:44:01:4A'
option ipv6 '0'
Firewall :
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone 'lan'
option name 'DMZ'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
list network 'DMZ'
list device 'tun+'
config forwarding
option src 'DMZ'
option dest 'WAN'
config zone
option name 'WIFI'
option input 'ACCEPT'
option output 'ACCEPT'
option masq '1'
option forward 'ACCEPT'
config forwarding
option src 'HOME'
option dest 'WAN'
config forwarding
option src 'DMZ'
option dest 'HOME'
config forwarding
option src 'HOME'
option dest 'DMZ'
config redirect
option dest 'DMZ'
option target 'DNAT'
option name 'REVERSE PROXY'
list proto 'tcp'
option src 'WAN'
option src_dport '443'
option dest_port '443'
option enabled '0'
config redirect
option dest 'WAN'
option target 'DNAT'
option name 'REVERSE PROXY'
list proto 'tcp'
option src 'DMZ'
option src_dport '443'
option dest_port '443'
option enabled '0'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option dest_port '1194'
option proto 'udp'
option target 'ACCEPT'
option src '*'
option dest '*'
config zone
option name 'VPN'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'VPN'
option masq '1'
config forwarding
option src 'VPN'
option dest 'HOME'
config forwarding
option src 'VPN'
option dest 'WAN'
config forwarding
option src 'HOME'
option dest 'VPN'
config forwarding
option src 'WAN'
option dest 'VPN'
config openvpn 'custom_config'
option config '/etc/openvpn/my-vpn.conf'
config openvpn 'sample_server'
option port '1194'
option proto 'udp'
option dev 'tun'
option ifconfig_pool_persist '/tmp/ipp.txt'
option keepalive '10 120'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option status '/tmp/openvpn-status.log'
option verb '3'
option ca '/etc/openvpn/server.conf'
option dh '/etc/openvpn/server.conf'
option cert '/etc/openvpn/server.conf'
option key '/etc/openvpn/server.conf'
option enabled '1'
option server '10.0.3.0 255.255.255.0'
config openvpn 'sample_client'
option client '1'
option dev 'tun'
option proto 'udp'
list remote 'my_server_1 1194'
option resolv_retry 'infinite'
option nobind '1'
option persist_key '1'
option persist_tun '1'
option user 'nobody'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/client.crt'
option key '/etc/openvpn/client.key'
option verb '3'
Sat Dec 10 22:30:39 2022 daemon.notice openvpn(sample_server)[15182]: /usr/libexec/openvpn-hotplug down sample_server tun1 1500 1621 10.0.3.1 10.0.3.2 init
Sat Dec 10 22:30:44 2022 daemon.warn openvpn(sample_server)[15217]: WARNING: --topology net30 support for server configs with IPv4 pools will be removed in a future release. Please migrate to --topology subnet as soon as possible.
Sat Dec 10 22:30:44 2022 daemon.warn openvpn(sample_server)[15217]: --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: OpenVPN 2.5.7 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: library versions: OpenSSL 1.1.1s 1 Nov 2022, LZO 2.10
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_best_gw result: via 82.66.85.254 dev wan
Sat Dec 10 22:30:44 2022 daemon.warn openvpn(sample_server)[15217]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: Diffie-Hellman initialized with 2048 bit key
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_best_gw query: dst 0.0.0.0
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_best_gw result: via 82.66.85.254 dev wan
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: TUN/TAP device tun1 opened
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_iface_mtu_set: mtu 1500 for tun1
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_iface_up: set tun1 up
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_addr_ptp_v4_add: 10.0.3.1 peer 10.0.3.2 dev tun1
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: /usr/libexec/openvpn-hotplug up sample_server tun1 1500 1621 10.0.3.1 10.0.3.2 init
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_add: 10.0.3.0/24 via 10.0.3.2 dev [NULL] table 0 metric -1
Sat Dec 10 22:30:44 2022 daemon.warn openvpn(sample_server)[15217]: Could not determine IPv4/IPv6 protocol. Using AF_INET
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: Socket Buffers: R=[212992->212992] S=[212992->212992]
Sat Dec 10 22:30:44 2022 daemon.err openvpn(sample_server)[15217]: TCP/UDP: Socket bind failed on local address [AF_INET][undef]:1194: Address in use (errno=98)
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: Exiting due to fatal error
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_route_v4_del: 10.0.3.0/24 via 10.0.3.2 dev [NULL] table 0 metric -1
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: Closing TUN/TAP interface
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: net_addr_ptp_v4_del: 10.0.3.1 dev tun1
Sat Dec 10 22:30:44 2022 daemon.notice openvpn(sample_server)[15217]: /usr/libexec/openvpn-hotplug down sample_server tun1 1500 1621 10.0.3.1 10.0.3.2 init
I know about rules wan -> lan but it's for my test, I will modify firewall later when all it's OK
Do you have one other idea ?
Remove all the wlan stuff.... delete the devices, remove the line from the wifi interfaces.
remove this whole thing:
Remove all of the VPN stuff form the firewall -- you don't have a network interface for this anymore.
Delete the following -- it has no purpose:
Now, delete all of this (you no longer have a firewall zone called home)
You know what...
honestly, this configuration has so many issues that I would recommend starting from scratch. Just reset your router to defaults and start over.
If I delete wifi interface, how can I propose ip static to my wifi devices ?
If I delete masquerading to my wan -> home I can't have acces to internet. Do you know th reason ?
After a reboot my openvpn server is now up but can't connect to him.
I'm cheking log
I'm not telling you to delete your wifi network interfaces, I'm saying you have a firewall zone that called WIFI that doesn't have any associated networks and is thus useless.
Masquerading should only be enabled on the wan zone.
Honestly, not worth it.
Just reset. You have too many problems in your configuration and you'll be better served by starting over. The current configuration is a mess.
I'm learning in the same time testing...
I have passed two days to config and to have internet in my home, I have to configure my reverse proxy next day but the problem that it's very complicate to have openvpn on openwrt.
I can have it up on 1mn on my nas and on 2mn in my other server.
I think that it's better to have one other server for my openvpn and create a VLAN with openwrt or something like that ..
I will perform my rules and network
Nothing wrong with this, in principle. However, you’ve made many mistakes and you have made you network too complicated by trying to do everything at once while you are learning. You need to start small/simple and make sure each step is correct before moving to the next.
Almost everything you have done has some error associated with it. That is why resetting is the best option.