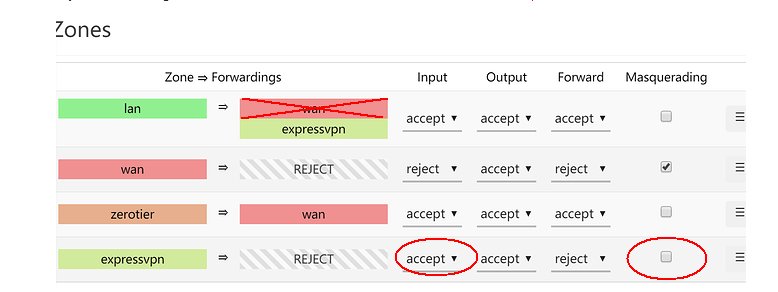
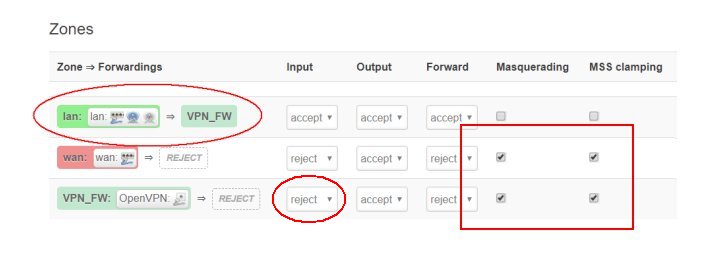
Thanks ,kill for keeping this post alive. This is what I did tonight on Linksys WRT3200ACM on David502 build (4.19.69-OpenWrt SNAPSHOT r10899-1c0290c5cc / LuCI Master (git-19.241.65047-dffe9ca)
- corrected the errors in the firewall file as you mentioned
- disabled WAN6
- added extra DNS by using
uci add_list dhcp.lan.dhcp_option='6,8.8.8.8,8.8.4.4'
uci commit
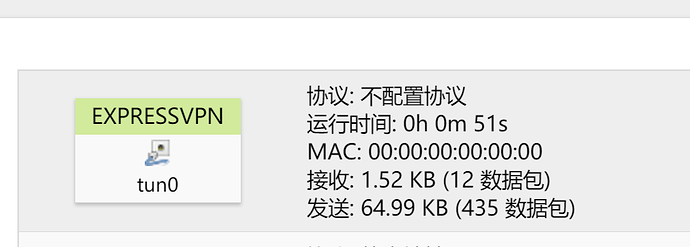
Then I started the OpenVPN , againt VPN is up and runing like a charm, but there is no internet connection at all. I can see that "tun0" is sending and receiving data.
root@OpenWrt:~# openvpn --cd /etc/openvpn --config /etc/openvpn/my_expressvpn_ho
ng_kong_-_2_udp.ovpn
Thu Sep 19 22:25:15 2019 WARNING: --keysize is DEPRECATED and will be removed in OpenVPN 2.6
Thu Sep 19 22:25:15 2019 OpenVPN 2.4.7 arm-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
Thu Sep 19 22:25:15 2019 library versions: OpenSSL 1.1.1c 28 May 2019, LZO 2.10
Thu Sep 19 22:25:15 2019 WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
Thu Sep 19 22:25:15 2019 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Sep 19 22:25:15 2019 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Sep 19 22:25:15 2019 TCP/UDP: Preserving recently used remote address: [AF_INET]45.56.152.81:1195
Thu Sep 19 22:25:15 2019 Socket Buffers: R=[163840->1048576] S=[163840->1048576]
Thu Sep 19 22:25:15 2019 UDP link local: (not bound)
Thu Sep 19 22:25:15 2019 UDP link remote: [AF_INET]45.56.152.81:1195
Thu Sep 19 22:25:15 2019 TLS: Initial packet from [AF_INET]45.56.152.81:1195, sid=ead074ab 91eaa9c9
Thu Sep 19 22:25:15 2019 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
Thu Sep 19 22:25:15 2019 VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com
Thu Sep 19 22:25:15 2019 VERIFY OK: nsCertType=SERVER
Thu Sep 19 22:25:15 2019 VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-990-2a, emailAddress=support@expressvpn.com
Thu Sep 19 22:25:15 2019 VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-990-2a, emailAddress=support@expressvpn.com
Thu Sep 19 22:25:15 2019 Control Channel: TLSv1.2, cipher TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Thu Sep 19 22:25:15 2019 [Server-990-2a] Peer Connection Initiated with [AF_INET]45.56.152.81:1195
Thu Sep 19 22:25:16 2019 SENT CONTROL [Server-990-2a]: 'PUSH_REQUEST' (status=1)
Thu Sep 19 22:25:16 2019 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.55.0.1,comp-lzo no,route 10.55.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.55.0.50 10.55.0.49,peer-id 6,cipher AES-256-GCM'
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: timers and/or timeouts modified
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: compression parms modified
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: --ifconfig/up options modified
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: route options modified
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: peer-id set
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: adjusting link_mtu to 1629
Thu Sep 19 22:25:16 2019 OPTIONS IMPORT: data channel crypto options modified
Thu Sep 19 22:25:16 2019 Data Channel: using negotiated cipher 'AES-256-GCM'
Thu Sep 19 22:25:16 2019 NCP: overriding user-set keysize with default
Thu Sep 19 22:25:16 2019 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Thu Sep 19 22:25:16 2019 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Thu Sep 19 22:25:16 2019 TUN/TAP device tun0 opened
Thu Sep 19 22:25:16 2019 TUN/TAP TX queue length set to 100
Thu Sep 19 22:25:16 2019 /sbin/ifconfig tun0 10.55.0.50 pointopoint 10.55.0.49 mtu 1500
Thu Sep 19 22:25:18 2019 /sbin/route add -net 45.56.152.81 netmask 255.255.255.255 gw 202.187.160.1
Thu Sep 19 22:25:18 2019 /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.55.0.49
Thu Sep 19 22:25:18 2019 /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.55.0.49
Thu Sep 19 22:25:18 2019 /sbin/route add -net 10.55.0.1 netmask 255.255.255.255 gw 10.55.0.49
Thu Sep 19 22:25:18 2019 Initialization Sequence Completed
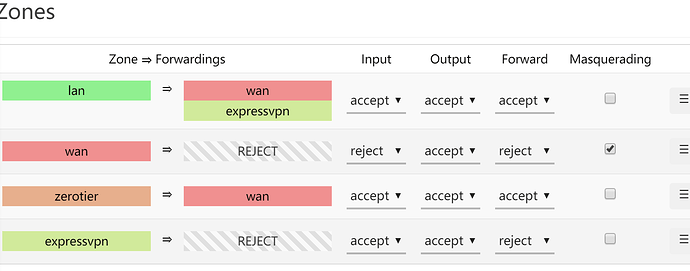
my firewall configuration is like this
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
list device 'eth0'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option network 'wan6 wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'bcp38'
option type 'script'
option path '/usr/lib/bcp38/run.sh'
option family 'IPv4'
option reload '1'
config redirect
option target 'DNAT'
option name 'Router'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.1'
option dest_port '443'
option src_dport '555'
config redirect
option target 'DNAT'
option name 'ESXi'
option proto 'tcp udp'
option src 'wan'
option src_dport '666'
option dest 'lan'
option dest_ip '192.168.1.106'
option dest_port '443'
config redirect
option target 'DNAT'
option name 'Remote windows desktop'
option proto 'tcp udp'
option src 'wan'
option src_dport '777'
option dest 'lan'
option dest_ip '192.168.1.201'
option dest_port '3389'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option name 'Web HTTP'
option dest_ip '192.168.1.214'
option src_dport '80'
option dest_port '80'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_port '443'
option name 'Web HTTPS'
option dest_ip '192.168.1.214'
option src_dport '443'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option src_dport '999'
option dest 'lan'
option dest_ip '192.168.1.159'
option dest_port '5000'
option name 'DSM_621'
config redirect
option target 'DNAT'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_port '5901'
option name 'Centos RD'
option src_dport '5901'
option dest_ip '192.168.1.214'
config redirect
option target 'DNAT'
option name 'Debian RD'
option proto 'tcp udp'
option src 'wan'
option src_dport '5902'
option dest 'lan'
option dest_ip '192.168.1.144'
option dest_port '5901'
config redirect
option target 'DNAT'
option name 'Ubuntu'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option src_dport '5903'
option dest_port '5901'
option dest_ip '192.168.1.210'
config redirect
option target 'DNAT'
option name 'MintLinux'
option proto 'tcp udp'
option src 'wan'
option src_dport '5904'
option dest 'lan'
option dest_port '5900'
option dest_ip '192.168.1.195'
config redirect
option target 'DNAT'
option name 'ClearOS'
option proto 'tcp udp'
option src 'wan'
option src_dport '5905'
option dest 'lan'
option dest_port '81'
option dest_ip '192.168.1.172'
config redirect
option target 'DNAT'
option name 'SSH'
option proto 'tcp udp'
option src 'wan'
option src_dport '22'
option dest 'lan'
option dest_ip '192.168.1.1'
option dest_port '22'
config zone
option name 'zerotier'
option input 'ACCEPT'
option output 'ACCEPT'
option network 'Zerotier'
option forward 'ACCEPT'
config forwarding
option src 'zerotier'
option dest 'wan'
config redirect
option target 'DNAT'
option name 'ESXi SSH'
option proto 'tcp udp'
option src 'wan'
option src_dport '23'
option dest 'lan'
option dest_ip '192.168.1.106'
option dest_port '22'
config rule
option name 'FTP'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option dest_port '10060-10090'
config rule
option proto 'tcp udp'
option src 'wan'
option src_port '21'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option name 'Transmission'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.1'
option src_dport '9091'
option dest_port '9091'
config redirect
option target 'DNAT'
option name 'FTP'
option proto 'tcp udp'
option src 'wan'
option src_dport '21'
option dest 'lan'
option dest_ip '192.168.1.1'
option dest_port '21'
config redirect
option target 'DNAT'
option name 'FTP passive'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.1'
option dest_port '10060-10090'
option src_dport '10060-10090'
config redirect
option target 'DNAT'
option name 'DSM FTP'
option proto 'tcp udp'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.159'
option dest_port '21'
option src_dport '24'
config forwarding
option src 'lan'
option dest 'wan'
config redirect
option target 'DNAT'
option name 'DSM FTP Passive'
option proto 'tcp udp'
option src 'wan'
option src_dport '55536-56559'
option dest 'lan'
option dest_ip '192.168.1.159'
option dest_port '55536-56559'
config zone
option name 'expressvpn'
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option network 'expressvpn'
config forwarding
option src 'lan'
option dest 'expressvpn'