Your router should be configured as a VPN client.
Please pardon my ignorance, but there are several options I show in the screenshot of the LuCI VPN section, top of this page.
Your router should be configured as a VPN client.
Please pardon my ignorance, but there are several options I show in the screenshot of the LuCI VPN section, top of this page.
It seems you have been struggling with this for 2 months without success.
You might consider contacting someone locally who has experience, and can sit with you and configure it with you.
Not true, jwoods. I bricked 3 of the 4 routers. I have had success, as I have got enough knowledge to start asking questions that aren't half so nebulous as months ago. Thank you for thinking of me, never the less.
I certainly appreciate the learning experience.
However, if the goal is to get a working VPN connection, it has not happened, despite the time and best efforts of highly experienced users.
For instance, I learned but today, that I will need a static IP or a service of a dynamic DNS provider. I'm reading up on that now.
And FYI, nowhere have I found the outline of what is needed for VPNing. I would write it up, if I were a good technical writer. It would look about like this, in part, as this is as far as I've got so far.
Obtain an account from a VPN.
Obtain an account from a DDNS if your ISP won't allow a static IP or it costs more than a DDNS provider's service.
Obtain the .ovpn (or .tcp or what you like) from your VPN provider
Obtain the .ca from your VPN provider.
Obtain the Firewall "rules" and set them up for your specific requirements such as gaming.
Install such files as ssl-openvpn (this is by example, NOT a filename)
Nowhere, do I find a reasonably simple explanation of the foregoing. It's one thing to have that extensive page about OpenVPN configging at lede-project, another to not give an introduction sufficient to allow a member to get a leg up.
Thanks for your help.
The LEDE User Guide is the best starting point...
https://openwrt.org/docs/start
Specifically, the OpenVPN Client section...
https://openwrt.org/docs/user-guide/services/openvpn.client
It adequately describes how to set up an OpenVPN client...for LEDE.
The VPN provider will also have instructions on how to set up your client to work with their service.
The reason you don't find a "reasonably simple" explanation is that it is not a reasonably simple process.
LEDE does require configuration, more so than stock firmware...it is not plug and play.
It is not really geared towards absolute beginners.
If you are a subscriber to a commercial VPN service, they are the server. Your router will be a VPN client. You do not need static IP or dynamic DNS. Your VPN client connects to the server like you would any other site on the Internet. In other words, you will find them (by DNS looking up a name to an IP address and making an outgoing connection)-- they don't have to find you.
When you have an .ovpn file from the service with their suggested configuration, use it directly. Do not attempt to configure through LuCI. Reference the OpenVPN documentation directly for example at https://openvpn.net/index.php/open-source/documentation/howto.html
Thanks again. I know that this is more than a simple process. I still say that the broad outline is needed as stated in my previous response to you. FWIW, I've read several How-To's. One at OpenVPN another 2 at OpenWRT and LEDE Project. Very complex. Still one can only do one step at a time. Assuming the user isn't a squid with multiple arms and keyboards.
There are two big steps to setting up a VPN client. First is to get the OpenVPN process to run and connect to the server. When this is successful you will see "Initialization sequence completed" in the log and have a "tun0" (or some other name you can configure) device which leads out to the Internet via the VPN. Then you need to configure to route your traffic through the tunnel device.
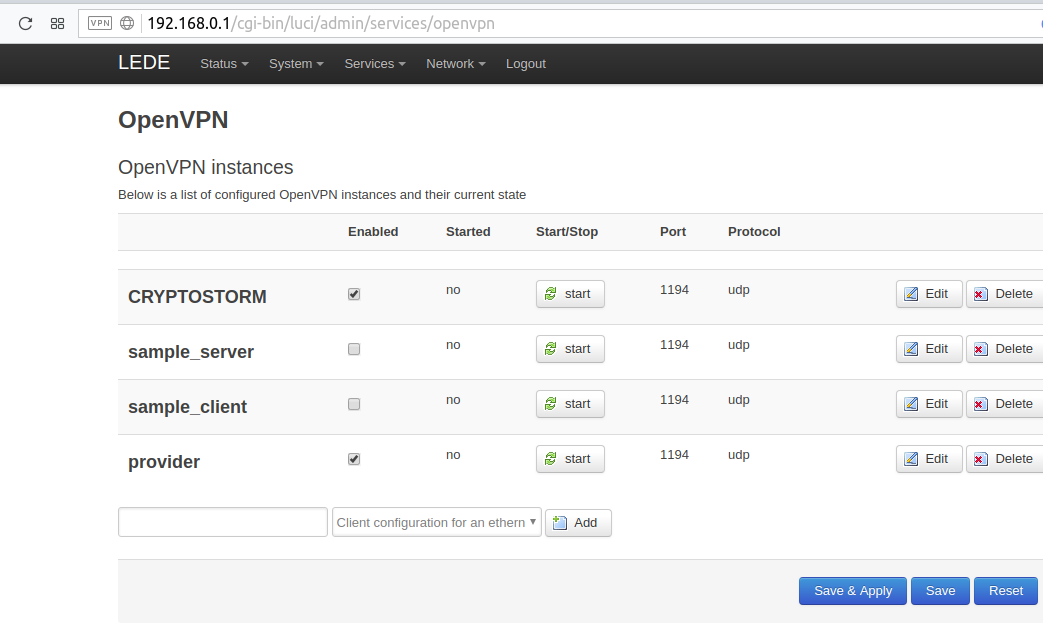
Here is what I see. I've tried to Start the 4 "Instances". The CRYPTOSTORM will start. The logs show all kinds of problems. You can see the entire log at:
https://paste.ubuntu.com/p/f4WfXK5Pcn/
In this post I'm mostly concerned about:
Sun Feb 18 21:56:07 2018 daemon.warn openvpn(CRYPTOSTORM)[19288]: WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
I have the most recent ca.crt. Any advice anyone?
ns-cert-type was depreciated something like a decade ago (the "ns" stands for NetScape [Browser]), so for the VPN provider, remote-crt-tls is to be utilized, of which requires a key usage of:
0xa0]: Digital Signature, Key Encipherment0x88]: Digital Signature, Key Agreement
#--------------------------------------------------------------------
##----- RFC 5280 4.2.1.3 -----##
#--------------------------------------------------------------------
# https://tools.ietf.org/html/rfc5280
# id-ce-keyUsage OBJECT IDENTIFIER ::= { id-ce 15 }
# KeyUsage ::= BIT STRING {
# digitalSignature (0),
# nonRepudiation (1),
# NOTE: Recent editions of X.509 have renamed this bit to contentCommitment
# keyEncipherment (2),
# dataEncipherment (3),
# keyAgreement (4),
# keyCertSign (5),
# cRLSign (6),
# encipherOnly (7),
# decipherOnly (8) }
The log doesn't show all kinds of problems, just the same problem over and over again...
{ERROR:} Options error: In [CMD-LINE]:1: Error opening configuration file: openvpn-provider.conf
{WARNING:} WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
Does the file openvpn-provider.conf exist? Have you specified the full path to it?
According to Tech Support at cryptostorm, this post: https://cryptostorm.org/viewtopic.php?t=9538
the "openvpn-provider.conf" is here: https://github.com/cryptostorm/cryptostorm_client_configuration_files/blob/master/linux/cstorm_linux-lisbon_udp.ovpn
and that file is in my /etc/openvpn/cstorm_linux-lisbon_udp.ovpn with 3 lines edited per a post this forum:
auth-user-pass /tmp/auth.conf
redirect-gateway def1
auth-nocache
Realize that /tmp is on a RAM disk and will be erased when rebooting. Also it is not recommended to name the userpass file .conf, This can get misinterpreted by OpenVPN scanning a directory for all .conf files.
" it is not recommended to name the userpass file .conf, This can get misinterpreted by OpenVPN scanning a directory for all .conf files."
sorry to necro this thread, but that is an important fact that can (and did in my case) bite you in the ass.
I had 3 .conf files in my openvpn folder (so if I wanted to I could just rename the etc/config/openvpn reference to use a different config...don't ask, long story)..anyway I couldn't understand why my vpn connection from my router was flaky as hell until I deleted 2 of the conf files, then things started behaving normally again.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.