Hi There,
I have following network situation...
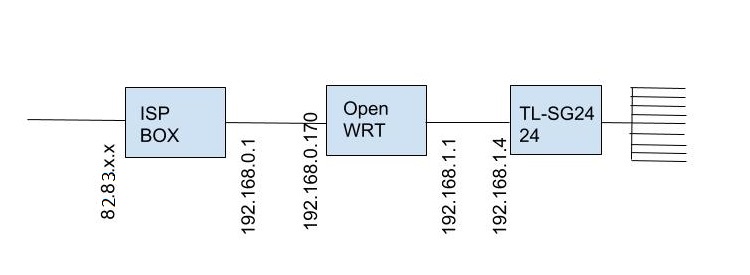
I finally managed to get OpenVPN working on my SNAPSHOT r8689-5beedcd.
The https://openwrt.org/docs/guide-user/services/vpn/openvpn/basic did the trick.
The first problem was getting out, my Belgian ISP Telenet uses a White CH7465LG-TN router only accessibly by their web page.(no 192.168.0.1 or other IP-adres that I'm aware off).
Although the websites tells you a port is open , one can't trust this answer.
I first tested the openvpn connection internally on 192.168.1.1 which worked so I new everything worked till that Iip address.
It's only after a reset from the ISP box that the ports also opened to the outside..
I have a QNAP nas behind this OpenWRT router en 2 IP camera's.
Unfortunately when I enter the ip address from cam1 nothing happens, also the ip address from the QNAP doesn't work.
The only thing that seems to work is the ip address from my openwrt router.
What I would like to achieve is to see my 2 camera's and eventually browse,play some music from NAS.
Can somebody point me out to my mistakes in my configurings?
Kind Regards
Guy F
root@OpenWrt:/# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@rule[7]=rule
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Allow SSL vpn in (tcp)'
firewall.@rule[9].src='wan'
firewall.@rule[9].proto='tcp'
firewall.@rule[9].dest_port='443'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].name='Allow SSL vpn in (udp)'
firewall.@rule[10].src='wan'
firewall.@rule[10].proto='udp'
firewall.@rule[10].dest_port='443'
firewall.@rule[10].target='ACCEPT'
firewall.@rule[11]=rule
firewall.@rule[11].name='Allow-OpenVPN'
firewall.@rule[11].src='wan'
firewall.@rule[11].dest_port='1194'
firewall.@rule[11].proto='tcp udp'
firewall.@rule[11].target='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='vpnserver'
firewall.@zone[2].network='vpnserver'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='vpnserver'
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='vpnserver'
firewall.@forwarding[2].dest='lan'
root@OpenWrt:/# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdf9:34d2:70fa::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan_dev=device
network.lan_dev.name='eth0.1'
network.lan_dev.macaddr='90:8d:78:xx:xx:xx'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='dhcp'
network.wan_dev=device
network.wan_dev.name='eth0.2'
network.wan_dev.macaddr='90:8d:78:xx:xx:xx'
network.wan6=interface
network.wan6.ifname='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='1 2 3 4 6t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='0 6t'
network.vpnserver=interface
network.vpnserver.ifname='tun0'
network.vpnserver.proto='none'