Hello! Im seeking for some help. Im using LEDE firmware on Ubiquiti Airgateway and I want to be able to have access to LEDE GUI through the WAN side of the Airgateway when I first flash it but by default LEDE firewall configuration wont let me have access through WAN only LAN. The idea is to edit the LEDE airgateway firmware so that every time I flash LEDE to a new Airgateway I immediately will have access through WAN (remotely). I speak spanish better so if there is someone who speaks spanish and can help me with this please PM me thanks!
I would suggest that they reply here - as others can benefit from the assistance, as well.
Basically what I need is the ubnt-air-gateway-squashfs-factory.bin image from LEDE 17.01.4 STABLE to have the firewall option called "option input" be set to ACCEPT and not REJECT. In the airgateway firmware this opcion is under wan6. Here is a picture of what Im talking about.
From what you describe, you must compile your own firmware, with the configuration above - customized to your needs. As, the config you desire seems like a security risk in most use cases.
Por favor, perdona mi español, es de Google Translate
Comprender su red ayudará a obtener una buena respuesta. Si su interfaz "WAN" es realmente para su red interna controlada, entonces abrir esa regla para HTTP (-S) puede tener sentido. Sería una importante violación de seguridad permitir el acceso externo a todos los puertos, o incluso solo a la interfaz LuCI (incluso con HTTPS).
¿Nos diría qué está conectado a la interfaz "WAN" y cómo controla esa red?
Si desea este comportamiento inmediatamente después del flash, tendrá que compilar su propio firmware.
Please forgive my Spanish, it is from Google Translate
Understanding your network will help in getting a good answer. If your "WAN" interface is actually to your controlled, internal network, then opening that rule for HTTP(-S) may make sense. It would be a major security breach to allow outside access to all ports, or even just the LuCI interface (even with HTTPS).
Would you let us know what is connected to the "WAN" interface and how you control that network?
If you want this behavior immediately after flash, you will need to compile your own firmware.
yes that is exactly what I want to do but I dont know how to edit and then compile the firmware  thats why I need someone who knows and has all the tools and experience needed to do this edit correctly.
thats why I need someone who knows and has all the tools and experience needed to do this edit correctly.
See:
https://openwrt.org/docs/guide-developer/build-system/start
No puedo recomendar el acceso a la interfaz de administración en la interfaz "WAN" si eso no es privado para su empresa. Si está conectado a una red privada que utiliza para administrar sus dispositivos, entonces ACCEPT solamente las conexiones a ssh y el puerto del servidor web. Si puede, también recomendaría el uso de una VLAN para fines de gestión. Recomiendo construir en luci-ssl (mbedTLS) oluci-ssl-openssl dependiendo de si usa OpenSSL para otros fines o no.
I cannot recommend allowing access to the management interface on the "WAN" interface if that is not private to your enterprise. If it is connected to a private network that you use to manage your devices, then I would only ACCEPT connections to ssh and the web server's port. If you can, I'd also recommend use of a VLAN for management purposes. I recommend building in either luci-ssl (mbedTLS) or luci-ssl-openssl depending on if you use OpenSSL for other purposes or not.
Buenas jeff, en mi caso el acceso por WAN no me trae problemas de seguridad ya que es manejo una red interna anda externa. Lo que quiero es tener una imagen que ya venga con acceso por la WAN pero el problema es que no se como editar y recompilar la imagen, no tengo ni la menor idea y cada vez que veo los pasos de como hacerlo me confundo. I managed a private home network so WAN access for my airgateways is not a issue for me :).
Hopefully, the link above will help. Following the custom compile step by step, and using the backup config file you make should be helpful.
Mejores deseos para usted.
¡Gracias por la aclaración!
Lleva un tiempo aprender el sistema de compilación, pero el proceso básico es:
- Instalar el sistema de compilación
- ejecutar
make menuconfig- Seleccione su arquitectura (Target System)
- Seleccione su tipo de dispositivo (Subtarget)
- Seleccione su dispositivo específico (Target Profile)
- Agregue LuCI => Collections => luci or luci-ssl or luci-ssl-openssl
- Guarde el resultado
make -jN clean download worlddonde N es la cantidad de hilos que quieres usar- Resuelva cualquier problema de compilación (es probable que falten utilidades en su caja de compilación)
- Verifique que el firmware se instale y se ejecute
Luego puede cambiar las opciones, como agregar paquetes que desea instalar. Una vez que tengas lo que quieres probar, ejecuta
make -jN download world
(ahorra tiempo de compilación)
Los archivos que agregue al directorio files se instalarán en la imagen. Para cosas como cambios en /etc /config, obtendría lo que desea de un AP en ejecución que haya configurado como quiera.
Thank you for clarifying!
It takes some time to learn the build system, but the basic process is to:
- Install the build system
- run
make menuconfig- Select your architecture (Target System)
- Select your device type (Subtarget)
- Select your specific device (Target Profile)
- Add LuCI => Collections => luci or luci-ssl or luci-ssl-openssl
- Save the result
make -jN clean download worldwhere N is the number of threads you want to use- Resolve any build problems (likely missing utilities on your build box)
- Check that the firmware installs and runs
You can then change the options, such as adding packages you want installed. Once you have what you want to try, run
make -jN download world
(saves some compile time)
Files you add to the files directory will be installed in the image. For things like changes to /etc/config I'd get what you want from a running AP that you've configured as you want.
Use the Image Builder, and pack in your custom config file, which will replace the default one.
This is faster, and also has the advantage that you are running the release kernel, which means you can later opkg install additional software from the release server rather than having to rebuild all packages yourself.
ok im making some progress, now Im able to compile the firmware on debian 64-bit, can I add a pre configured backup file to the LEDE image so that when I flash it to the airgateway all my settings are there? if yes, where should I put my backup file and in what format? with .tar.gz at the end of the backup file or do I need to extract it to a directory in the LEDE files folder??
You can do it through LuCI and the web interface or with the command line
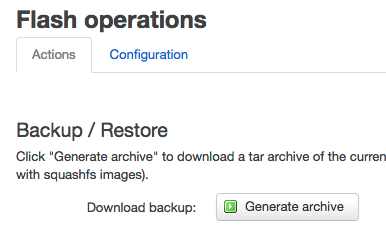
to download a backup to your local machine (for safety), then
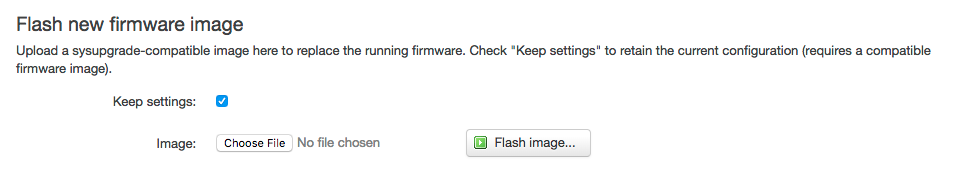
That should preserve your settings. You can check to see the files that will be saved first by either extracting the backup (tar), or by running
router # sysupgrade -l
If there are files "missing" from the list that you want to save, you can edit /etc/sysupgrade.conf Most of the system and packages' config files are saved. Mine looks like this:
## This file contains files and directories that should
## be preserved during an upgrade.
# /etc/example.conf
# /etc/openvpn/
/etc/.git
/etc/.gitignore
/etc/ethers
/etc/mac80211-post-add.sh
/root
/home
(I run with a non-root user and use sudo -- /home is non-standard)
I typically use the command line (without downloading a backup first, as I backup in other ways)
build-box $ scp path/to/openwrt-ar71xx-generic-archer-c7-v2-squashfs-sysupgrade.bin root@my.openwrt.router:/tmp/
build-box $ ssh root@my.openwrt.router
router # sysupgrade /tmp/openwrt-ar71xx-generic-archer-c7-v2-squashfs-sysupgrade.bin
ok Jeff thanks for the info :D. What I would like to do is to compile a LEDE firmware with my backup settings in it so that when I flash it to any airgateway the default settings are replaced by my backup settings. That way I dont even have to touch any configuration after flashing the firmware 
You can look through a downloaded backup and decide what you want to add.
The changes you make to the files on the device can be seen under /overlay/upper/
The file hierarchy under openwrt_build_system/files/ gets copied to the root of the device's firmware. Ownership seems to always be root:root and I haven't figured out how to get permissions to be anything but default.