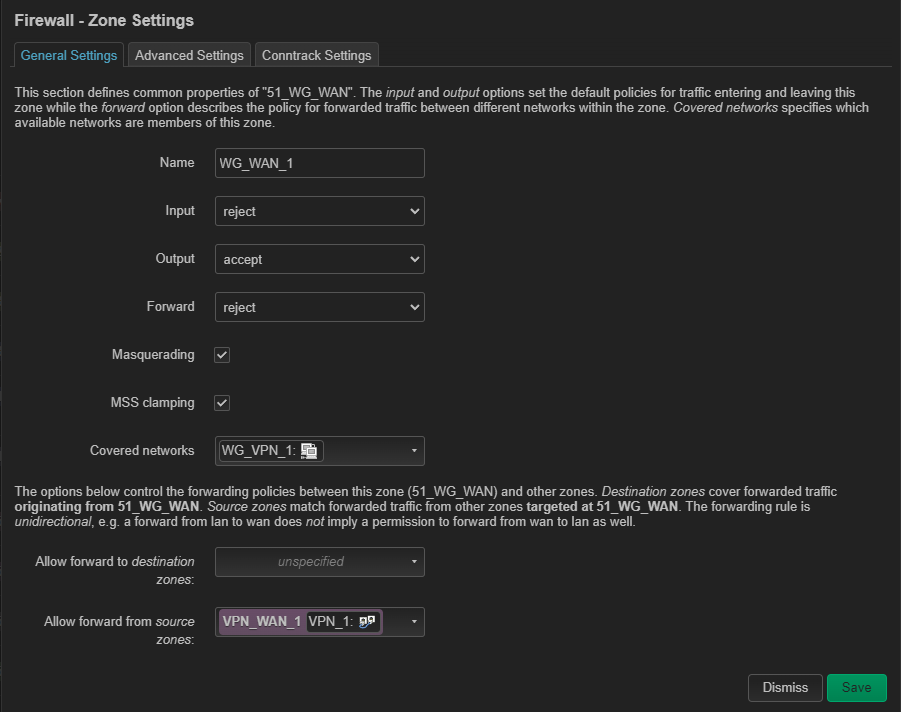
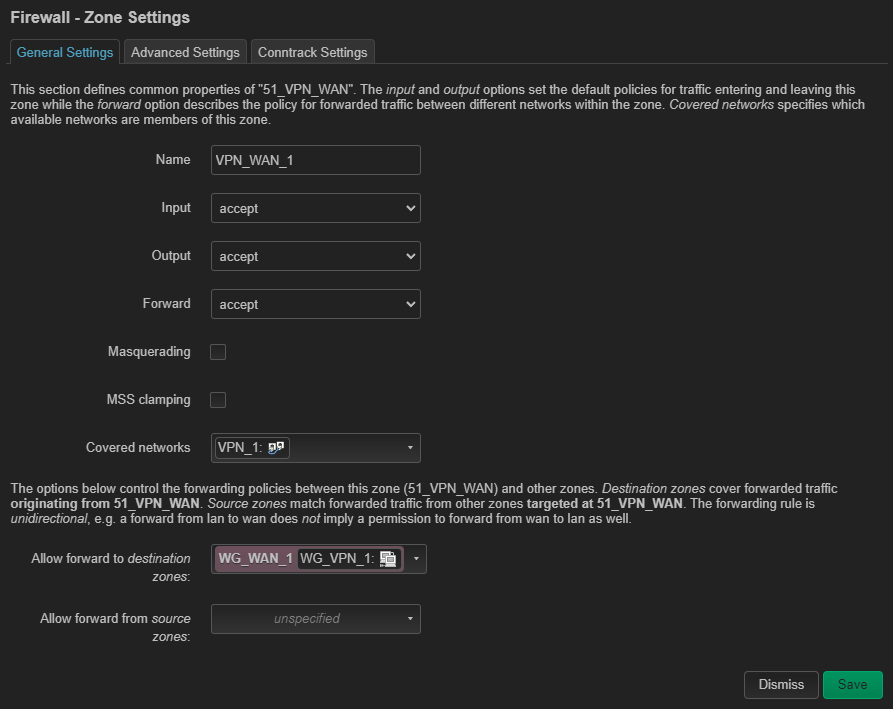
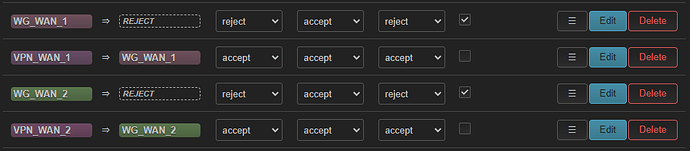
I am trying to setup 2 additional network interfaces (separate from lan) with VPN. Each interface should use a different VPN server (both from the same provider, Mullvad).
They are both setup in a very similar way, but only one ever worked at any given time.
At the moment, Interface #1 does not work: devices can connect to the interface, and they get an IP in the 10.10.10.X range, but they have no internet.
Interface #1 (which doesn't work currently):
config interface 'VPN_1'
option proto 'static'
option device 'br-vpn-1'
option netmask '255.255.255.0'
list dns '-PROVIDER DNS-'
option ipaddr '10.10.10.1'
config interface 'WG_VPN_1'
option proto 'wireguard'
option private_key '-PRIVATE KEY #1-'
option listen_port '51820'
list addresses '-PROVIDER IP #1-'
config wireguard_WG_VPN_1
option public_key '-REDACTED-'
list allowed_ips '0.0.0.0/0'
option endpoint_host '-REDACTED-'
option endpoint_port '51820'
option description '-REDACTED-'
config rule
option in 'VPN_1'
option lookup '1742'
config route
option interface 'WG_VPN_1'
option target '0.0.0.0'
option netmask '0.0.0.0'
option table '1742'
Interface #2 (which works):
config interface 'VPN_2'
option proto 'static'
option device 'br-vpn-2'
option ipaddr '10.10.12.1'
option netmask '255.255.255.0'
list dns '-PROVIDER DNS-'
config interface 'WG_VPN_2'
option proto 'wireguard'
option private_key '-PRIVATE KEY #2-'
option listen_port '51820'
list addresses '-PROVIDER IP #2-'
config wireguard_WG_VPN_2
option description '-REDACTED-'
option public_key '-REDACTED-'
list allowed_ips '0.0.0.0/0'
option endpoint_host '-REDACTED-'
option endpoint_port '51820'
config rule
option in 'VPN_2'
option lookup '1743'
config route
option interface 'WG_VPN_2'
option target '0.0.0.0'
option netmask '0.0.0.0'
option table '1743'
Is there something obvious that I am missing?