nslookup from a PC connected to OpenWRT router returns the following
nslookup r5-pc.s3.amazonaws.com
Server: OpenWrt.FakeLanName
Address: fxxx:xxxx:xxxx::1
*** OpenWrt.FakeLanName can't find r5-pc.s3.amazonaws.com: Non-existent domain
WireShark shows;
Flags: 0x8183 Standard query response, No such name
R5-pc.s3.amazonaws.com: type AAAA, class IN
Internet Control Message Protocol v6
Type: Destination Unreachable (1)
Code: 4 (Port unreachable)
Checksum: 0x7549 [correct]
[Checksum Status: Good]
Reserved: 00000000
Source: OpenWRT
Destination: IPv6 address of PC
User Datagram Protocol, Src Port: 53, Dst Port: 63689
This doesn't happen with any other names that I am aware of.
nslookup directly connected to SurfBoard Modem returns
nslookup r5-pc.s3.amazonaws.com
Server: dns-my-isp.com
Address: 2xx.xxx.xxx.xxx
Non-authoritative answer:
Name: s3-us-west-2-w.amazonaws.com
Address: 52.218.232.203
Aliases: r5-pc.s3.amazonaws.com
What would cause this FQDN to fail but everything else appears to resolve correctly?
What happens if you directly look up the name using 1.1.1.1 or 8.8.8.8 as the DNS server? Give the server address as the second argument to nslookup
1 Like
Looks like a recursion / ipsec issue..... That or some sort of 4/6 confusion on the resolver side.
Try firing up the nameserver in debug / interactive mode with max debug....
Also post all your config files for your resolver, specifically any file it uses to determine forwarders or root hints, protocol selection and dnssecurity.
@dlakelan
PS C:\Users\NotMyRealName> nslookup
server 1.1.1.1
r5-pc.s3.amazonaws.com
*** one.one.one.one can't find r5-pc.s3.amazonaws.com : Non-existent domain
server 8.8.8.8google-public-dns-a.google.com
r5-pc.s3.amazonaws.com google-public-dns-a.google.com
*** google-public-dns-a.google.com can't find r5-pc.s3.amazonaws.com : Non-existent domain
@anon50098793
try
nslookup -type=soa amazonaws.com
or
nslookup -type=soa s3.amazonaws.com
from/via wrt (server 1.1.1.1)
if you are returned an origin for s3, use nslookup interactive to point your resolver to the authoritative ns ( origin );
nslookup [ENTER]
server ns-1726.awsdns-23.co.uk [ENTER]
r5-pc.s3.amazonaws.com [ENTER]
i'm now thinking geo-cism....
nslookup r5-pc.s3.amazonaws.com 1.1.1.1
nslookup r5-pc.s3.amazonaws.com 8.8.8.8
@dlakelan
@anon50098793
So either the domain doesn't exist, or the global DNS system is out of sync with the authoritative system for that domain.
In the original thread I mentioned that connecting directly to my cable modem, it returns and IP address
Trying to figure out why it would not when connected to the router
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com
Server: 127.0.0.1
Address: 127.0.0.1#53
Name: R5-pc.s3.amazonaws.com
R5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
Name: s3-us-west-2-w.amazonaws.com
Address 1: 52.218.217.51
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
What are your WAN settings?
Have you manually entered a DNS server on WAN?
You never responded to @vgaetera 's post.
I think so. Seems like a Geo entry.
some ISPs will often return fake DNS entries unfortunately, they redirect you to their own advertisement sponsors or stuff... so just because your ISP returns an IP doesn't mean it's accurate
I'm at home so I looked it up at my home network:
host r5-pc.s3.amazonaws.com
r5-pc.s3.amazonaws.com is an alias for s3-us-west-2-w.amazonaws.com.
s3-us-west-2-w.amazonaws.com has address 52.218.212.202
so looks legit and it's probably your local resolver isn't in sync yet, this probably goes away after a while.
@vgaetera @lleachii
root@OpenWrt:~# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fdxx:xxxx:xxxx::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.ifname='eth1'
network.wan.proto='dhcp'
network.wan.peerdns='0'
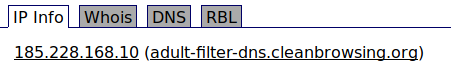
network.wan.dns='185.228.168.10 185.228.169.11'
network.wan6=interface
network.wan6.ifname='eth1'
network.wan6.proto='dhcpv6'
network.wan6.reqaddress='try'
network.wan6.reqprefix='auto'
network.wan6.peerdns='0'
network.wan6.dns='2a0d:2a00:1::1 2a0d:2a00:2::1'
root@OpenWrt:~#
Change these to working DNS servers.
BTW:
the IPv4 DNS IPs (by their reverse name) appear to do some form of content blocking - this may be an issue
the IPv6 DNS IPs seem to be controlled by a private individual. If you don't know who that is, definitely change those
Those are Cleanbrowsing DNS servers. They do provide content filtering.
Have you tried changing these servers and testing again?
You do realize that the link you posted says "filters," correct? ~
lleachii:
(by their reverse name)
1 Like
Check from the router:
nslookup r5-pc.s3.amazonaws.com
nslookup r5-pc.s3.amazonaws.com 1.1.1.1
nslookup r5-pc.s3.amazonaws.com 8.8.8.8
It's either some Windows glitch/malware, or even more likely DNS hijacking.https://openwrt.org/docs/guide-user/services/dns/start#encryption
2 Likes
@vgaetera
Taken from the router
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com
Server: 127.0.0.1
Address: 127.0.0.1#53
** server can't find r5-pc.s3.amazonaws.com: NXDOMAIN
** server can't find r5-pc.s3.amazonaws.com: NXDOMAIN
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com 1.1.1.1
Server: 1.1.1.1
Address: 1.1.1.1#53
Name: r5-pc.s3.amazonaws.com
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
Name: s3-us-west-2-w.amazonaws.com
Address 1: 52.218.212.178
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Name: r5-pc.s3.amazonaws.com
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
Name: s3-us-west-2-w.amazonaws.com
Address 1: 52.218.196.162
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
I also tried with the Cleanbrowsing IPv6 servers
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com 2a0d:2a00:1::1
Server: 2a0d:2a00:1::1
Address: 2a0d:2a00:1::1#53
Name: r5-pc.s3.amazonaws.com
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
Name: s3-us-west-2-w.amazonaws.com
Address 1: 52.218.196.234
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
root@OpenWrt:~# nslookup r5-pc.s3.amazonaws.com 2a0d:2a00:2::1
Server: 2a0d:2a00:2::1
Address: 2a0d:2a00:2::1#53
Name: r5-pc.s3.amazonaws.com
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
Name: s3-us-west-2-w.amazonaws.com
Address 1: 52.218.212.42
r5-pc.s3.amazonaws.com canonical name = s3-us-west-2-w.amazonaws.com
uci show firewall
uci show dhcp
netstat -l -n -p | grep -e 127.0.0.1:53
root@OpenWrt:~# **netstat -l -n -p | grep -e 127.0.0.1:53**
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 31109/dnsmasq
udp 0 0 127.0.0.1:53 0.0.0.0:* 31109/dnsmasq
root@OpenWrt:~# **uci show firewall**
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].target='REJECT'
firewall.@rule[9].name='Block-Egress-SMB'
firewall.@rule[9].src='lan'
firewall.@rule[9].dest='wan'
firewall.@rule[9].dest_port='135 137-139 445'
firewall.@rule[10]=rule
firewall.@rule[10].name='Block-Egress-TFTP'
firewall.@rule[10].proto='udp'
firewall.@rule[10].dest_port='69'
firewall.@rule[10].target='REJECT'
firewall.@rule[10].src='lan'
firewall.@rule[10].dest='wan'
firewall.@rule[11]=rule
firewall.@rule[11].target='REJECT'
firewall.@rule[11].name='Block-Egress-Syslog'
firewall.@rule[11].dest_port='514'
firewall.@rule[11].src='lan'
firewall.@rule[11].proto='tcp udp'
firewall.@rule[11].dest='wan'
firewall.@rule[12]=rule
firewall.@rule[12].name='Block-Egress-SNMP'
firewall.@rule[12].proto='udp'
firewall.@rule[12].target='REJECT'
firewall.@rule[12].dest_port='161-162'
firewall.@rule[12].src='lan'
firewall.@rule[12].dest='wan'
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].syn_flood='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[0].log='1'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].log='1'
firewall.@zone[1].network='wan wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].forward='REJECT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.adblock_dns_53=redirect
firewall.adblock_dns_53.name='Adblock DNS, port 53'
firewall.adblock_dns_53.src='lan'
firewall.adblock_dns_53.proto='tcp udp'
firewall.adblock_dns_53.src_dport='53'
firewall.adblock_dns_53.dest_port='53'
firewall.adblock_dns_53.target='DNAT'
firewall.adblock_dns_853=redirect
firewall.adblock_dns_853.name='Adblock DNS, port 853'
firewall.adblock_dns_853.src='lan'
firewall.adblock_dns_853.proto='tcp udp'
firewall.adblock_dns_853.src_dport='853'
firewall.adblock_dns_853.dest_port='853'
firewall.adblock_dns_853.target='DNAT'
firewall.adblock_dns_5353=redirect
firewall.adblock_dns_5353.name='Adblock DNS, port 5353'
firewall.adblock_dns_5353.src='lan'
firewall.adblock_dns_5353.proto='tcp udp'
firewall.adblock_dns_5353.src_dport='5353'
firewall.adblock_dns_5353.dest_port='5353'
firewall.adblock_dns_5353.target='DNAT'
firewall.@rule[13]=rule
firewall.@rule[13].name='Block-Egress-SMTP'
firewall.@rule[13].proto='tcp'
firewall.@rule[13].dest_port='25'
firewall.@rule[13].target='REJECT'
firewall.@rule[13].src='lan'
firewall.@rule[13].dest='wan'
firewall.@rule[14]=rule
firewall.@rule[14].name='Block-Egress-IRC'
firewall.@rule[14].proto='tcp'
firewall.@rule[14].dest_port='6660-6669'
firewall.@rule[14].target='REJECT'
firewall.@rule[14].src='lan'
firewall.@rule[14].dest='wan'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='wan'
firewall.@forwarding[0].src='lan'
firewall.miniupnpd=include
firewall.miniupnpd.type='script'
firewall.miniupnpd.path='/usr/share/miniupnpd/firewall.include'
firewall.miniupnpd.family='any'
firewall.miniupnpd.reload='1'
root@OpenWrt:~# **uci show dhcp**
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@dnsmasq[0].nonwildcard='1'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].serversfile='/tmp/adb_list.overall'
dhcp.@dnsmasq[0].domain='BestLocalAreaNetwork'
dhcp.@dnsmasq[0].cachesize='1000'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'