Hi everybody,
Since a couple of days, i try to get the following working:
RPi (client) --> WAN --> GL-AR300M (OpenWRT and OpenVPN) --> Routing to my HomeNetwork.
What works:
I can establish the OpenVPN to my AR300M.
I can ping and SSH from client to AR300M (and also from AR300M to client).
root@GL-AR300M:~# ssh pi@192.168.2.6
pi@192.168.2.6's password:
Linux devopb 4.14.98-v7+ #1200 SMP Tue Feb 12 20:27:48 GMT 2019 armv7l
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Apr 10 17:04:22 2019 from 192.168.8.100
pi@devopb:~ $
pi@devopb:~ $ ssh root@192.168.2.1
root@192.168.2.1's password:
BusyBox v1.28.3 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 18.06.1, r7258-5eb055306f
-----------------------------------------------------
root@GL-AR300M:~#
But i can NOT get it to route traffic to my homenet. For example i can not reach 192.168.1.22 (which is also a RPi.
Somehow i made it, that i can also reach the AR300M trough 192.168.1.2 (which is its internal IP), but no other devices).
pi@devopb:~ $ ssh root@192.168.1.2
root@192.168.1.2's password:
BusyBox v1.28.3 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt 18.06.1, r7258-5eb055306f
-----------------------------------------------------
root@GL-AR300M:~#
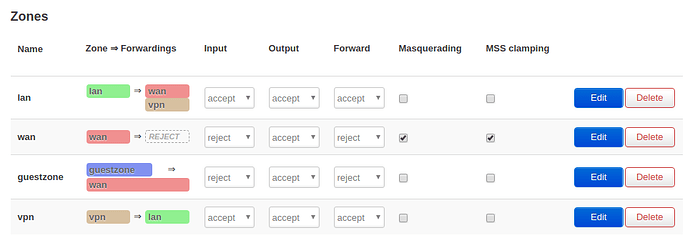
My configs so far:
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6f:af50:d654::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option macaddr 'e4:95:6e:44:80:f2'
option default_macaddr 'e4:95:6e:44:80:f2'
option hostname 'GL-AR300M-0f1'
option ipaddr '192.168.1.2'
option gateway '192.168.1.254'
option broadcast '192.168.1.255'
option dns '1.1.1.1'
option ifname 'eth1'
config device 'lan_dev'
option name 'eth1'
option macaddr 'e4:95:6e:44:80:f1'
config interface 'wan'
option hostname 'GL-AR300M-0f1'
option metric '10'
option clientid 'root'
option proto 'static'
option ipaddr '192.168.2.2'
option gateway '192.168.2.254'
option netmask '255.255.255.0'
option peerdns '0'
option dns '1.1.1.1 8.8.8.8'
option ifname 'eth0 eth1'
config interface 'wan6'
option proto 'dhcpv6'
option ifname 'eth0'
config interface 'guest'
option ifname 'guest'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
option ip6assign '60'
config route
config interface 'vpn0'
option proto 'none'
option ifname 'tun0'
option auto '1'
/etc/config/openvpn
option enabled 1
option port 1194
option proto tcp
option dev tun0
option ca /root/ca.crt
option cert /root/server.crt
option dh /root/dh4096.pem
option key /root/server.key
option server "192.168.2.0 255.255.255.0"
option ifconfig_pool_persist /tmp/ipp.txt
list push "route 192.168.1.0 255.255.255.0"
route 192.168.1.0 255.255.255.0
client-to-client
option keepalive "10 120"
option tls_auth "/root/tlsauth.key 0"
option cipher AES-256-CBC
option compress lzo
option persist_key 1
option persist_tun 1
option user nobody
option status /tmp/openvpn-status.log
option verb 3
/etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option device 'tun0'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config zone 'guestzone'
option name 'guestzone'
option network 'guest'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
config forwarding 'guestzone_fwd'
option src 'guestzone'
option dest 'wan'
config rule 'guestzone_dhcp'
option name 'guestzone_DHCP'
option src 'guestzone'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule 'guestzone_dns'
option name 'guestzone_DNS'
option src 'guestzone'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config include 'mwan3'
option type 'script'
option path '/var/etc/mwan3.include'
option reload '1'
config rule 'glservice_rule'
option name 'glservice'
option dest_port '83'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option enabled '0'
config rule 'vpn'
option name 'Allow-OpenVPN'
option src 'lan'
option dest_port '1194'
option proto 'tcp'
option target 'ACCEPT'
option dest 'lan'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'vpn'
option forward 'ACCEPT'
list device 'tun0'
option network 'vpn0'
config redirect
option target 'DNAT'
option src 'vpn'
option dest 'lan'
option proto 'tcp udp'
option src_dport '23'
option dest_ip '192.168.1.22'
option dest_port '22'
option name 'vpn_sshtest'
option reflection '0'
option enabled '0'
config forwarding
option dest 'wan'
option src 'lan'
config forwarding
option dest 'lan'
option src 'vpn'
config forwarding
option dest 'vpn'
option src 'lan'
Please help, i really have no clue. I already followed a lot of Wiki/Tut/HowTo's, so maybe there is also just a left-over, which is blocking me 
Thx alot,
Icinger