hi,
i am disapointed, not able to get acces from outside.
The modem does not permit bridge mode.
LiveBox orange is the modem (192.168.0.1) > dmz to OpenWRT (192.168.0.11) > Openwrt (192.168.1.1)
on the modem, i forward 80 & 443 to openwrt & firewall is disabled.
ddns is correct on OpeWrt.
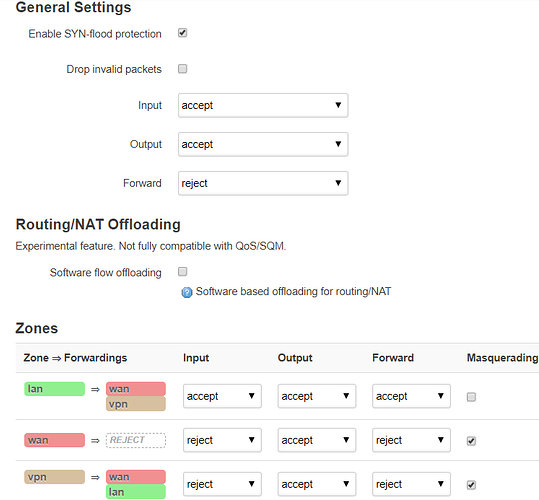
some firewall extract :
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'config include
option path '/etc/firewall.user'
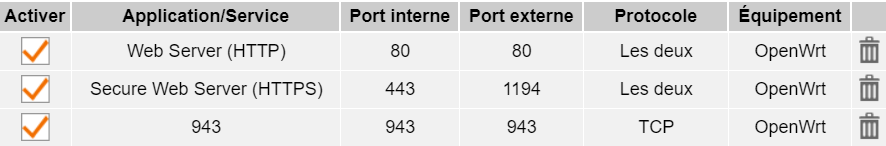
config rule
option src_port '80'
option src 'wan'
option name '80'
option target 'ACCEPT'
option dest_port '80'
option proto 'tcp udp'
option dest 'lan'
option enabled '0'
config rule
option src_port '443'
option src 'wan'
option name '443'
option target 'ACCEPT'
option dest_port '443'
option proto 'tcp udp'
option dest 'lan'
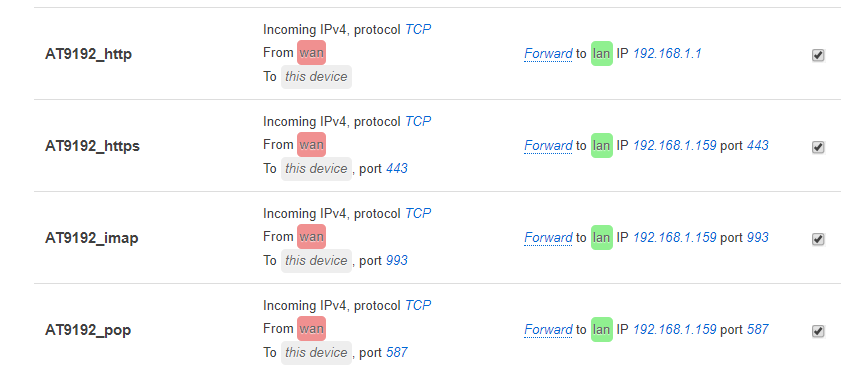
option enabled '0'config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'TCP'
option src_dport '443'
option dest_ip '192.168.1.159'
option dest_port '443'
option name 'AT9192_https'
Network definition
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'config globals 'globals'
option ula_prefix 'fd48:2080:194b::/48'config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '8.8.8.8'
list dns '8.8.4.4'config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'c0:4a:00:50:fd:6b'config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'config interface 'nordvpn_vpn'
option proto 'none'
option ifname 'tun0'
option metric '10'config interface 'vpn0'
option ifname 'tun0'
option proto 'none'
option auto '1'
Any idea ? Tks in advance.
Arnaud

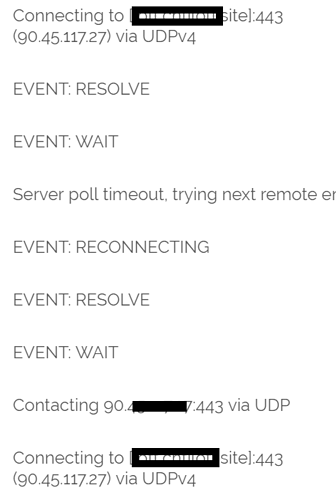
 it is in progress
it is in progress