You cannot directly use vlans on top of wifi but you could use something like multiple gre tap tunnels and bridge them to the corresponding ethernet vlan devices on each end.
As jow correctly points out, segregating traffic over a single, 802.11 link can't be done using VLANs as they aren't supported by 802.11.
If what you're trying to do is segregate traffic that is from multiple (Virtual) APs ("SSIDs") on an Ethernet link, that is a simpler task, assuming both routers can be properly configured. The general pattern is:
- Select a VLAN number for each "different" kind of traffic. I suggest not using VLANs 1 or 2 for "custom" configurations (some switches' drivers have an upper limit of, for example, 16 or 128 VLANs, making configuration of "VLAN 1000" a bit more complex1)
- Create a VLAN-tagged interface on the "right" physical interface of the AP (Edit: I often use the "WAN" port and Ethernet interface on devices that aren't serving as a border router.)
- Create a bridge over that interface
- Configure the switch so that the trunk port is tagged for that VLAN and that it is tagged for the CPU port as well
- Configure firewall rules (on all points where the VLANs come together) to prevent forwarding between VLANs, as well as "INPUT" to the device itself
- Configure
/etc/config/wirelessto associate the proper VAP (SSID) with the bridge created above
Personally, I never run untagged traffic on a VLAN trunk. Since it's a link under my control, I make it very clear what goes where by using a VLAN tag on everything (and denying untagged traffic with devices that allow me to configure them in that way)
1 Configuration of high-numbered VLANs can be done with the vid and pvid UCI parameters. See https://openwrt.org/docs/guide-user/base-system/basic-networking#switch_configuration for some details.
Awesome. Thanks again. But wondering what Q over Q in routeros documentation is. I guest some propietary extension, but maybe I can use it.
QinQ is primarily for huge-scale enterprises for whom 1023 VLANs aren't enough. It is sometimes needed for home users as, for example, the ISP may set it up so that the "outer" VLAN is used for "Joe's connection" and the "inner" VLAN separates Internet, phone, and video.
Do I understand it correctly, that I actually need to create two bridges one for LAN+WLAN and second just for GUEST WLAN on the AP? So that both bridges will contain their WLAN alias (not sure if it's correct term) and VLAN (eg. eth0.3 and eth0.4) port.
Also reading @jow answer. He is suggesting tap interfaces. How are those different from interface aliases in openwrt?
PS: I might be completely (once again) off with "alias" terminology.
Yes, that sounds correct. Each “network” gets:
- It’s own (single) DHCP server, subnet, and some way to get DNS and probably NTP
- It’s own VLAN-tagged, Ethernet interface
- It’s own bridge over that VLAN-tagged interface
- It’s wlan interface set to associate with that bridge
- It’s bridge in it’s own firewall zone
“tun” and GRE are tunnels. They are used to send one protocol inside another. Packets put into one end of the tunnel "magically" appear at the other end. VPNs are one place where these are used (internally). Put a packet into your "tun0" interface and it appears at your VPN server. It wasn't sent "bare" over the Internet, but wrapped inside of something "safe" that the other end understands.
An interface "alias" is often used to provide a multiple addresses on a single, physical interface. It typically doesn't "wrap" the packets with anything, just alerts the interface driver and hardware to be able to use more than one address.
Thanks @jeff. In mean time, I've also found quite nice howto I can follow. https://www.middling.uk/blog/2015/03/customising-openwrt-to-my-needs/
The last thing that worry me is the old TL-WR841N/ND v8. It will be used just as an dumb AP, but I still need to configure two VLANs on it. The only problem reading it's openwrt switch configuration page is
eth0 is directly connected to the WAN port.
Not sure how can this can impact me.
If it isn't connected to the switch, it means that as soon as you configure a VLAN tag on a sub-interface of eth0, it appears on the port.
Looking on switch config for ASUS WL-500g - https://openwrt.org/docs/guide-user/network/vlan/switch
makes think, that basically it just prevents data flow from WAN port to other ports, without passing through CPU. But apart from slower routing in some specific cases, it shouldn't limit me that much. Is my assumption correct? (Sorry for asking so many question, I promise this will be the last one for a long time ;).
EDIT: Or in other words WAN port is not part of the switch
On this model (and most with an Atheros internal 10/100 switching chip like the AR92xx and 93xx) the blue WAN port is a direct path into the CPU known as eth0. Simply declare VLANs such as eth0.1 eth0.2 in the physical settings of your network bridges.
In the intended use of a router connecting a LAN to the Internet, it is potentially faster since a single CPU port with VLANs in the switch would have to be shared between LAN and WAN purposes. In that use case, the CPU has to touch every WAN packet anyway for NAT translation.
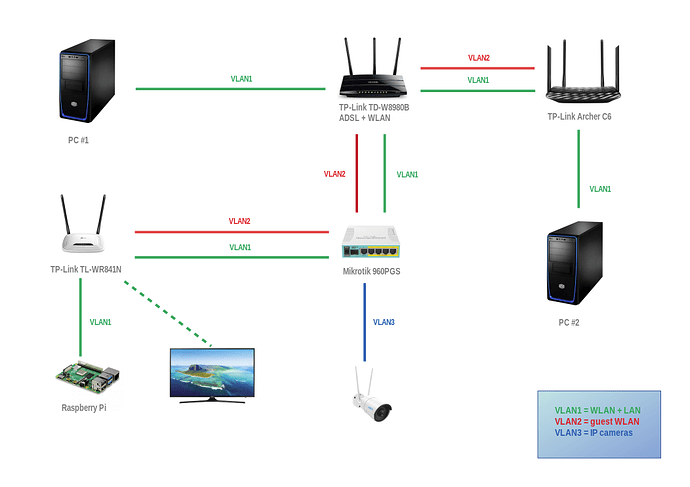
Finally I've managed to setup some test VLANs between TL-WR841N (now just dumb AP) and Mikrotik.
It's not final, because I'm waiting for USB to UART bridge, so I can flash OpenWrt on TD-W8980B.
Hopefully after that, I will managed to setup Mikrotik to "passthrough" VLAN2 and VLAN1 from TD-W8980B to TD-W8980B.
This is new topology.