I have a network comprised of multiple VLANs. Wireguard is set as default route and router can ping6 via the wireguard network. Clients on lan network bypass Wireguard and go to wan. I can do this IPv4 using PBR, and it works great.
In the past I had enabled NAT6 in order to share my Wireguard's /128 address via the ULA on the vpn network. To prevent leaks I also disabled ULA on lan (LAN clients only get GUA). At one point this all worked great, but since upgrading to snapshot (using firewall3/ipt), I can no longer route any (lan or vpn) IPv6 on clients.
uci export network:
package network
config globals 'globals'
option ula_prefix 'ddc2:9aea:13b1::/48'
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.1.1'
option ip6assign '64'
option ip6ifaceid '::1'
option ip6hint '1'
option device 'br-lan'
list ip6class 'wan6'
config interface 'wan'
option proto 'dhcp'
option device 'eth0'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix '56'
option device 'eth0'
option ip6table '2'
config interface 'wireguard'
option proto 'wireguard'
option private_key 'redacted
list addresses '10.65.5.239/32'
list addresses 'fc00:bbbb:redacted/128'
config wireguard_wireguard
option persistent_keepalive '25'
option public_key 'redacted'
option endpoint_host 'redacted'
option description 'vpn'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::0/0'
option endpoint_port '51820'
option route_allowed_ips '1'
config interface 'vpn'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
list dns 'redacted'
option device 'br-vpn'
option ip6ifaceid '::1'
option ip6assign '64'
option ip6hint '2'
list ip6class 'local'
config interface 'dmz'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option ip6assign '64'
option ip6ifaceid '::1'
option ip6hint '3'
option device 'br-dmz'
config interface 'iot'
option proto 'static'
option ipaddr '192.168.4.1'
option ip6assign '64'
option ip6hint '4'
option ip6ifaceid '::1'
option netmask '255.255.255.0'
option device 'br-iot'
config device
option name 'br-lan'
option type 'bridge'
option stp '1'
list ports 'eth1'
config device
option name 'br-vpn'
option type 'bridge'
list ports 'eth1.2'
config device
option name 'br-dmz'
option type 'bridge'
list ports 'eth1.3'
config device
option name 'br-iot'
option type 'bridge'
list ports 'eth1.4'
uci export firewall:
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
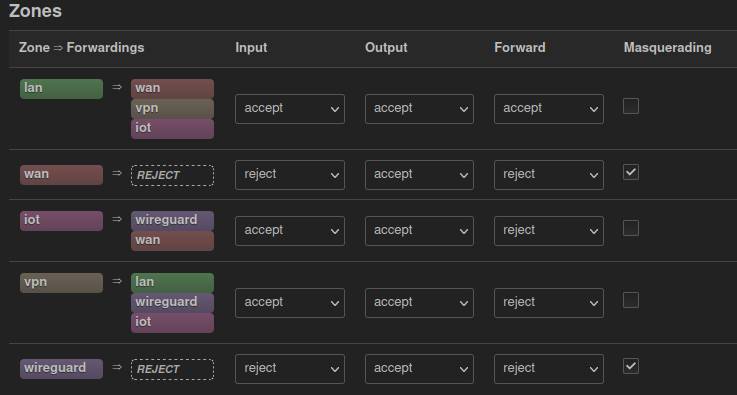
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'dmz'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config zone
option name 'iot'
option output 'ACCEPT'
list network 'iot'
option forward 'REJECT'
option input 'ACCEPT'
config zone
option name 'vpn'
option output 'ACCEPT'
list network 'vpn'
option forward 'REJECT'
option input 'ACCEPT'
config zone
option name 'wireguard'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wireguard'
option masq6 '1'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'lan'
option dest 'iot'
config forwarding
option src 'vpn'
option dest 'lan'
config forwarding
option src 'vpn'
option dest 'wireguard'
config forwarding
option src 'vpn'
option dest 'iot'
config forwarding
option src 'iot'
option dest 'wireguard'
config forwarding
option src 'iot'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled ''\''0'\'''
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config include 'pbr'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
option family 'any'
option reload '1'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
uci export pbr:
package pbr
config pbr 'config'
option src_ipset '0'
list supported_interface ''
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_chain_column '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option verbosity '1'
option webui_enable_column '1'
option webui_protocol_column '1'
option dest_ipset '0'
option webui_show_ignore_target '0'
option resolver_ipset 'dnsmasq.ipset'
option ipv6_enabled '1'
option strict_enforcement '1'
option enabled '1'
config policy
option interface 'wan'
option proto 'all'
option src_addr '192.168.1.0/24'
option name 'dmz4'
In this case the 192.168.1.0/24 subnet (lan) is routed to wan. Great! But I cannot seem to figure out how to use pbr to route lan IPv6 to wan6, every configuration of CIDR I've used for the GUAs on my lan segment fail with "unknown fw_mark." I've also read about using route6 to set up routes but I don't think it (or PBR?) are designed for routing based on GUAs (or their subnets).
Right now, I don't care about NAT6 or IPv6 in my vpn vlan. I just want to have IPv6 on my LAN working correctly (routed to wan6) as if the wireguard route were not involved. No matter what I try I cannot seem to accomplish this!
/etc/init.d/pbr status:
pbr 0.9.4-10 running on OpenWrt SNAPSHOT.
============================================================
Dnsmasq version 2.86 Copyright (c) 2000-2021 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus UBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth cryptohash DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default * 0.0.0.0 U 0 0 0 wireguard
IPv4 Table 201: default via 35.143.192.1 dev eth0
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-vpn proto kernel scope link src 192.168.2.1
192.168.3.0/24 dev br-dmz proto kernel scope link src 192.168.3.1
192.168.4.0/24 dev br-iot proto kernel scope link src 192.168.4.1
IPv4 Table 201 Rules:
30000: from all fwmark 0x10000/0xff0000 lookup wan
IPv4 Table 202: default via 10.65.5.239 dev wireguard
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-vpn proto kernel scope link src 192.168.2.1
192.168.3.0/24 dev br-dmz proto kernel scope link src 192.168.3.1
192.168.4.0/24 dev br-iot proto kernel scope link src 192.168.4.1
IPv4 Table 202 Rules:
29999: from all fwmark 0x20000/0xff0000 lookup wireguard
IPv6 Table 202: default dev wireguard proto static metric 1024 pref medium
============================================================
Mangle IP Table: PREROUTING
# Warning: iptables-legacy tables present, use iptables-legacy to see them
-N PBR_PREROUTING
-A PBR_PREROUTING -s 192.168.1.0/24 -m comment --comment dmz4 -c 0 0 -g PBR_MARK0x010000
============================================================
Mangle IPv6 Table: PREROUTING
-N PBR_PREROUTING
============================================================
Mangle IP Table MARK Chain: PBR_MARK0x010000
# Warning: iptables-legacy tables present, use iptables-legacy to see them
-N PBR_MARK0x010000
-A PBR_MARK0x010000 -c 2 134 -j MARK --set-xmark 0x10000/0xff0000
-A PBR_MARK0x010000 -c 2 134 -j RETURN
============================================================
Mangle IP Table MARK Chain: PBR_MARK0x020000
# Warning: iptables-legacy tables present, use iptables-legacy to see them
-N PBR_MARK0x020000
-A PBR_MARK0x020000 -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A PBR_MARK0x020000 -c 0 0 -j RETURN
============================================================
Current ipsets
============================================================
Your support details have been logged to '/var/pbr-support'. [✓]
Any ideas re: the best method to get IPv6 working on my lan network?