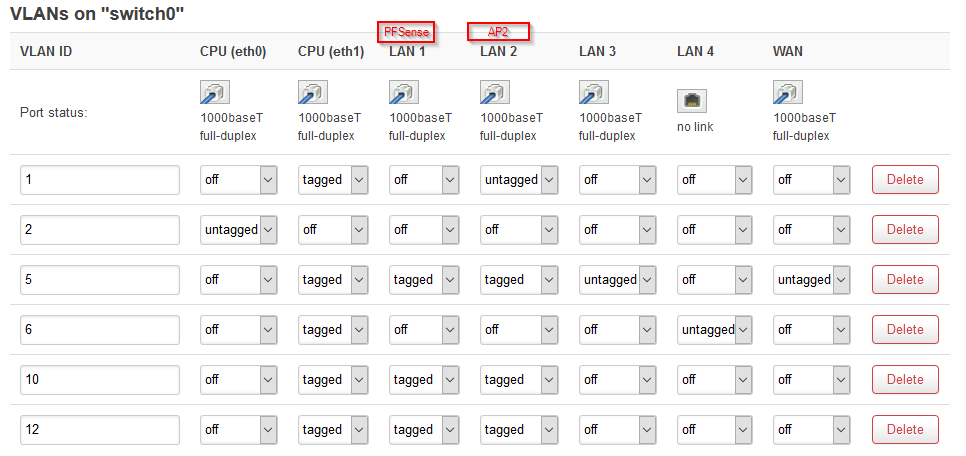
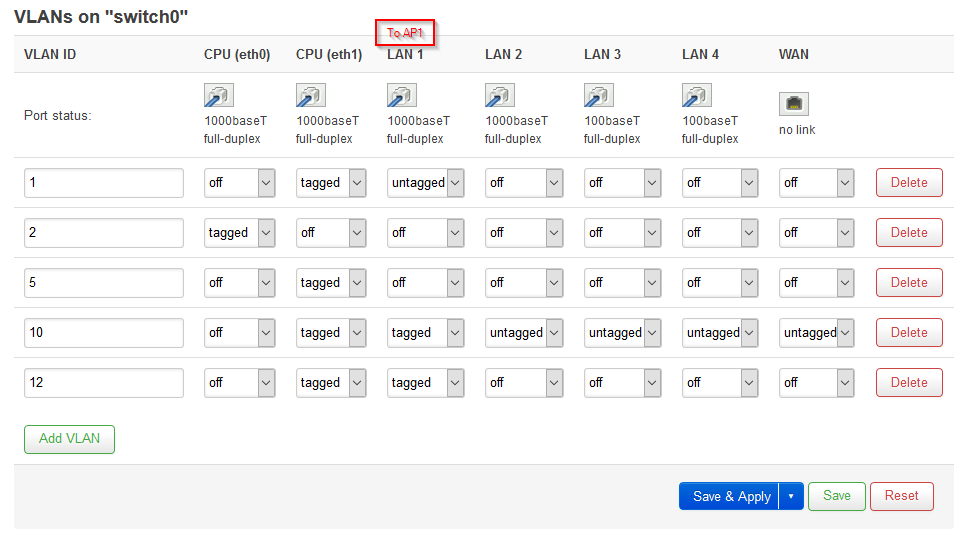
Hi
Im currently trying to configure 2 access points with OpenWRT with a PFSense to achieve the following:
VLANs:
Internal VLAN (5)
IOT VLAN (10)
Guest VLAN (12)
WLANs:
Internal WLan
IOT WLan
Guest WLan
DHCP an management should all run on PFSense. The connection should be from PFSense > AP1 > AP2. So AP 1 should forward the traffic from AP 2 to PFSense.
I managed to create the VLans on PFSense and to get the VLANs woking on the LAN ports of AP1. The internal WLan is also woking. Unfortunately everything else isn't working right now as I want it to ..
The Guest & IOT WLan don't get any IP from PFSense (over LAN its working properly). I have access to AP2 but only on the internal LAN.
Switch Configuration AP1:
Configuration:
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd9d:27ec:db1f::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option delegate '0'
option ipaddr '192.168.66.2'
option gateway '192.168.66.1'
option ifname 'eth1.1 eth1.5'
config interface 'wan'
option proto 'dhcp'
config interface 'wan6'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '10'
option ports '3t 4t 6t'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '12'
option ports '3t 4t 6t'
config interface 'IOT'
option proto 'none'
option type 'bridge'
option delegate '0'
option ifname 'eth0.10'
config interface 'Guest'
option ifname 'eth0.12'
option type 'bridge'
option delegate '0'
option proto 'none'
config interface 'Backup'
option proto 'static'
option ipaddr '192.168.33.1'
option netmask '255.255.255.0'
option ifname 'eth1.6'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '5'
option ports '2 3t 4t 5 6t'
config switch_vlan
option device 'switch0'
option vlan '6'
option ports '1 6t'
option vid '6'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
list interface 'GUEST'
config dhcp 'lan'
option interface 'lan'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'Backup'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'Backup'
config dhcp 'Guest'
option interface 'Guest'
option ignore '1'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'soc/1b500000.pci/pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option key '5c@3vV2DkRsLC~BYj:CUCiz=EEZS4pd~ZuxkDH6tG\0+s|n2iv'
option ssid 'Quokka'
option encryption 'psk-mixed'
option ft_over_ds '1'
option ft_psk_generate_local '1'
option ieee80211r '1'
config wifi-device 'radio1'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'soc/1b700000.pci/pci0001:00/0001:00:00.0/0001:01:00.0'
option htmode 'HT20'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ft_over_ds '1'
option ssid 'Koala'
option encryption 'psk-mixed'
option ft_psk_generate_local '1'
option key '5c@3vV2DkRsLC~BYj:CUCiz=EEZS4pd~ZuxkDH6tG\0+s|n2iv'
option ieee80211r '1'
config wifi-iface 'wifinet3'
option ssid 'Skynet'
option encryption 'psk-mixed'
option device 'radio1'
option ieee80211r '1'
option ft_over_ds '1'
option key 'rWaG27YwxpQzSV2E'
option mode 'ap'
option network 'IOT'
option ft_psk_generate_local '1'
config wifi-iface 'wifinet4'
option ssid 'Test'
option encryption 'psk-mixed'
option device 'radio1'
option mode 'ap'
option network 'Guest'
option key 'test1234'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan Guest'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option forward 'REJECT'
option name 'Guest'
option output 'ACCEPT'
I tried so many things the last few days but can't seem to get it working. Maybe I'm also trying something that isn't even possible like this. I'm thankful for any help 
Cheers
Symon