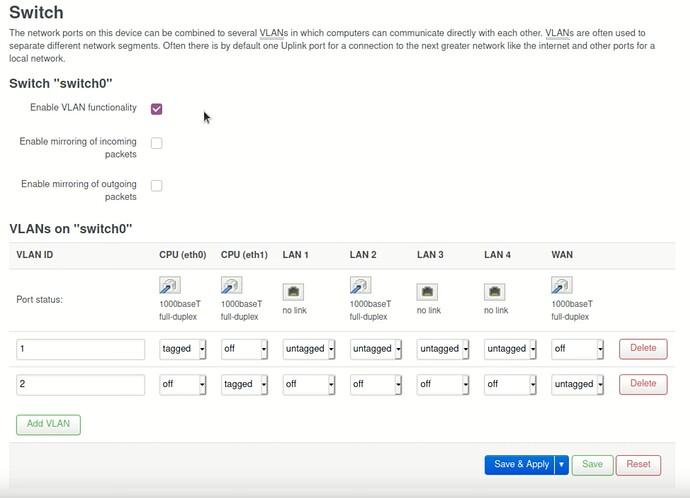
So tonight wasn't as successful as last night, to say the least.
Last night, entirely and only on the mesh HUB router, I added a Guest firewall zone, extra 'GUEST' interface (192.168.3.0/24) bound to 'bat0', and a couple of guest SSIDs (on the 2.4 & 5 GHz radios 0 & 2). Worked like a charm. I even had .3.0's DHCP telling clients to use my two pi-holes on the 'lan' .2.0 network for DNS, with a routing rule to allow .3.0 clients to access those two .2.0 DNS server IPs (only port 67 & 68). Perfect.
But replicating this config to the 2 mesh nodes was a complete failure.
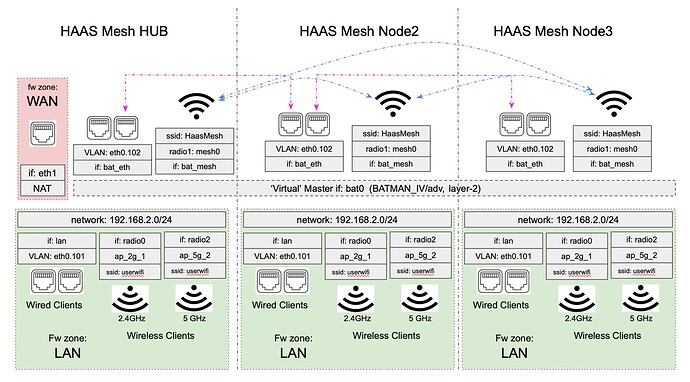
(Background: Although 192.168.2.1 is the Hub in your terminology, I still consider it a node too, so i refer to 192.168.2.2 as node-2, and 192.168.2.3 as 'node-3'. My node-2 is wireless mesh backhaul only (on radio1 which is dedicated to mesh), and node-3 upstairs is wired, though all 3 get at least some degree of connectivity via the wireless mesh; (this is presumably not used for comms between wired nodes?).
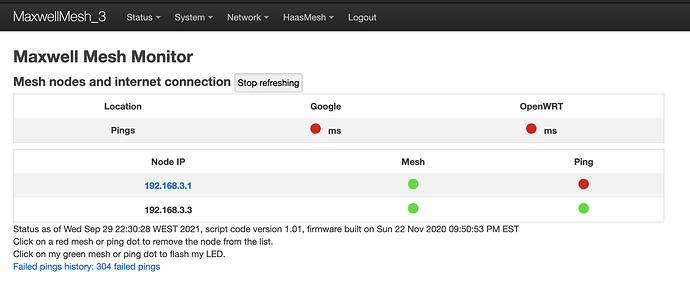
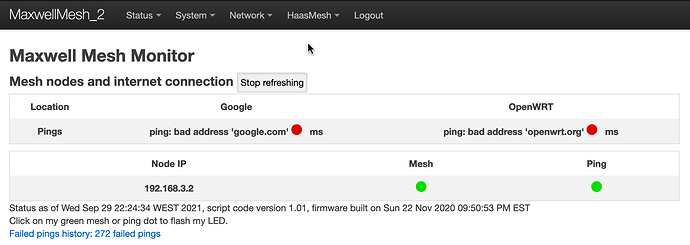
On both nodes 2 & 3, I can add the Guest firewall zone, create the .3.0 interface, create the Guest SSIDs bound to the new Guest .3.0/24 interface, but then when I add the 'bat0' binding to the Guest interface, the mesh seems to fail. Exactly how it fails I'm not really sure at all. But there's a hint in the HaasMesh Monitor page for node-3, which is now showing the IP address of the guest (192.168.3.0/24) for mesh connectivity, instead of .2.0/24:
To clarify, the wired node-3 Monitor page is showing .3.1 (hub) and .3.3 (itself), but node-2 (wireless) is not present.
I had to plug an ethernet cable into all 3 devices, with laptop set to static .2.x IP (DHCP wasn't working), and unbind the Guest 192.168.3.0/24 interface from 'bat0', then reboot, to get back to scratch.
I'm pretty much out of ideas at this stage. In a standard openwrt setup, VLANs would be added for the additional networks (guest .3.0/24, etc) and can be carried over a single ethernet to remote APs. But I've no idea if that is necessary, or would work, or break things even more, under BATMAN...