I have to allow first lanp "full" forwarding to wan, next blocking 80 and 443 SRC port in wan to lanp ?
No.
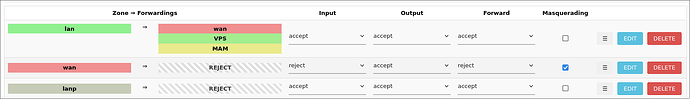
![]() Please be clear, order of firewall rules matter.
Please be clear, order of firewall rules matter.
- block 80 and 443 first
- then allow all
Wait...have you blocked lanp to wan or something?
We cant guess - you have to tell us.
i need block for all lanp network, not only my son host
Then block for all, simply omit son's IP or MAC. Then the rule will apply for all of lanp network. Simple.
Yes, I consider that this interface is limited from the start
Ok, but when we ask, you have to tell us or provide your configurations, so we can consider it too.
Hope the best for your rules.
Ummmmm....Ok, you already block 80 and 443 on lanp.
You reject everything.
- change to allow
Done.
That will allow everything except 80 and 443.
I would have liked a simple ruler like this:
config nat
option name 'Hors Proxy'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
option src 'wan'
option src_ip '192.168.5.0/24'
option dest_port '!80-443'
option target 'MASQUERADE'
it won't block proxy access too ?
sorry, i was wrong, it's only for the wan.
I'm confused where your syntax is coming from (it makes me wonder if there's more configs you haven't noted):
config rule
option name 'block_80and443'
list proto 'tcp'
option src 'lan'
option target 'REJECT'
option dest_port '80 443'
option dest '*'
- 8888 != 443
- 8888 != 80
- If your proxy is on the OpenWrt, it's input, not forward
 You're disabling the proxy for your son's gaming device so he can play - this is why you're making the rule
You're disabling the proxy for your son's gaming device so he can play - this is why you're making the rule
option src lanp ?
Sorry, I have to use my own device to make/verify syntax (i.e. no lanp):
config rule
option name 'block_80and443'
list proto 'tcp'
option src 'lanp'
option target 'REJECT'
option dest_port '80 443'
option dest '*'
I created this interface (lanp) to be dedicated to devices that must be forced to go through the proxy ![]()
I thank you very much for all the time you have devoted to me.
Yes, it took a while to understand you also firewalled that network too. ![]()
Also, you never explained how you "forced" devices to use the proxy, and why. So hope all the rules help to allow lanp to wan then block 80 and 443 for your son to bypass, and all other client devices are still forced to use the proxy locally on the lanp Input at port 8888 - as you say you configured them.
No worries, just let us know your success.
especially for devices like android and also to protect my children from malicious sites and especially to have the logs.
Cool, things like that can all be done on OpenWrt without the proxy.
Not sure about logging each HTTP/HTTPS request as easy as a proxy software, but cool!
(e.g. you can assign kids-safe DNS servers, force clients to use them, etc.)
Yea...I understand those are more difficult to add remote parental controls, etc. Gotcha!
So there was no other solution except full forwarding "wan" to "lanp" (and block 80,443) ?
Perhaps others have an idea:
- It seems the proxy is making a bad gaming experience
- Seems easy to bypass proxy for gaming
Well...
On the Debian, you could setup a network profile only for your son to game, and create another lan X - with all of this configured.
Leaving lanp's firewall configs, proxy, etc. intact.
![]() Or allow him on LAN to game, block his MAC from accessin 80 and 443
Or allow him on LAN to game, block his MAC from accessin 80 and 443
![]() Just to be clear, order matters in *nix -based systems, their ACLs, firewalls, etc. And when reducing it back into human communication - to avoid confusion:
Just to be clear, order matters in *nix -based systems, their ACLs, firewalls, etc. And when reducing it back into human communication - to avoid confusion:
So additionally/conversely - there should be no need to allow " 'wan' to 'lanp' "
We were discussing "allow lanp to wan, except for 80 and 443/tcp DST ports".
I don't know if that was just English parlance, but order matters when specifying firewall rules.