i have 2 OpenVPN instances on my OpenWrt router ( it is NOT the gateway, my gateway is an xDSL router with port forwarding setup correctly)
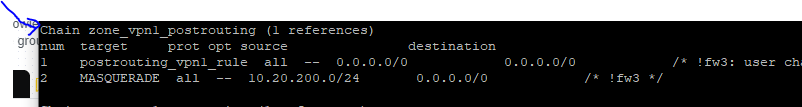
what i'm trying to achieve is enable masquerade on only ONE instance (i named it srvr2) while keeping it disabled on the other server. what happens is that if i try to enable it. it gets enabled on BOTH servers and almost everything.. ( wireshark sees the traffic coming from 192.168.1.222 which is the wan port static address on the openwrt ) while if i disable it i can see the direct tunnel ip address ( 10.20.100.0/24) and also 200.0/24 )
setup is as follows :
router================== OpenWrt ( vpn0 ....... and ... vpn1 )
================== 192.168.1.222 | 10.20.100.1 ........ 200.1
Firewall.conf:
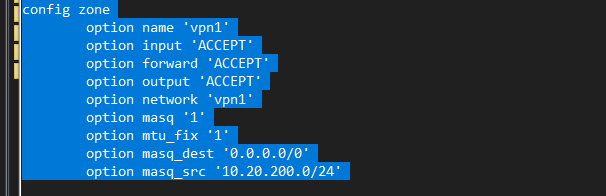
i want to enable masquerade on VPN1 only and not zero ( so that traffic comes out as 192.168.1.222 not the tunnel endpoint ip address ) . it never works
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'DROP'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '0'
option mtu_fix '1'
option network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option dest_port '1723'
option name 'pptp'
option target 'ACCEPT'
option proto 'all'
option src 'lan'
config rule
option target 'ACCEPT'
option name 'gre'
option src 'lan'
option proto 'gre'
option enabled '0'
###################################################################################
config rule
option name 'Allow-OpenVPN-Inbound'
option target 'ACCEPT'
option proto 'tcp'
option src '*'
option dest_port '443'
config rule
option name 'Allow-OpenVPN-UDP'
option target 'ACCEPT'
option proto 'udp'
option src '*'
option dest_port '444'
config zone
option name 'vpn0'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option masq '0'
option network 'vpn0 ipsec0'
option subnet '10.20.100.0/24'
option mtu_fix '1'
config forwarding
option dest 'vpn0'
option src 'lan'
config forwarding
option dest 'lan'
option src 'vpn0'
################################################################################################
config zone
option name 'vpn1'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option network 'vpn1'
option masq '1'
option mtu_fix '1'
config forwarding
option dest 'vpn1'
option src 'lan'
config forwarding
option dest 'lan'
option src 'vpn1'
config include 'ipsecd'
option type 'script'
option path '/etc/ipsec.include'
option reload '1'
config rule
option dest_port '500'
option src 'wan'
option name 'ike'
option target 'ACCEPT'
option proto 'udp'
config rule
option dest_port '4500'
option src 'wan'
option name 'ipsec'
option target 'ACCEPT'
option proto 'udp'
config rule
option target 'ACCEPT'
option src 'wan'
option name 'ah'
option proto 'ah'
config rule
option target 'ACCEPT'
option src 'wan'
option name 'esp'
option proto 'esp'
Network.conf
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc1:2325:d70e::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
option ipv6 '0'
config interface 'wan'
option ifname 'eth1'
option _orig_ifname 'eth1'
option _orig_bridge 'false'
option proto 'static'
option ipaddr '192.168.1.222'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
option broadcast '255.255.255.255'
option dns '8.8.8.8 208.67.222.222 8.8.4.4'
option ipv6 '0'
config interface 'wan6'
option ifname 'eth1'
option proto 'none'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config interface 'vpn0'
option ifname 'tun0'
option proto 'none'
option auto '1'
config interface 'vpn1'
option ifname 'tun1'
option proto 'none'
option auto '1'
config interface 'ipsec0'
option ifname 'ipsec0'
option _orig_ifname 'ipsec0'
option _orig_bridge 'false'
option proto 'none'