Well, I kind of like LLDP as long as you don't put any trust in it. It is also part of 802.3at, so it's nice to have on the power source port.
I've had and tested both. As a result, I returned the TL-SG108E to the dealer, because it looses its configuration on power down. On power up it had its factory settings.
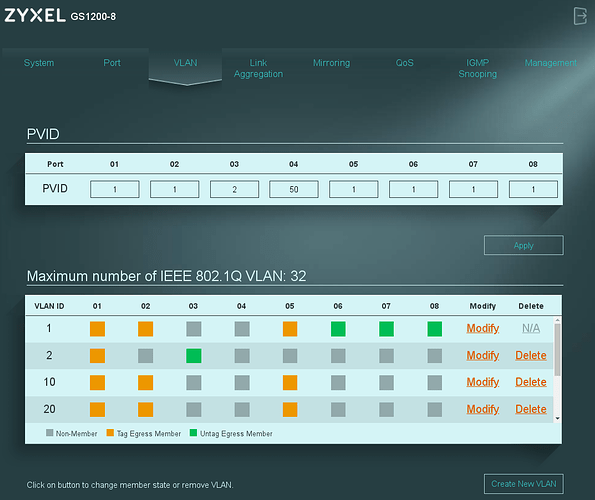
What I like with the Zyxel GS1200-8 (regarding the definition of VLANs) is, that the definitions for egress and ingress is on one page. So you can easily check, whether your PVID+port is in accordance to your VLAN definition (see the following screen shot).
To get a full overview of all features just download the user manual from zyxel support page.
Wow, that's quite the bug! Maybe you just had a bad unit, can't be on all of them, it would render them all useless.
Thanks for the screenshot on the Zyxell. Here's something that's not sitting well with me on these "cheap" switches, settings that don't make sense to me, but perhaps I'm not understanding VLANs and PVID well enough:
-
What does it mean to Tag Egress Port 01 in VLAN 1 but PVID for the port is 1? So you can ingress untagged traffic but egress only tagged or does it actually strip the tag on egress because PVID is set? In other words I don't understand which setting takes precedence Tagged or PVID.
-
Not sure whether this Zyxel allows it, but Netgear is just fine setting a port as Untagged in multiple VLANs which again I don't understand what it really means.
That's handy, on my "old" GS1920 it's on separate pages.
This is absolutely not the case with any version of the SG108E that I've had (I have 4 of them, two with POE version).
Of course, the first thing you do out of the box is upload the latest firmware. But that's true of any switch.
I think the SG108e of 5+ years ago was a much worse device. Recent firmware is functional, nothing to write home about, but basically free of any major bugs.
It means all VLAN1 packets will be tagged on egress, and any ingress of untagged packets will be interpreted as if they're on VLAN 1.
If you want a port to egress untagged packets you have to make it an untagged member.
Is there a scenario where this is useful in practice?
Hard to think of one. In general if you have tagged packets on a port, you want ALL the packets tagged. Most ports like this I'd say set the PVID to something invalid (ie. a VLAN that none of the ports are members of, like 4094 or something). Other more advanced switches you can just filter out all untagged packets, that's a better method.
It's useful if you have "dumb" clients (or hardware) that doesn't support VLAN tagging or to simply make it less of a pain configuring clients.
I understand PVID/native VLAN but it makes no sense to have the port untagged ingress, tagged egress on the same VLAN, dumb clients won't be able to deal with it.
I love my SG300 and SG350 switches. Ordinarily, we use Cisco enterprise switches everywhere, but I have one facility of about 100 people that use Cisco SG300s exclusively.
The SG300/350 line has a nice GUI, a CLI that is sort of like Cisco IOS, and very complete SNMP support. It has every layer 2 bell and whistle you could want. They will do layer 3 routing, but I've never used that feature, so I can't speak to how well it works.
As others have mentioned, the smartport macro capability can ruin your day in a hurry if you don't either correctly configure it for your environment, or completely disable it.
One other thing: If you buy a used 10 port SG300/SG350 off ebay, it will almost certainly come without the wall-wart (10 port models are the only ones that use wall warts). The non PoE versions use a standard 12V DC wall wart with a standard barrel type connector. The PoE versions, however, use a proprietary supply with a proprietary connector.
Cisco 2960S switches are dirt cheap on ebay. They are rock-solid and built like a battleship (as is most Cisco enterprise gear). But, they draw around 80W IIRC, and while they aren't jet engine loud, they aren't exactly quiet either. Some models have two 10Gb SFP+ slots, if you need 10Gb.
I have a SG108E v3 and a GS1200-8. Between those two (within the context of a $30 price point) the advantage is clearly to the Zyxel. The SG108 is from 2017 though and they have a V5 now. I don't know if it has corrected the limitations of the V3.
The big problem with the TP-Link is that the management interface listens on all the VLANs. Also its user interface is a lot less intuitive.
The Zyxel is pretty flexible as a very basic entry level "managed" switch. The one thing you can't change is that it must use VLAN 1 for management-- which would be a problem if you have to connect to an existing network where VLAN 1 is already used or can't be used. If you're designing the network from scratch it should be possible to work around this.
I don't understand the super confusing VLAN management on these consumer switches that span multiple pages and let you configure it in a way that makes no sense or has any practical purpose.
Here's a very simple and intuitive way to do it from an EdgeRouter X
If pvid is empty, use only tagged frames. You also can't have the same number in both pvid and vid. Done. A single page tells me everything I need to know, at a glance. How hard can it be?
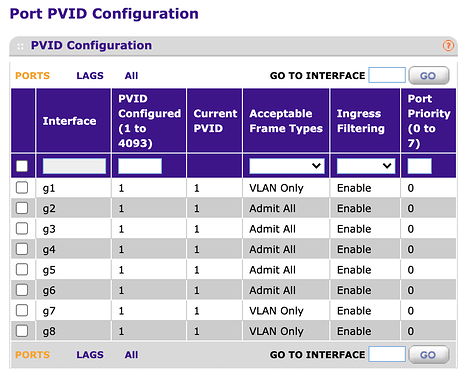
Compare with Netgear GS108Tv2:
You have to go to 2 more pages to create VLANs and assign ports to VLANs. You can end up with all sorts of crazy configs. There's no single place where you can get a nice view of the entire VLAN/port config.
I'm now the proud owner of a Cisco SG250-08, because you know, you just can't have enough switches around the house! It will be about a week before it arrives though.
The Cisco SG250-08 has so many (too many?) features! Feels a bit overwhelming for a home network where all I want is VLANs. The box is also slightly bigger and heavier than other switches. And it takes a good minute to boot and start passing traffic, I guess it does run a full OS on a slow CPU.
I think for a home network that just needs basic VLAN functionality something like the TP-Link TL-SG108 or Zyxel GS1200-8 are fine, with their well known limitations (VLAN 1 cannot be deleted/no management VLAN, HTTP only, no CLI, crappy Web interface, ...). I cannot endorse any of the new Netgear v3 switches because of the registration non-sense that Netgear forces on you.
Does any of these switches support TLS 1.3 ?
I got me a Netgear GS716Tv3, but it does only support TLS 1.0.
I've logged a support case with Netgear, still waiting for response.
Fortunately I can return the Netgear till end of january.
zyxel gs2210-48 is nice switch for core network
I wonder whether switches such as the Zyxel GS1900-16 are true 16 port switches or more like 2 x 8-port switches connected internally by a 1Gbps link.
Looking at this video it appears there are 2 chips inside.
That could be a problem as the bandwidth between the 2 "halves" is limited to 1Gbps.
i was searching for new switch for lab and came across on this one little fellow https://www.arubainstanton.com/files/DS_AIO_1930SwitchSeries.pdf , main advantage - no fan and four sfp+ and cherry on the top - low power consumption ( 24 port without poe) imho this is bes option for new future proof switch but i'm gonna play with it very soon 
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.