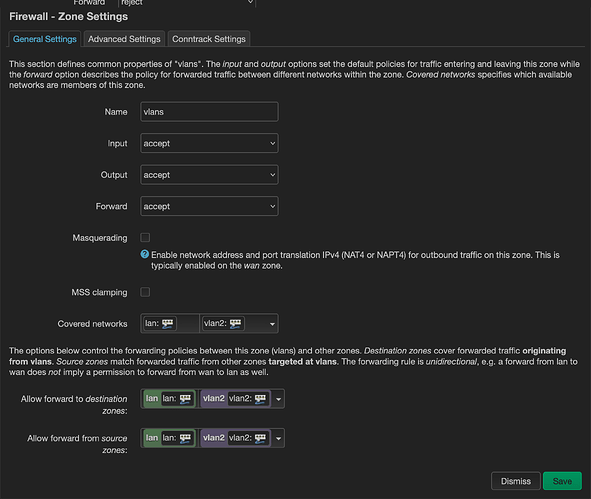
I tried doing this with the settings below and still no lucky. Is this the correct way to configure forwarding between devices in each vlan?
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
The firewall config appears to be wrong, but we need to see the full text config
Thank you copied below
Summary
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdee:e1a2:9fc4::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
list ports 'eth0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option delegate '0'
list dns_search 'lan'
list dns '192.168.1.100'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth0:t'
list ports 'lan1:u*'
list ports 'lan2:u*'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'eth0:t'
list ports 'lan3:u*'
list ports 'lan4:u*'
config interface 'vlan2'
option proto 'static'
option device 'br-lan.2'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option delegate '0'
config interface 'wgiot'
option proto 'wireguard'
option private_key 'xxx='
list addresses 'xxx/16'
option dns_metric '10'
list dns 'xxx'
list dns 'xxx'
config wireguard_wgiot
option description 'Imported peer configuration'
option public_key 'xxx='
list allowed_ips '0.0.0.0/0'
option endpoint_host 'xxx'
option endpoint_port '51820'
option persistent_keepalive '25'
config rule
option in 'vlan2'
option lookup '1742'
config route
option interface 'wgiot'
option target '0.0.0.0'
option netmask '0.0.0.0'
option table '1742'
config interface 'xxx'
option proto 'wireguard'
option private_key 'xxx='
option defaultroute '0'
list dns '192.168.1.100'
list addresses 'xxx'
config wireguard_wgmvad
option description 'xxx'
option public_key 'xxx='
list allowed_ips '0.0.0.0/0'
list allowed_ips '::0/0'
option endpoint_host 'xxx'
option endpoint_port '51820'
config rule
option in 'lan'
option lookup '1743'
config route
option interface 'wgmvad'
option target '0.0.0.0/0'
option netmark '0.0.0.0'
option table '1743'
config device
option name 'br-lan.1'
option type '8021q'
option ifname 'br-lan'
option vid '1'
option ipv6 '0'
config device
option name 'br-lan.2'
option type '8021q'
option ifname 'br-lan'
option vid '2'
option ipv6 '0'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '1'
option band '2g'
option htmode 'HE20'
option disabled '0'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'vlan2'
option mode 'ap'
option ssid 'xxx2'
option encryption 'sae-mixed'
option key 'xxx'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0+1'
option channel '36'
option band '5g'
option htmode 'HE80'
option disabled '0'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'xxx'
option encryption 'sae-mixed'
option key 'xxx'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.1.100'
config dhcp 'lan'
option interface 'lan'
option start '11'
option limit '150'
option leasetime '2m'
option dhcpv4 'server'
option master '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vlan2'
option interface 'vlan2'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wgiot'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wgiot'
option masq '1'
config forwarding
option src 'wgiot'
option dest 'wan'
config zone
option name 'vlan2'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vlan2'
config forwarding
option src 'vlan2'
option dest 'wgiot'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'wgmvad'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wgmvad'
config forwarding
option src 'lan'
option dest 'wan'
config zone
option name 'vlans'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan2'
config forwarding
option src 'vlans'
option dest 'lan'
config forwarding
option src 'vlans'
option dest 'vlan2'
config forwarding
option src 'lan'
option dest 'vlans'
config forwarding
option src 'vlan2'
option dest 'vlans'
delete all of this:
then add the vlan2 network to the lan firewall zone so that it looks like this:
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan2'
Restart and see if that fixes the problem.
If not, there are a few other things we'll explore.
Thanks @psherman for your continued help here.
No luck after trying this.
Updated file pasted below.
I also wonder if having both lan and vlan2 networks in a single zone will mean that I can't have a VPN connection on all devices accessing the internet from VLAN 2 as that is currently governed by a different firewall rule.
At this point I must also consider if VLANs are worth doing all of this or if my needs will be satisfied by firewall rules alone?
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan2'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vlan2'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vlan2'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config zone
option name 'wgmvad'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wgmvad'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'vlan2'
option dest 'wgmvad'
config rule
option name 'all vlan1 to 2'
list proto 'all'
option src 'lan'
option dest 'vlan2'
option target 'ACCEPT'
config rule
option name 'all vlan2 to vlan1'
list proto 'all'
option src 'vlan2'
option dest 'lan'
option target 'ACCEPT'
config forwarding
option src 'vlan2'
option dest 'lan'
You'll need policy based routing, so the firewall zone issue isn't really a big deal. You can use a single fireawll zone for both lan and vlan2, or you can put them into individual zones. Let's start with them in the same zone to reduce the complications, and then we can move them to a separate zone if you want later.
You've assigned the vlan2 network to two firewall zones. It must only be included in one zone. Therefore (for now anyway), delete the vlan2 firewall zone:
And remove all of the associated rules that involve that zone:
Restart and then try again.
If it is still not working, please detail how you are trying testing, and also what OS is on each of the hosts that you are using on each network.
Ok so an update here is that pinging my DNS (pihole) server results in a different message:
Request timeout for icmp_seq 8
92 bytes from openwrt.lan (192.168.2.1): Destination Port Unreachable
Vr HL TOS Len ID Flg off TTL Pro cks Src Dst
4 5 00 5400 657a 0 0000 3f 01 90db 192.168.2.159 192.168.1.100
I still can't access the admin page at 192.168.1.100/admin but the response to a ping suggests it's getting one step further.
I've also lost internet access on VLAN2 but I think that's due to the VPN configuration left over.
If you ping the pihole from the router itself does it work?
What host OS is the PiHole running on (direct on linux, docker on linux, docker on another platform)?
That could be... check your PBR and VPN configs. In fact, that could explain the issue for why you are unable to ping across the VLANs.
Yes pings from my computer on the main VLAN and from the router to the pihole get a response.
The pihole is running on a debian host directly.
I deleted the PBR add on a while ago. I removed the last traces of PBR from my firewall earlier (the lines below) while debugging. Do I need to reinstall PBR?
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
Does this mean it is working now?
Later... after we get everything else working.
Unfortunately not.
As before, my VLAN1 devices can communicate with the pihole (also on VLAN1 - via ethernet plugged into the router).
It is my VLAN2 devices that are unable to load the pihole admin page over http or use it as a dns server.
check the pihole settings -- specifically, settings > DNS > interface settings
I have it set to permit all origins while testing to rule this out. ![]()
Does the Linux host have a local firewall enabled that would prevent access from another subnet? (Context: this is the default situation on the windows firewall; typically not engaged on a Linux system, but possible depending on the local host firewall config)
I can't believe I forgot I had ufw enabled! But I've disabled it and rebooted the pihole and still no luck ![]()
do you have any other hosts you can put on that network (ideally linux) that you can try?
Yes I have a spare thin client that I have connected to the VLAN2-associated SSID.
I've been trying from both my main machine and the spare thin client with the same results.
Happy to try more steps from the thin client (which is also running debian but with a desktop environment)
I have copied my current configs below to make sure they're correct while I've been tinkering:
firewall
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan2'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Pihole Port Forward'
option family 'ipv4'
option src 'lan'
option src_ip '!192.168.1.100'
option src_dport '53'
option dest_ip '192.168.1.100'
option dest_port '53'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.1.100'
config dhcp 'lan'
option interface 'lan'
option start '11'
option limit '150'
option leasetime '2m'
option dhcpv4 'server'
option master '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'vlan2'
option interface 'vlan2'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdee:e1a2:9fc4::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
option ipv6 '0'
list ports 'eth0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option delegate '0'
list dns_search 'lan'
list dns '192.168.1.100'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth0:t'
list ports 'lan1:u*'
list ports 'lan2:u*'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'eth0:t'
list ports 'lan3:u*'
list ports 'lan4:u*'
config interface 'vlan2'
option proto 'static'
option device 'br-lan.2'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option delegate '0'
list dns '192.168.1.100'
list dns_search 'lan'
config rule
option in 'vlan2'
option lookup '1743'
config interface 'xxx'
option proto 'wireguard'
option private_key 'xxx='
option defaultroute '0'
list addresses 'xxx/32'
list dns 'xxx'
config xxx
option description 'xxx.conf'
option public_key 'xxx='
list allowed_ips '0.0.0.0/0'
list allowed_ips '::0/0'
option endpoint_host 'xxx'
option endpoint_port '51820'
option private_key 'xxx8='
config rule
option in 'lan'
option lookup '1743'
option disabled '1'
config route
option interface 'wgmvad'
option target '0.0.0.0/0'
option netmark '0.0.0.0'
option table '1743'
config device
option name 'br-lan.1'
option type '8021q'
option ifname 'br-lan'
option vid '1'
option ipv6 '0'
option acceptlocal '1'
config device
option name 'br-lan.2'
option type '8021q'
option ifname 'br-lan'
option vid '2'
option ipv6 '0'
config device
option name 'lan1'
option acceptlocal '1'
This should be working... I don't see a reason why it wouldn't at the moment.
I see you've just posted your DHCP and fireawll files... Let's review the latest network config files again, too..
[quote="withrespecto, post:37, topic:172645"]
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Pihole Port Forward'
option family 'ipv4'
option src 'lan'
option src_ip '!192.168.1.100'
option src_dport '53'
option dest_ip '192.168.1.100'
option dest_port '53'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
Try removing this rule (for now)... you don't want icmp in there, for sure.
Thanks I've removed that rule and shared the network config too.