[EDIT] With apologies for the length of this - I was obviously not good at being both precise and brief.
Sorry, my mistake. You are correct. What I should have said is that what should be in the [Interface] Address = field in the remote's generated config is instead being put in the remote's [peer] -> AllowedIP =. That is backwards and can never work.
Ok, I'll explain. To try and avoid the confusing over-use of 'peer' below, I'm going to use "remote" to mean a device remoting in to my OpwnWrt router, and "router" to mean the device acting as the VPN server.
My network topology: Standard cable-modem -> OpenWrt router. On the router the LAN is 192.168.2.1/24 and the wireguard interface is set up on 10.6.0.1/24.
Here are the relevant parts of /etc/config/network:
config interface 'lan'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config interface 'vpn'
option proto 'wireguard'
option private_key 'krouterprivatekey='
option listen_port '12345'
list addresses '10.6.0.1/24'
config wireguard_vpn
option description 'CursorToo3'
option public_key 'kremotepublickey='
option private_key 'kremoteprivatekey='
option preshared_key 'Kremotepresharedkey='
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '10.6.0.3/32'
Here is one of my actual, working (but obviously redacted) remote device's wireguard configs:
[interface[
Address = 10.6.0.3/32
DNS = 192.168.2.1
PrivateKey = kremoteprivatekey=
[Peer]
AllowedIPs = 10.6.0.0/24, 192.168.2.0/24
Endpoint = myddnsaddress.dynamodns.info:12345
PersistentKeepalive = 25
PreSharedKey = Kremotepresharedkey=
PublicKey = krouterpuiblickey=
This tells the remote it's own IP address is 10.6.0.3, and tells the remote that it's allowed to send anything to addresses 192.168.2.0/24 and 10.6.0.0/24 to its peer (the remote's peer is obviouisly the router).
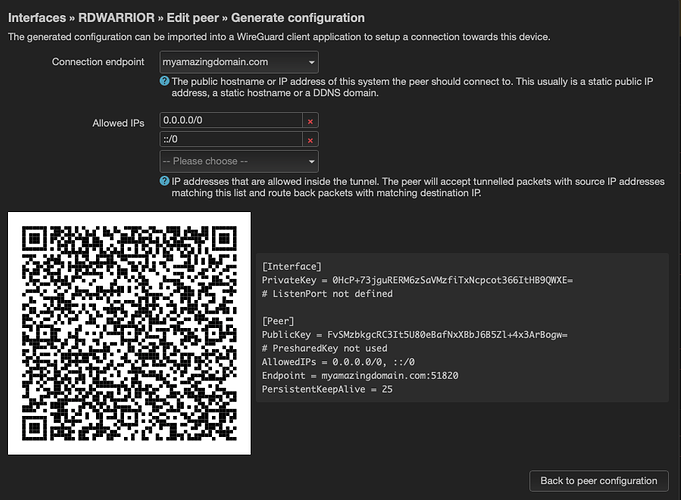
Here is the remote's config that OpenWrt actually generates:
[Interface]
PrivateKey = Kremotepresharedkey=
# ListenPort not defined
[Peer]
PublicKey = krouterprivatekey=
PresharedKey = Kremotepresharedkey=
AllowedIPs = 10.6.0.3/32
Endpoint = myddnsaddress.dynamodns.info:12345
PersistentKeepAlive = 25
Allowed IP for the peer configuration on the router should not be the allowed IP for the peer configuration on the remote. That is telling both the router and the remote to send to the same address. This makes no sense and can never work.
What it should be:
/etc/config/network
config wireguard_vpn
option description 'CursorToo3'
list allowed_ips '10.6.0.3/32' --->
Generated config:
[Interface]
Address = <--- router's PEER allowed_ips goes here
but never
Generated config:
[Peer]
AllowedIPs = <--- never never never there
And even better would be to make:
/etc/config/network
config interface 'vpn'
list addresses '10.6.0.1/24' ---->
This is what should be going
Generated config:
[Peer]
AllowedIPs = <---- router's VPN interface address should go here
I know I describe it with road-warrior topology, but if done as I describe, it will work with any topology because the it's router's VPN interface address and the router's VPN peer addresses/allowed_ips that change, not the position of where they go in the generated file.