maybe you post your network/firewall config?
He have many rules to post . There's a way to reset to default only the traffic rules or i must to reset the router?
I managed to block access by creating a drop rule between the ip of the first lan-side router and the device (router openwrt) on ports 443 and 80. It's a patch but it doesn't explain the underlying problem.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
uci export network; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
As I wrote before there is too much stuff and the risk that some data will pass is high. Is there a way to reset the firewall section to default?
If this router has a single ethernet port, then it will be used as lan. lan firewall zone accepts everything by default.
Since you are not posting configurations nor the router model, one can only speculate.
At least post the firewall settings
uci export firewall
There shouldn't be any sensetive info there.
I did and the problem seems to be solved. Maybe a mistake in the zone rules. I have to be more careful. Thanks @ThomasCr @krazeh .
@Hegabo already defaulted sorry. I wanted to sort it out quickly.
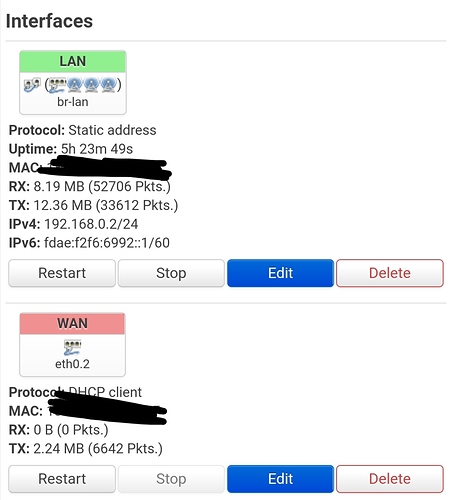
@trendy the router is Archer C7 V5 . He have 4 lan port and 1 wan/lan port . For the last i'm not sure.
If the "too much stuff" includes configuration you made, then there is a big chance you accidentally exposed it. And if it's just the default info, then you can post your network uci export network; just remember to redact your MAC addresses and your WiFi info. I don't imagine you have a public IP on that router, so you don't have to worry about that bit.
It's a WAN port (which is protected by the firewall in the default config).
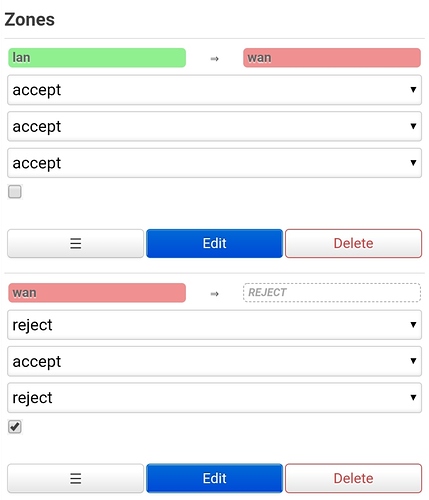
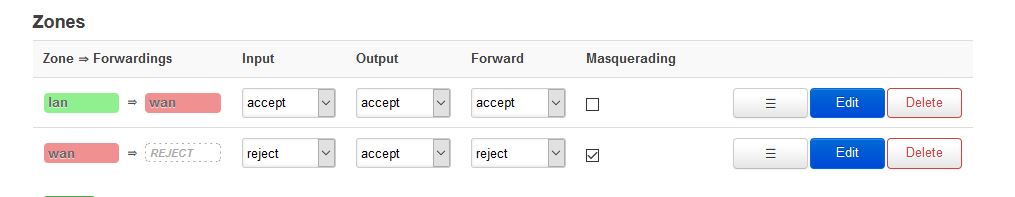
My best guess is that you accidentally assigned the LAN firewall zone to the WAN interface.
If you reset the firewall settings, and also the problem displayed, then it's unlikely to be so present.
Anyway, in the the default config the LAN zone is green and the WAN zone is red. If you go to the network page and see the WAN interface Red then that's likely to be correct.
You should have something like this
@Hegabo the same like you . The only difference in wan i have br-wan and you eth0.2. I think is not relevant.
It shouldn't make a difference in this particular case (as you appear to have only one interface in your WAN bridge - - most probably eth0.2), but why do you have a bridge for your WAN interface?
On what port can you connect to your router?
Maybe try temporary stop Dropbear and try if you can still access your router.
May be a setting error. But i don't know so solve. I have another problem. I am trying to configure the router so that it does not receive pings from wan addresses but although I have tried several ways to avoid it, I am continuing to receive it from the external ip of the mobile phone and I do not understand why.
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option src 'wan'
option target 'DROP'
list src_ip '10.10.10.10'
list src_ip '10.10.10.100'
option dest_port '20-23 443 80 3389'
option name '20 21 22 23 443 80 3389 Wan'
option family 'ipv4'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option proto 'icmp'
option target 'DROP'
option name 'NO Allow-Ping'
list src_ip '10.10.10.10'
list src_ip '10.10.10.100'
option src 'wan'
option family 'ipv4'
list icmp_type 'echo-request'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
These are not so many rules. Better post the whole troubleshooting commands to get a better picture.
Remember to redact passwords, MAC addresses and any public IP addresses you may have
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
{
"kernel": "4.14.180",
"hostname": "******",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C7 v5",
"board_name": "tplink,archer-c7-v5",
"release": {
"distribution": "OpenWrt",
"version": "19.07.3",
"revision": "r11063-85e04e9f46",
"target": "ath79/generic",
"description": "OpenWrt 19.07.3 r11063-85e04e9f46"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '****:****:****::/**'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option gateway '10.10.10.10'
option netmask '255.255.255.0'
option ifname 'eth0.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'static'
option broadcast '10.10.10.255'
option ipaddr '10.10.10.100'
option gateway '10.10.10.10'
option type 'bridge'
option netmask '255.255.255.0'
list dns ' ***'
list dns '***'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '***'
config switch
option name 'switch0'
option reset '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option country 'IT'
option htmode 'HT40'
option channel '48'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option legacy_rates '0'
option country 'IT'
option htmode 'HT40'
option channel 'auto'
config wifi-iface 'wifinet1'
option device 'radio1'
option key '***'
option network 'lan'
option mode 'ap'
option ssid '***'
option encryption 'psk2'
config wifi-iface 'wifinet2'
option ssid '***'
option device 'radio0'
option mode 'ap'
option network 'lan'
option key '***'
option encryption 'psk2'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option noresolv '1'
list addnhosts '/tmp/adb_list.overall'
option confdir '/tmp/dnsmasq.d'
option resolvfile '/etc/resolv-crypt.conf'
option allservers '0'
list server '127.0.0.1#5443'
list server '/pool.ntp.org/8.8.8.8'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '3h'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config domain
option name '***'
option ip '10.10.10.10'
config domain
option name '***'
option ip '192.168.1.1'
config domain
option ip '192.168.1.2'
option name '***'
config domain
option name '***'
option ip '192.168.1.4'
config domain
option name '***'
option ip '192.168.1.117'
config domain
option name '***'
option ip '192.168.1.162'
config domain
option name '***'
option ip '192.168.1.200'
config host
option mac '***'
option dns '1'
option name '***'
option ip '192.168.1.117'
option leasetime '24h'
config host
option mac '***'
option leasetime '12h'
option dns '1'
option name '***'
option ip '192.168.1.193'
config domain
option name '***'
option ip '192.168.1.210'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option src 'wan'
option target 'DROP'
list src_ip '10.10.10.10'
list src_ip '10.10.10.100'
option dest_port '20-23 443 80 3389'
option name '20 21 22 23 443 80 3389 Wan'
option family 'ipv4'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option proto 'icmp'
option target 'DROP'
option name 'NO Allow-Ping'
list src_ip '10.10.10.10'
list src_ip '10.10.10.100'
option src 'wan'
option family 'ipv4'
list icmp_type 'echo-request'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Generated by iptables-save v1.8.3 on Sat Oct 10 23:24:24 2020
*nat
:PREROUTING ACCEPT [3444:417574]
:INPUT ACCEPT [790:54156]
:OUTPUT ACCEPT [501:35747]
:POSTROUTING ACCEPT [404:27977]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[3444:417574] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[3073:372125] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[371:45449] -A PREROUTING -i br-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[1504:166447] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[3:988] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[1100:138470] -A POSTROUTING -o br-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[3:988] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[3073:372125] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[1100:138470] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[1100:138470] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[371:45449] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sat Oct 10 23:24:24 2020
# Generated by iptables-save v1.8.3 on Sat Oct 10 23:24:24 2020
*mangle
:PREROUTING ACCEPT [54535:44716828]
:INPUT ACCEPT [4090:438848]
:FORWARD ACCEPT [50031:44143639]
:OUTPUT ACCEPT [3033:511625]
:POSTROUTING ACCEPT [52948:44650885]
[389:21472] -A FORWARD -o br-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Oct 10 23:24:24 2020
# Generated by iptables-save v1.8.3 on Sat Oct 10 23:24:24 2020
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[809:75619] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[3283:363309] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[969:188461] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1084:64220] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[950:70744] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[450:49264] -A INPUT -i br-wan -m comment --comment "!fw3" -j zone_wan_input
[50031:44143639] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[48909:43995953] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1122:147686] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i br-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[809:75619] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[2228:436902] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[2046:423549] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[7:2317] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[175:11036] -A OUTPUT -o br-wan -m comment --comment "!fw3" -j zone_wan_output
[119:6276] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[297:41380] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[170:9380] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[914:54840] -A syn_flood -m comment --comment "!fw3" -j DROP
[7:2317] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[1122:147686] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[1122:147686] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[950:70744] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[950:70744] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[7:2317] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[7:2317] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[950:70744] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[119:5384] -A zone_wan_dest_ACCEPT -o br-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[1178:153338] -A zone_wan_dest_ACCEPT -o br-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o br-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[450:49264] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[5:260] -A zone_wan_input -s 10.10.10.10/32 -p tcp -m tcp --dport 20:23 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[21:1092] -A zone_wan_input -s 10.10.10.10/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p tcp -m tcp --dport 3389 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p tcp -m tcp --dport 20:23 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p tcp -m tcp --dport 3389 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p udp -m udp --dport 20:23 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p udp -m udp --dport 443 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p udp -m udp --dport 3389 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p udp -m udp --dport 20:23 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p udp -m udp --dport 443 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p udp -m udp --dport 3389 -m comment --comment "!fw3: 20 21 22 23 443 80 3389 Wan" -j DROP
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -s 10.10.10.10/32 -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: NO Allow-Ping" -j DROP
[0:0] -A zone_wan_input -s 10.10.10.100/32 -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: NO Allow-Ping" -j DROP
[8:256] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[416:47656] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[175:11036] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[175:11036] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[416:47656] -A zone_wan_src_REJECT -i br-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Oct 10 23:24:24 2020
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
8: br-wan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 10.10.10.100/24 brd 10.10.10.255 scope global br-wan
valid_lft forever preferred_lft forever
default via 10.10.10.10 dev br-wan
10.10.10.0/24 dev br-wan scope link src 10.10.10.100
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
broadcast 10.10.10.0 dev br-wan table local scope link src 10.10.10.100
local 10.10.10.100 dev br-wan table local scope host src 10.10.10.100
broadcast 10.10.10.255 dev br-wan table local scope link src 10.10.10.100
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default