hello all
its posible install on tp-link TD-W8970, via web upgrated?
or necesary over serial cable? where can buy this cable without having to weld?
thanks team
hello all
its posible install on tp-link TD-W8970, via web upgrated?
or necesary over serial cable? where can buy this cable without having to weld?
thanks team
See the LEDE page for the TD-W8970...
https://lede-project.org/toh/hwdata/tp-link/tp-link_td-w8970_10
You might consider using TFTP rather than the web GUI.
TFTP tutorials…
thanks, it only posible by serial cable?
TFTP doesn't require a serial cable.
ok but, im conect to telnet is not posible execute coman, only a basic internal command.
You might want to open a new topic for your question regarding installation of LEDE on TD-W8970.
I created a login here with a single purpose - to say thank you guys  You rock!
You rock! 
So, I took the question to the hostap mailing list and there were two issues mentioned the workaround doesn't cover so far, TDLS and WNM Sleep Mode handshakes [1] [2]. Jouni Malinen made suggestions how these two attack scenarios could be further complicated, so I posted patches on the lede-dev mailing list, to incorporate those suggestions into LEDE [3].
Btw, it turned out that I confused two CVEs before, so the aforementioned CVE-2017-13086 isn't about the PeerKey handshake but really about TDLS.
[1] http://lists.infradead.org/pipermail/hostap/2017-October/038005.html
[2] http://lists.infradead.org/pipermail/hostap/2017-October/038007.html
[3] http://lists.infradead.org/pipermail/lede-dev/2017-October/009521.html
Tried in a Linksys E2000, and WAN port not detecting connection.
Same here. Took some minutes to update my router from 14.07rc and 15.05 to 17.01.4. Worked like a charm with keep settings enabled
I can confirm that this new version works without any issue as upgrade from Chaos Calmer 15.05 to 17.01.04 on a tl-wdr4300.
Thank you very much!!!
If I flash this update on my Archer C7, do I need to re-install and re-configure OpenVPN again? (I am currently on v17.01.2)
BR.
If I flash this update on my Archer C7, do I need to re-install and re-configure OpenVPN again? (I am currently on v17.01.2)
This is explained in the upgrade guide.
Does someone else lost the 5 Ghz Wifi with the WDR3600 after this Upgrade?
Just wanted to ask before i open a topic 
Great to see the platform fixes for ar71xx, but still no squashfs-factory.bin for the tl-wr902ac?
Guess i could attempt to build my own image utilizing Heinz's 'kernel size partition' patch, but im just not that good yet!
Rep
Hi Knight, excuse me for my english, i am having a problem with the 5GHz Band in a AP-Client WDS configuration of 2 * WDR3600, for me is unstable, but the 2.4GHz band it's working, but i need the 5GHz band. i'll probably wait for a future release. Hope you can resolve your issue.
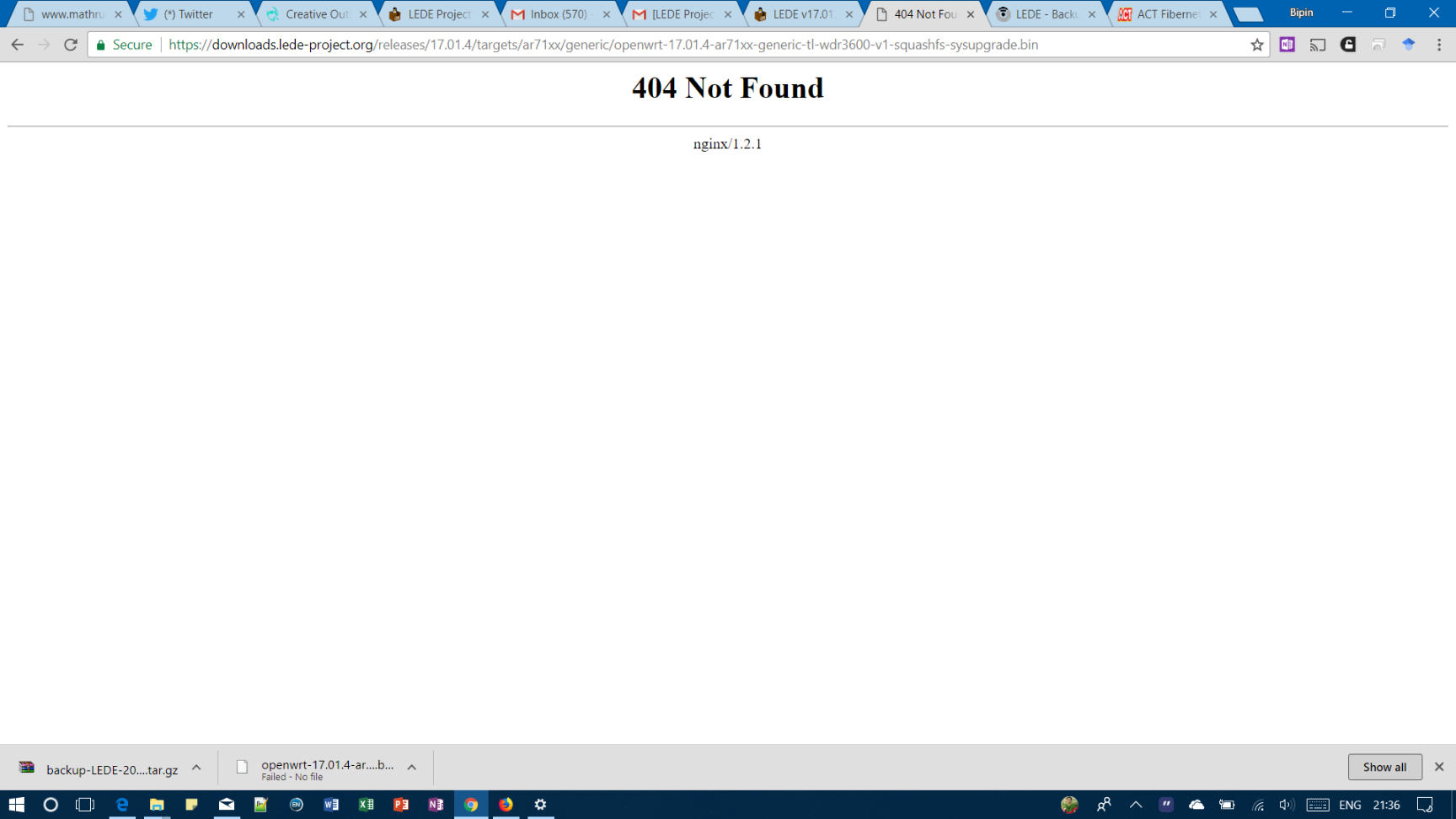
Hi, i am getting 404 error while trying to download latest images. i have tried from different pc's as well as ISP still the issue persists. can you please look into it?
After the update to this release my 5Ghz wifi is broken. Only 2,4 Ghz is online and available. If i try to stop and start it i get this stack trace.
[3705072.083768] ath: phy0: Unable to reset channel, reset status -5
[3709579.982387] ------------[ cut here ]------------
[3709579.987297] WARNING: CPU: 0 PID: 0 at compat-wireless-2017-01-31/net/mac80211/rx.c:4214 0x875a5cf0 [mac80211@87580000+0x607a0]()
[3709579.999230] Rate marked as an HT rate but passed status->rate_idx is not an MCS index [0-76]: 127 (0x7f)
[3709580.009030] Modules linked in: ath9k ath9k_common pppoe ppp_async iptable_nat ath9k_hw ath pppox ppp_generic nf_nat_ipv4 nf_conntrack_ipv6 nf_conntrack_ipv4 mac80211 ipt_REJECT ipt_MASQUERADE cfg80211 xt_time xt_tcpudp xt_state xt_nat xt_multiport xt_mark xt_mac xt_limit xt_conntrack xt_comment xt_TCPMSS xt_REDIRECT xt_LOG xt_CT slhc nf_reject_ipv4 nf_nat_redirect nf_nat_masquerade_ipv4 nf_nat nf_log_ipv4 nf_defrag_ipv6 nf_defrag_ipv4 nf_conntrack_rtcache nf_conntrack iptable_mangle iptable_filter ip_tables crc_ccitt compat ledtrig_usbport ip6t_REJECT nf_reject_ipv6 nf_log_ipv6 nf_log_common ip6table_mangle ip6table_filter ip6_tables x_tables ehci_platform ehci_hcd gpio_button_hotplug usbcore nls_base usb_common
[3709580.073719] CPU: 0 PID: 0 Comm: swapper Not tainted 4.4.92 #0
[3709580.079730] Stack : 803875b4 00000000 00000001 803e0000 00000000 00000000 00000000 00000000
[3709580.079730] 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
[3709580.079730] 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
[3709580.079730] 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
[3709580.079730] 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
[3709580.079730] ...
[3709580.116283] Call Trace:[<80071a8c>] 0x80071a8c
[3709580.121004] [<80071a8c>] 0x80071a8c
[3709580.124728] [<80081888>] 0x80081888
[3709580.128466] [<875a5cf0>] 0x875a5cf0 [mac80211@87580000+0x607a0]
[3709580.134662] [<800818e4>] 0x800818e4
[3709580.138393] [<8009b5d8>] 0x8009b5d8
[3709580.142126] [<875a5cf0>] 0x875a5cf0 [mac80211@87580000+0x607a0]
[3709580.148323] [<80260a70>] 0x80260a70
[3709580.152042] [<80260c54>] 0x80260c54
[3709580.155781] [<874f0388>] 0x874f0388 [ath9k_common@874f0000+0x4800]
[3709580.162256] [<874c77f4>] 0x874c77f4 [ath9k@874c0000+0x16650]
[3709580.168195] [<874c77d4>] 0x874c77d4 [ath9k@874c0000+0x16650]
[3709580.174127] [<874c4a44>] 0x874c4a44 [ath9k@874c0000+0x16650]
[3709580.180053] [<80084448>] 0x80084448
[3709580.183775] [<80083e04>] 0x80083e04
[3709580.187505] [<800a8014>] 0x800a8014
[3709580.191229] [<8006a990>] 0x8006a990
[3709580.194951] [<80060bf8>] 0x80060bf8
[3709580.198677]
[3709580.200369] ---[ end trace ada346d1ada346d1 ]---
[4715408.785174] ath: phy0: Unable to reset channel, reset status -5
[5016007.274721] ath: phy0: Unable to reset channel, reset status -5
Any ideas? My config has not changed 
Router: TP-Link TL-WDR3600 v1
Firmware: LEDE Reboot 17.01.4 r3560-79f57e422d / LuCI lede-17.01 branch (git-17.298.45605-07e7ff0)
Kernel Version: 4.4.92
Thanks
Tobias
cat /etc/config/network
cat /etc/config/wireless
Make sure to obscure the "option key" value(s) in the wireless config results before posting.