Well, just managed to sort out the problem with accessing my home server and all the services running on it. To be honest I was thinking that something is wrong with the routers routing or firewall rules, so i was testing a lot of things these days, most of them without realizing what they do, fortunately rid not break anything but finally got a solution. So the problem was not in my MT or Openwrt routers but in my Home servers firewall ....
i just had to allow everything from Wireguard subnet and it started working like a charm. Well thanks again to everyone and for your patience as well 
All the best and live long and prosperous!
please find down below the latest config files for both sides:
OpenWRT:
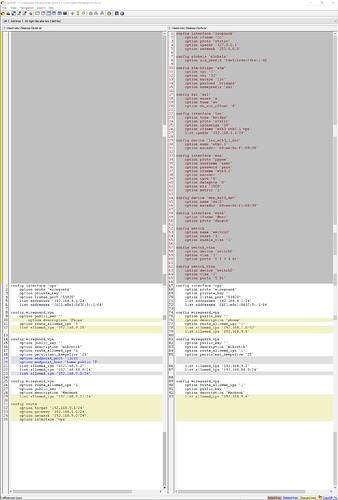
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fde5:fe4e:f4fe::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'a'
option tone 'av'
option ds_snr_offset '0'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ip6assign '60'
option ifname 'eth0 eth0.1 vpn'
list ipaddr '192.168.1.1/24'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr ''
config interface 'wan'
option proto 'pppoe'
option username ''
option password ''
option ifname 'eth0.2'
option macaddr ''
option ipv6 '0'
option delegate '0'
option mtu '1500'
option metric '1'
config device 'wan_dsl0_dev'
option name 'dsl0'
option macaddr ''
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 6t'
config interface 'vpn'
option proto 'wireguard'
option private_key ''
option listen_port '51820'
list addresses '192.168.9.1/24'
list addresses 'fdf1:e8a1:8d3f:9::1/64'
config wireguard_vpn
option public_key ''
option description 'phone'
option route_allowed_ips '1'
list allowed_ips '192.168.9.20'
config wireguard_vpn
option public_key ''
option description 'mikrotik'
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '192.168.9.2'
list allowed_ips '192.168.88.0/24'
list allowed_ips '192.168.9.0/24'
config wireguard_vpn
option route_allowed_ips '1'
option public_key ''
option description 'Macbook'
list allowed_ips '192.168.9.21'
config route
option target '192.168.88.0/24'
option interface 'vpn'
option gateway '192.168.9.1'
option netmask '255.255.255.0'
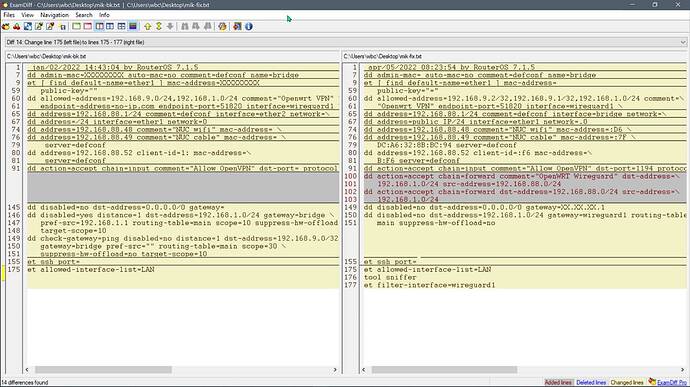
Mikrotik Side:
# 04/10/2022 08:59:44 by RouterOS 7.1.5
# software id = 2Y0D-P7Z5
#
# model = RB750Gr3
# serial number =
/interface bridge
add admin-mac= auto-mac=no comment=defconf name=bridge
/interface ethernet
set [ find default-name=ether1 ] mac-address=
/interface wireguard
add listen-port=13231 mtu=1420 name=wireguard1
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface lte apn
set [ find default=yes ] ip-type=ipv4 use-network-apn=no
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec proposal
set [ find default=yes ] disabled=yes enc-algorithms=3des
/ip pool
add name=dhcp ranges=192.168.88.30-192.168.88.80
add name=vpn-pool ranges=192.168.8.10-192.168.8.12
/ip dhcp-server
add address-pool=dhcp interface=bridge name=defconf
/port
set 0 name=serial0
/ppp profile
add dns-server=192.168.8.250 local-address=192.168.8.250 name=vpn-profile \
remote-address=vpn-pool use-encryption=yes
/routing table
add fib name=""
/user group
set full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,pas\
sword,web,sniff,sensitive,api,romon,dude,tikapp,rest-api"
/interface bridge port
add bridge=bridge comment=defconf ingress-filtering=no interface=ether2
add bridge=bridge comment=defconf ingress-filtering=no interface=ether3
add bridge=bridge comment=defconf ingress-filtering=no interface=ether4
add bridge=bridge comment=defconf ingress-filtering=no interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=all
/ipv6 settings
set disable-ipv6=yes max-neighbor-entries=8192
/interface l2tp-server server
set authentication=mschap1,mschap2
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/interface ovpn-server server
set auth=sha1 certificate=server-certificate cipher=aes128,aes192,aes256 \
default-profile=vpn-profile require-client-certificate=yes
/interface wireguard peers
add allowed-address=192.168.9.4/32 comment=Phone interface=wireguard1 \
public-key=""
add allowed-address=192.168.9.5/32 comment=MacBookAir interface=wireguard1 \
public-key=""
add allowed-address=\
192.168.9.2/32,192.168.88.0/24,192.168.1.0/24,192.168.9.0/24 comment=\
"Openwrt VPN" endpoint-address=OPENWRT DDNS IP endpoint-port=51820 \
interface=wireguard1 persistent-keepalive=25s public-key=\
""
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=\
192.168.88.0
add address=public IP/24 interface=ether1 network=public IP mask
add address=192.168.9.2/24 interface=wireguard1 network=192.168.9.0
/ip cloud
set update-time=no
/ip dhcp-client
add comment=defconf disabled=yes interface=ether1
/ip dhcp-server lease
add address=192.168.88.48 comment="NUC wifi" mac-address= \
server=defconf
add address=192.168.88.49 comment="NUC cable" mac-address= \
server=defconf
add address=192.168.88.43 comment="Raspberry pi 4" mac-address=\
server=defconf
add address=192.168.88.52 client-id= mac-address=\
server=defconf
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.49 gateway=\
192.168.88.1
/ip dns
set allow-remote-requests=yes servers=192.168.88.49
/ip dns static
add address=192.168.88.1 disabled=yes name=router.lan
add address=192.168.88.49 name="Home DNS"
/ip firewall filter
add action=accept chain=input comment="Allow OpenVPN" disabled=yes dst-port=\
1194 protocol=tcp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=accept chain=input comment="Wireguard VPN NUC" dst-port=13231 \
in-interface-list=WAN protocol=udp
add action=accept chain=input comment="Wireguard VPN" dst-address=\
192.168.88.0/24 src-address=192.168.9.0/24
add action=accept chain=input comment="Wireguard VPN" disabled=yes \
dst-address=192.168.9.0/24 in-interface=wireguard1 src-address=\
192.168.1.0/24
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=dst-nat chain=dstnat comment=Wireguard dst-port=52994 \
in-interface=ether1 protocol=udp to-addresses=192.168.88.49 to-ports=\
52994
add action=redirect chain=dstnat disabled=yes dst-port=53 protocol=tcp \
src-port="" to-ports=53
add action=redirect chain=dstnat disabled=yes dst-port=53 protocol=udp \
to-ports=53
/ip firewall service-port
set ftp disabled=yes
set tftp disabled=yes
set irc disabled=yes
set h323 disabled=yes
set sip disabled=yes
set pptp disabled=yes
set udplite disabled=yes
set dccp disabled=yes
set sctp disabled=yes
/ip ipsec policy
set 0 disabled=yes dst-address=0.0.0.0/0 src-address=0.0.0.0/0
/ip route
add disabled=no dst-address=0.0.0.0/0 gateway=
add disabled=no distance=1 dst-address=192.168.1.0/24 gateway=wireguard1 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=yes distance=1 dst-address=192.168.88.0/24 gateway=wireguard1 \
pref-src=0.0.0.0 routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh port=
/ppp secret
add name= profile=vpn-profile
/system clock
set time-zone-name=Europe/
/system identity
set name=MikroTikRouter
/system ntp client
set enabled=yes
/system ntp client servers
add address=192.168.88.49
/tool graphing interface
add
/tool graphing queue
add
/tool graphing resource
add
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
/tool sniffer
set filter-interface=wireguard1
So these configs solve all problems
Thanks again to everyone!