Hi,
I've followed the guide here: https://openwrt.org/docs/guide-user/network/wifi/wifiextenders/bridgedap#wireless_access_point_-_dumb_access_point_-_examples
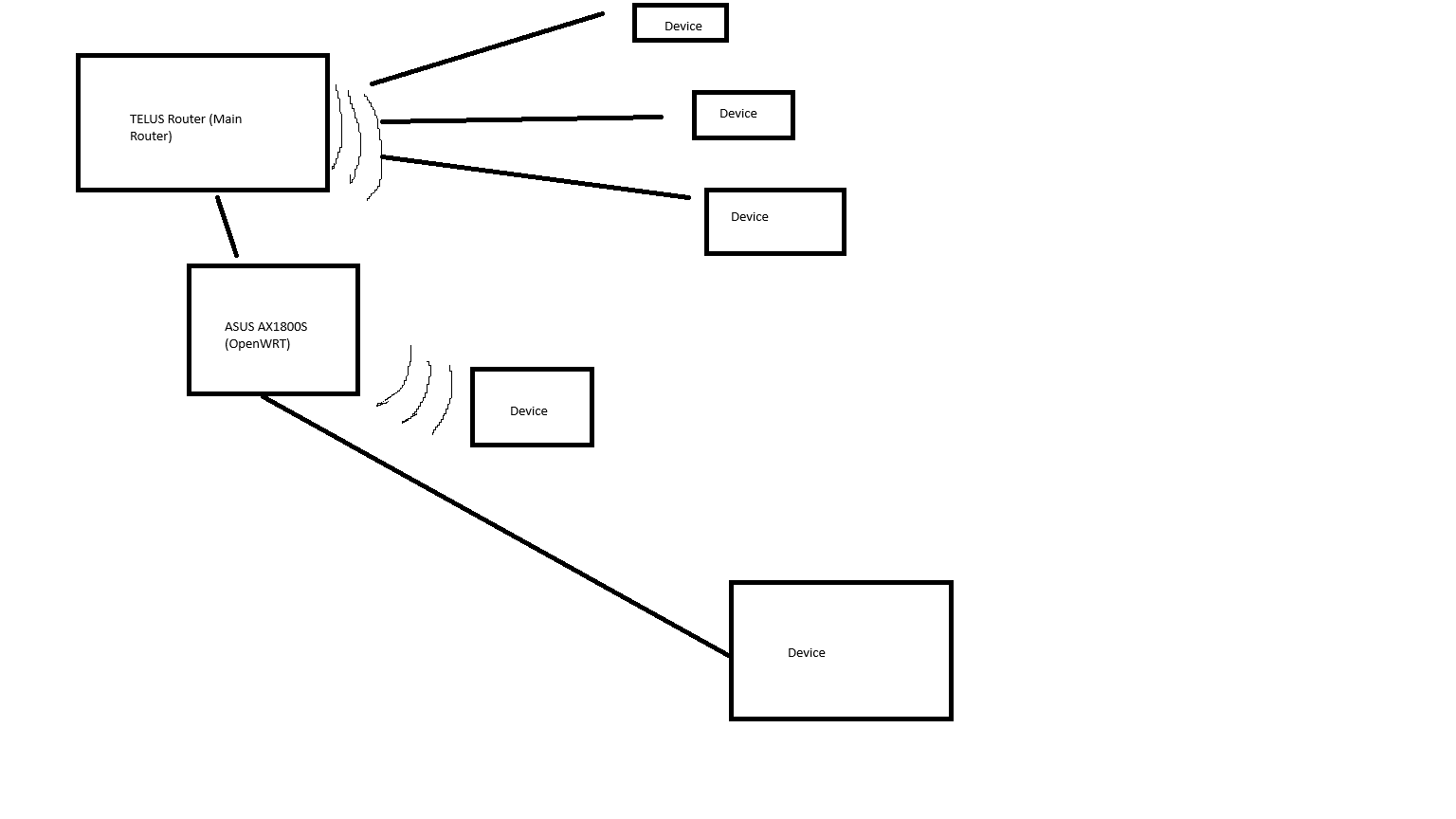
Ethernet works perfectly fine, but when I turn on my wireless... it works for a bit, and then doesn't. This is what I want set up:
I have the interface set up to use DHCP (i've tried with static and also not working)
I am not sure where to start troubleshooting.
Lucky1
October 10, 2024, 8:03am
2
Need some more info
1 Like
Lucky1
October 10, 2024, 5:30pm
4
Ok it's a MT7621 I'll presume it's the access point and not the router
save your settings "just in case"
uci add_list network.cfg030f15.ports=$(uci get network.wan.device)
uci del network.wan
uci set network.lan.proto="dhcp"
uci del network.lan.ipaddr
uci del network.lan.netmask
uci del network.lan.ip6assign
uci set network.lan.delegate='0'
uci del network.wan6
uci set network.lan6=interface
uci set network.lan6.proto='dhcpv6'
uci set network.lan6.device='@lan'
uci set network.lan6.reqaddress='try'
uci set network.lan6.reqprefix='no'
uci commit network
uci del firewall.cfg02dc81.network
uci set firewall.cfg02dc81.network='lan lan6'
uci commit firewall
/etc/init.d/dnsmasq disable
/etc/init.d/dnsmasq stop
uci del dhcp.lan
uci del dhcp.wan
uci del dhcp.odhcpd
uci set dhcp.lan=dhcp
uci set dhcp.lan.interface='lan'
uci set dhcp.lan.ignore='1'
uci add_list dhcp.lan.ra_flags='none'
uci commit dhcp
/etc/init.d/odhcpd disable
/etc/init.d/odhcpd stop
echo "# Put your custom commands here that should be executed once" > /etc/rc.local
echo "# the system init finished. By default this file does nothing." >> /etc/rc.local
echo "" >> /etc/rc.local
echo "/etc/init.d/dnsmasq disable" >> /etc/rc.local
echo "/etc/init.d/dnsmasq stop" >> /etc/rc.local
echo "/etc/init.d/odhcpd disable" >> /etc/rc.local
echo "/etc/init.d/odhcpd stop" >> /etc/rc.local
echo "exit 0" >> /etc/rc.local
reboot
1 Like
Before making any changes as suggested by @Lucky1 , let's just take a look at your current configuration.
Importantly, we also need to know what port on the AP is being used for the uplink.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
1 Like
Here's the output from the commands, thanks!
root@OpenWrt:~# ubus call system board
config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/fir{
"kernel": "5.15.162",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:4",
"model": "ASUS RT-AX54",
"board_name": "asus,rt-ax54",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.4",
"revision": "r24012-d8dd03c46f",
"target": "ramips/mt7621",
"description": "OpenWrt 23.05.4 r24012-d8dd03c46f"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd59:d8a7:cbf5::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'wan'
option acceptlocal '1'
config interface 'lan'
option device 'br-lan'
option proto 'dhcp'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '1'
option band '2g'
option htmode 'HE20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0+1'
option channel '64'
option band '5g'
option htmode 'HE40'
option country 'CA'
option cell_density '0'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'LAN Solo'
option encryption 'psk2'
option key 'Dx$3A#qf'
option disabled '1'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Remove the acceptlocal line below:
Looking at your 5G radio config, I think that the problem is relate to your channel selection:
You've chosen a DFS channel which means that it must immediately shut down if it gets a radar hit. I'd recommend trying somethign that is not in the DFS range.
Obviously, the other thing to note is that you have both bands disabled currently.
lancem26:
So far so good, it works! But I did have it set to a non DFS channel (48) before and it still stopped working after a while.
What does option acceptlocal '1' mean?
So far so good, it works! But I did have it set to a non DFS channel (48) before and it still stopped working after a while.
What does option acceptlocal '1' mean?
Also, after applying the changes (not sure if related) I am now unable to access my unraid file share both using hostname and the ip in file explorer. I can access the gui just fine on the browser.
@psherman so it happened again, my wifi isn’t working.
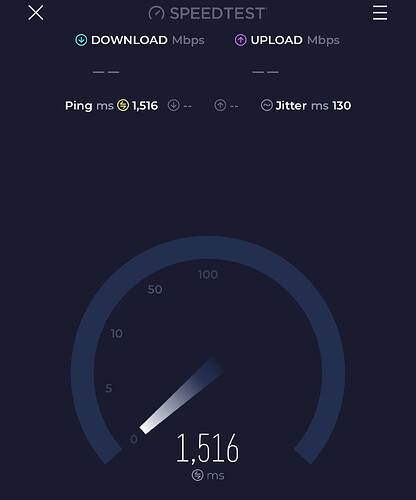
I tried this, wifi worked on my phone for a speedtest. After 5 minutes, it stopped working. I even switched the wifi to a non DFS channel (48) now LuCI is also having issues loading anything. I can still ssh fine though.
Lucky1
October 13, 2024, 8:14pm
13
I'm I bit lost on where you are now
At this point, this type of behavior doesn't seem like it is WiFi related. Something is happening with the AP itself. Please test a wired connection and see if you can access LuCI when connecting via Ethernet. (if it's too late to test with this current occurrence of the issue, please do so the next time it manifests.)
Just updated to 23.05.5
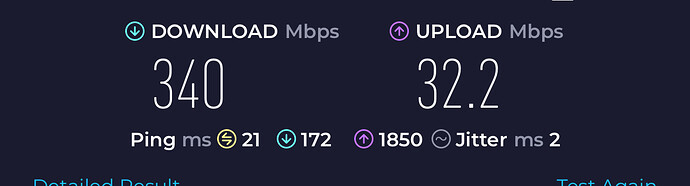
Ran the SSH scripts. I was able to do one speedtest (but it started having issues once it was uploading time) and then the second time just doesn’t work.
I believe it’s wifi related because as soon as I reboot the router and disable wireless… it won’t “crap” out on me. But as soon as I enable wireless and then run some speed test from my phone, it runs into the issue again.
It could be exacerbated by WiFi if the situation is, for example, and out of memory condition.
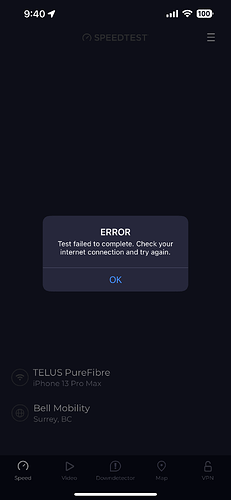
Here's the "trouble loading" thing I am talking about:
Here's my output of logread:
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.188021] br-lan: port 6(phy1-ap0) entered blocking state
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.193783] br-lan: port 6(phy1-ap0) entered disabled state
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.200101] device phy1-ap0 entered promiscuous mode
Sun Oct 13 13:46:51 2024 daemon.notice hostapd: phy1-ap0: interface state UNINITIALIZED->HT_SCAN
Sun Oct 13 13:46:51 2024 daemon.notice netifd: lan (2150): udhcpc: sending renew to server 192.168.1.254
Sun Oct 13 13:46:51 2024 daemon.notice netifd: lan (2150): udhcpc: lease of 192.168.1.26 obtained from 192.168.1.254, lease time 86400
Sun Oct 13 13:46:51 2024 daemon.notice netifd: Wireless device 'radio1' is now up
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.677451] IPv6: ADDRCONF(NETDEV_CHANGE): phy1-ap0: link becomes ready
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.684687] br-lan: port 6(phy1-ap0) entered blocking state
Sun Oct 13 13:46:51 2024 kern.info kernel: [ 618.690360] br-lan: port 6(phy1-ap0) entered forwarding state
Sun Oct 13 13:46:51 2024 daemon.notice netifd: Network device 'phy1-ap0' link is up
Sun Oct 13 13:46:51 2024 daemon.notice hostapd: phy1-ap0: interface state HT_SCAN->ENABLED
Sun Oct 13 13:46:51 2024 daemon.notice hostapd: phy1-ap0: AP-ENABLED
Sun Oct 13 13:47:20 2024 daemon.info hostapd: phy1-ap0: STA 92:ff:bc:b4:d7:ec IEEE 802.11: authenticated
Sun Oct 13 13:47:20 2024 daemon.info hostapd: phy1-ap0: STA 92:ff:bc:b4:d7:ec IEEE 802.11: associated (aid 1)
Sun Oct 13 13:47:20 2024 daemon.notice hostapd: phy1-ap0: AP-STA-CONNECTED 92:ff:bc:b4:d7:ec auth_alg=open
Sun Oct 13 13:47:20 2024 daemon.info hostapd: phy1-ap0: STA 92:ff:bc:b4:d7:ec WPA: pairwise key handshake completed (RSN)
Sun Oct 13 13:47:20 2024 daemon.notice hostapd: phy1-ap0: EAPOL-4WAY-HS-COMPLETED 92:ff:bc:b4:d7:ec
Sun Oct 13 13:49:27 2024 daemon.notice hostapd: phy1-ap0: AP-STA-DISCONNECTED 92:ff:bc:b4:d7:ec
Sun Oct 13 13:49:28 2024 daemon.info hostapd: phy1-ap0: STA 92:ff:bc:b4:d7:ec IEEE 802.11: disassociated
Sun Oct 13 13:49:29 2024 daemon.info hostapd: phy1-ap0: STA 92:ff:bc:b4:d7:ec IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
Sun Oct 13 13:49:48 2024 kern.err kernel: [ 796.029587] mt7915e 0000:02:00.0: Message 00005aed (seq 5) timeout
Sun Oct 13 13:50:09 2024 kern.err kernel: [ 816.509618] mt7915e 0000:02:00.0: Message 000026ed (seq 6) timeout
Sun Oct 13 13:50:29 2024 kern.err kernel: [ 836.989609] mt7915e 0000:02:00.0: Message 00005aed (seq 7) timeout
Sun Oct 13 13:50:50 2024 kern.err kernel: [ 857.469599] mt7915e 0000:02:00.0: Message 00005aed (seq 8) timeout
Sun Oct 13 13:51:10 2024 kern.err kernel: [ 877.949510] mt7915e 0000:02:00.0: Message 00005aed (seq 9) timeout
Sun Oct 13 13:51:31 2024 kern.err kernel: [ 898.429462] mt7915e 0000:02:00.0: Message 00005aed (seq 10) timeout
Sun Oct 13 13:51:51 2024 daemon.notice hostapd: nl80211: nl80211_recv_beacons->nl_recvmsgs failed: -5
Sun Oct 13 13:51:51 2024 kern.err kernel: [ 918.909396] mt7915e 0000:02:00.0: Message 000026ed (seq 11) timeout
Sun Oct 13 13:52:12 2024 kern.err kernel: [ 939.389340] mt7915e 0000:02:00.0: Message 00005aed (seq 12) timeout
Sun Oct 13 13:52:32 2024 kern.err kernel: [ 959.869256] mt7915e 0000:02:00.0: Message 00005aed (seq 13) timeout
Sun Oct 13 13:52:53 2024 kern.err kernel: [ 980.349232] mt7915e 0000:02:00.0: Message 00005aed (seq 14) timeout
Sun Oct 13 13:53:13 2024 kern.err kernel: [ 1000.829125] mt7915e 0000:02:00.0: Message 00005aed (seq 15) timeout
Sun Oct 13 13:53:34 2024 kern.err kernel: [ 1021.309009] mt7915e 0000:02:00.0: Message 00005aed (seq 1) timeout
Sun Oct 13 13:53:54 2024 kern.err kernel: [ 1041.788919] mt7915e 0000:02:00.0: Message 000026ed (seq 2) timeout
Sun Oct 13 13:54:15 2024 kern.err kernel: [ 1062.268834] mt7915e 0000:02:00.0: Message 00005aed (seq 3) timeout
Sun Oct 13 13:54:35 2024 kern.err kernel: [ 1082.748696] mt7915e 0000:02:00.0: Message 00005aed (seq 4) timeout
Sun Oct 13 13:54:56 2024 kern.err kernel: [ 1103.228576] mt7915e 0000:02:00.0: Message 00005aed (seq 5) timeout
Sun Oct 13 13:55:16 2024 kern.err kernel: [ 1123.708477] mt7915e 0000:02:00.0: Message 00005aed (seq 6) timeout
Sun Oct 13 13:55:37 2024 kern.err kernel: [ 1144.188350] mt7915e 0000:02:00.0: Message 000026ed (seq 7) timeout
Sun Oct 13 13:55:57 2024 daemon.notice hostapd: nl80211: nl80211_recv_beacons->nl_recvmsgs failed: -5
Sun Oct 13 13:55:57 2024 kern.err kernel: [ 1164.668256] mt7915e 0000:02:00.0: Message 00005aed (seq 8) timeout
Sun Oct 13 13:56:18 2024 kern.err kernel: [ 1185.148143] mt7915e 0000:02:00.0: Message 00005aed (seq 9) timeout
Sun Oct 13 13:56:38 2024 kern.err kernel: [ 1205.628059] mt7915e 0000:02:00.0: Message 00005aed (seq 10) timeout
Sun Oct 13 13:56:58 2024 kern.err kernel: [ 1226.107948] mt7915e 0000:02:00.0: Message 00005aed (seq 11) timeout
Sun Oct 13 13:57:14 2024 authpriv.info dropbear[3982]: Child connection from 192.168.1.126:51343
Sun Oct 13 13:57:14 2024 authpriv.info dropbear[3982]: Exit before auth from <192.168.1.126:51343>: Error reading: Connection reset by peer
Sun Oct 13 13:57:19 2024 kern.err kernel: [ 1246.587898] mt7915e 0000:02:00.0: Message 00005aed (seq 12) timeout
Sun Oct 13 13:57:39 2024 kern.err kernel: [ 1267.067803] mt7915e 0000:02:00.0: Message 000026ed (seq 13) timeout
Sun Oct 13 13:57:45 2024 authpriv.info dropbear[3983]: Child connection from 192.168.1.126:51376
https://openwrt.org/toh/asus/rt-ax54
According to this page, it has 256MB ram. Is there anything I can start to look at to decrease my ram usage?
Is this tested with Ethernet or WiFi?