I'm really confused what Ur trying to do?
But if you want wire guard that can acces your lan and wan network.
I think that you probably want to have lan to wan acces?
Or is it a offline network?
Could you please upload Ur /etc/config/network config or UCI show network?
It's a bad idea if this is your router to run wan and lan inside the same interface because there is no firewall then.
Also masquerade needs to be on on the wan firewall, only IPv6 is big enough that every device in your home network could get a IP address, probably IPv6 still will being using masquerade (I'm not sure Dow)
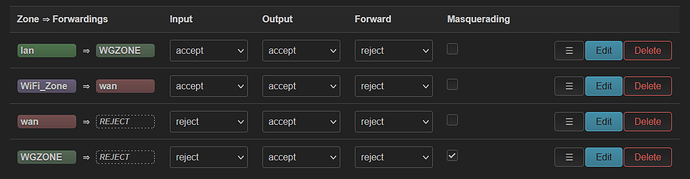
You need something like:
Lan -> wan
Wlan -> wan
Wire guard -> wan and lan masquerade on
Wan -> nothing masquerade on
But don't bridge your wan trough your lan or wlan, can't think of a single reason except maybe mesh or clients.
Yeah you get your lan working trough VPN because your lan makes a connection trough VPN that masquerade that IP, that part makes sense, but how it reached the wan?
If I understand it correctly still learning, lets call it the firewall pointers.
You make zone that zone can go to a different zone and can receive from zone.
The receive zone you don't need to be adjusted because they will be automatic being made by the forward zone (go to zone).
(Packet is the message that a device send trough the internet)
Every packet will be checked for a connection state.
Lan:
A Interface lan has a DHCP running in range 192.168.2.x
Has firewall zone lan attached to it, that zone only can reach the wan zone.
And
Wifi:
A Interface wlan has a DHCP running in range 192.168.3.x
Has firewall zone wlan attached to it, that zone also only can reach the wan zone.
Wan are all the devices outside your home (websites, Minecraft servers etc)
Lan and wlan are all the devices inside your home.
The wan can't reach your lan/wlan.
Unless the devices on your WLAN/lan network first have made a connection to a device on the wan.
Because if the device inside your home network makes the connection first, the message back from the wan will be checked if there is a connection between the two. And if that connection state is not invalid then the message from the wan to WLAN/lan will be accepted.
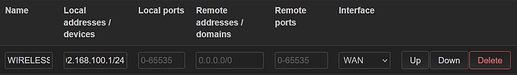
Also this can be bypassed by port forwarding but thats only needed if a device outside your home (wan) needs to established the connection first on the inside of your home.
That why you needed to forward wireguard.