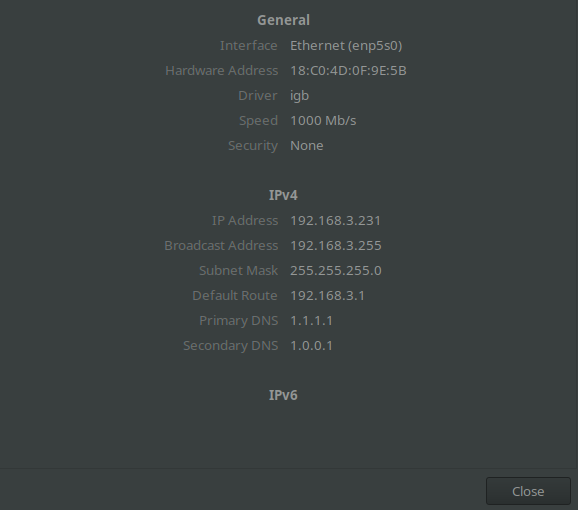
I have a similar problem in migrating my Wrt1900acs from a 4.19 kernel to current DSA-enabled 5.4.140 (OpenWrt SNAPSHOT, r17397-669d920e27).
The network setup result (ip a s, ip r s, ip -6 r s) on the router looks OK, router connectivity to the internet works, IPv6 assignment on LAN works.
Some observations:
- My /etc/config/firewall is (modulo some minor changes) a copy/paste from my working old setup.
- I was therefore pretty surprised when I compared the outputs of iptables-save and ip6tables-save of old and new configurations and found many differences, see below (ip6tables diffs are similar).
The significant differences seem to be always in rules with -i/-o pppoe-wan or -i/-o $WAN_DEVICE.
- The diffs were even bigger in a prior firmware where I had some nftables stuff compiled in.
- So my current suspicion is that the problem is in the list of kernel modules and/or in the firewall script which is somehow not able to deal with a wan device which is a DSA bridge port device.
Unfortunately, I am now out of ideas on how to debug this further. Any advice appreciated.
My setup:
- sqm-scripts are present, but disabled
- If there is any hw offloading it must be enabled by some default, I am sure that I did not enable anything in this direction.
WAN
- Router connected to VDSL modem in bridge mode
- Connection to ISP via pppoe with tagged VLAN 40
- IPv4/IPv6 dualstack, IPv6 /56 prefix delegated via odhcp6c.
LAN
- 3 subnetworks separated with VLANs,
- DHCP, DHCPv6 and RA all done by dnsmasq.
- no odhcp6d
$ cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdREDACTED::/48'
option enable_vlan_filtering '1'
config device
option name 'br-lan' # FIXME: not appropriate anymore, br0?
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'wan'
#option macaddr '58:REDACTED'
config bridge-vlan
# PVID 1
option device 'br-lan'
option vlan '1'
list ports 'lan1:u*'
list ports 'lan2:u*'
config bridge-vlan
# PVID 2
option device 'br-lan'
option vlan '2'
list ports 'wan:u*'
config bridge-vlan
option device 'br-lan'
option vlan '3'
list ports 'lan3'
config bridge-vlan
option device 'br-lan'
option vlan '39'
list ports 'lan4'
config bridge-vlan
option device 'br-lan'
option vlan '40'
list ports 'wan:t'
# no effect on MAC, but on LL-addr: option macaddr '5a:REDACTED'
config interface 'lan'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6hint '0'
option ip6ifaceid '::1'
option ip6assign '60'
list ip6addr 'fdREDACTED::1/128'
config interface 'vlan3'
option device 'br-lan.3'
option proto 'static'
option ipaddr '192.168.32.1'
option netmask '255.255.255.0'
option ip6hint '10'
option ip6ifaceid '::1'
option ip6assign '60'
list ip6addr 'fdREDACTED:10::1'
config interface 'vlan39'
option device 'br-lan.39'
option proto 'static'
option ipaddr '192.168.64.1'
option netmask '255.255.255.0'
# don't assign a global IPv6, which VoIP phone would pick up
# and cause renumbering problems
#option ip6hint '20'
#option ip6ifaceid '::1'
#option ip6assign '64'
list ip6addr 'fdREDACTED:20::1/64'
config interface 'wan'
option device 'br-lan.40'
option proto 'pppoe'
option peerdns '1'
option defaultroute '1'
option username 'REDACTED@mdsl.mnet-online.de'
option ipv6 'auto'
# bad, seems to interfere with 'option ipv6 auto' above
#config interface 'wan_6'
# option device '@wan'
# option proto 'dhcpv6'
$ cat /etc/config/firewall
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name 'vlan3'
list network 'vlan3'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'vlan39'
list network 'vlan39'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name wan
list network 'wan'
#list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
config forwarding
option src 'lan'
option dest 'vlan3'
config forwarding
option src 'lan'
option dest 'vlan39'
config forwarding
option src 'vlan3'
option dest 'wan'
config forwarding
option src 'vlan39'
option dest 'wan'
config forwarding
option src 'vlan3'
option dest 'lan'
config forwarding
option src 'vlan39'
option dest 'lan'
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
# allow interoperability with traceroute classic
# note that traceroute uses a fixed port range, and depends on getting
# back ICMP Unreachables. if we're operating in DROP mode, it won't
# work so we explicitly REJECT packets on these ports.
config rule
option name Support-UDP-Traceroute
option src wan
option dest_port 33434:33689
option proto udp
option family ipv4
option target REJECT
option enabled false
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
### EXAMPLE CONFIG SECTIONS
# deleted, not used
itables.conf: old setup, iptables_0823.conf: new setup
Note: port 5060 (sip) not yet configured in new setup
$ diff -u iptables.conf iptables_0823.conf
--- iptables.conf 2021-08-22 10:01:43.153680550 +0200
+++ iptables_0823.conf 2021-08-24 10:19:27.048911802 +0200
@@ -1,9 +1,9 @@
-# Generated by iptables-save v1.8.4 on Sat Aug 21 08:33:07 2021
+# Generated by iptables-save v1.8.7 on Tue Aug 24 08:18:21 2021
*nat
-:PREROUTING ACCEPT [15234:899888]
-:INPUT ACCEPT [6567:491564]
-:OUTPUT ACCEPT [3210:215236]
-:POSTROUTING ACCEPT [767:35739]
+:PREROUTING ACCEPT [92:5408]
+:INPUT ACCEPT [31:2095]
+:OUTPUT ACCEPT [36:2507]
+:POSTROUTING ACCEPT [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vlan39_rule - [0:0]
@@ -23,17 +23,15 @@
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
--A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
--A PREROUTING -i br-vlan3 -m comment --comment "!fw3" -j zone_vlan3_prerouting
--A PREROUTING -i br-vlan39 -m comment --comment "!fw3" -j zone_vlan39_prerouting
+-A PREROUTING -i br-lan.1 -m comment --comment "!fw3" -j zone_lan_prerouting
+-A PREROUTING -i br-lan.3 -m comment --comment "!fw3" -j zone_vlan3_prerouting
+-A PREROUTING -i br-lan.39 -m comment --comment "!fw3" -j zone_vlan39_prerouting
-A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
--A PREROUTING -i wan -m comment --comment "!fw3" -j zone_wan_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
--A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
--A POSTROUTING -o br-vlan3 -m comment --comment "!fw3" -j zone_vlan3_postrouting
--A POSTROUTING -o br-vlan39 -m comment --comment "!fw3" -j zone_vlan39_postrouting
+-A POSTROUTING -o br-lan.1 -m comment --comment "!fw3" -j zone_lan_postrouting
+-A POSTROUTING -o br-lan.3 -m comment --comment "!fw3" -j zone_vlan3_postrouting
+-A POSTROUTING -o br-lan.39 -m comment --comment "!fw3" -j zone_vlan39_postrouting
-A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
--A POSTROUTING -o wan -m comment --comment "!fw3" -j zone_wan_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_vlan39_postrouting -m comment --comment "!fw3: Custom vlan39 postrouting rule chain" -j postrouting_vlan39_rule
@@ -44,39 +42,31 @@
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
-# Completed on Sat Aug 21 08:33:07 2021
-# Generated by iptables-save v1.8.4 on Sat Aug 21 08:33:07 2021
+# Completed on Tue Aug 24 08:18:21 2021
+# Generated by iptables-save v1.8.7 on Tue Aug 24 08:18:21 2021
*raw
-:PREROUTING ACCEPT [144441:89476582]
-:OUTPUT ACCEPT [24537:1750373]
+:PREROUTING ACCEPT [284:20386]
+:OUTPUT ACCEPT [187:15288]
:zone_lan_helper - [0:0]
:zone_vlan39_helper - [0:0]
:zone_vlan3_helper - [0:0]
--A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
--A PREROUTING -i br-vlan3 -m comment --comment "!fw3: vlan3 CT helper assignment" -j zone_vlan3_helper
--A PREROUTING -i br-vlan39 -m comment --comment "!fw3: vlan39 CT helper assignment" -j zone_vlan39_helper
+-A PREROUTING -i br-lan.1 -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
+-A PREROUTING -i br-lan.3 -m comment --comment "!fw3: vlan3 CT helper assignment" -j zone_vlan3_helper
+-A PREROUTING -i br-lan.39 -m comment --comment "!fw3: vlan39 CT helper assignment" -j zone_vlan39_helper
COMMIT
-# Completed on Sat Aug 21 08:33:07 2021
-# Generated by iptables-save v1.8.4 on Sat Aug 21 08:33:07 2021
+# Completed on Tue Aug 24 08:18:21 2021
+# Generated by iptables-save v1.8.7 on Tue Aug 24 08:18:21 2021
*mangle
-:PREROUTING ACCEPT [144440:89476506]
-:INPUT ACCEPT [28941:2238551]
-:FORWARD ACCEPT [115499:87237955]
-:OUTPUT ACCEPT [24537:1750373]
-:POSTROUTING ACCEPT [140027:88987968]
+:PREROUTING ACCEPT [284:20386]
+:INPUT ACCEPT [266:18874]
+:FORWARD ACCEPT [0:0]
+:OUTPUT ACCEPT [187:15288]
+:POSTROUTING ACCEPT [187:15288]
-A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
--A FORWARD -o wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
--A POSTROUTING -p udp -m udp --sport 5060 --dport 5060 -m comment --comment "mark for VLAN PCP=>5" -j CLASSIFY --set-class 0000:0004
+-A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
-# Completed on Sat Aug 21 08:33:07 2021
-# Generated by iptables-save v1.8.4 on Sat Aug 21 08:33:07 2021
+# Completed on Tue Aug 24 08:18:21 2021
+# Generated by iptables-save v1.8.7 on Tue Aug 24 08:18:21 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
@@ -123,32 +113,29 @@
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
--A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
--A INPUT -i br-vlan3 -m comment --comment "!fw3" -j zone_vlan3_input
--A INPUT -i br-vlan39 -m comment --comment "!fw3" -j zone_vlan39_input
+-A INPUT -i br-lan.1 -m comment --comment "!fw3" -j zone_lan_input
+-A INPUT -i br-lan.3 -m comment --comment "!fw3" -j zone_vlan3_input
+-A INPUT -i br-lan.39 -m comment --comment "!fw3" -j zone_vlan39_input
-A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
--A INPUT -i wan -m comment --comment "!fw3" -j zone_wan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
--A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
--A FORWARD -i br-vlan3 -m comment --comment "!fw3" -j zone_vlan3_forward
--A FORWARD -i br-vlan39 -m comment --comment "!fw3" -j zone_vlan39_forward
+-A FORWARD -i br-lan.1 -m comment --comment "!fw3" -j zone_lan_forward
+-A FORWARD -i br-lan.3 -m comment --comment "!fw3" -j zone_vlan3_forward
+-A FORWARD -i br-lan.39 -m comment --comment "!fw3" -j zone_vlan39_forward
-A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
--A FORWARD -i wan -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
--A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
--A OUTPUT -o br-vlan3 -m comment --comment "!fw3" -j zone_vlan3_output
--A OUTPUT -o br-vlan39 -m comment --comment "!fw3" -j zone_vlan39_output
+-A OUTPUT -o br-lan.1 -m comment --comment "!fw3" -j zone_lan_output
+-A OUTPUT -o br-lan.3 -m comment --comment "!fw3" -j zone_vlan3_output
+-A OUTPUT -o br-lan.39 -m comment --comment "!fw3" -j zone_vlan39_output
-A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
--A OUTPUT -o wan -m comment --comment "!fw3" -j zone_wan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
--A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
+-A zone_lan_dest_ACCEPT -o br-lan.1 -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to vlan3 forwarding policy" -j zone_vlan3_dest_ACCEPT
@@ -160,8 +147,8 @@
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
--A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
--A zone_vlan39_dest_ACCEPT -o br-vlan39 -m comment --comment "!fw3" -j ACCEPT
+-A zone_lan_src_ACCEPT -i br-lan.1 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
+-A zone_vlan39_dest_ACCEPT -o br-lan.39 -m comment --comment "!fw3" -j ACCEPT
-A zone_vlan39_forward -m comment --comment "!fw3: Custom vlan39 forwarding rule chain" -j forwarding_vlan39_rule
-A zone_vlan39_forward -m comment --comment "!fw3: Zone vlan39 to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_vlan39_forward -m comment --comment "!fw3: Zone vlan39 to lan forwarding policy" -j zone_lan_dest_ACCEPT
@@ -172,8 +159,8 @@
-A zone_vlan39_input -m comment --comment "!fw3" -j zone_vlan39_src_ACCEPT
-A zone_vlan39_output -m comment --comment "!fw3: Custom vlan39 output rule chain" -j output_vlan39_rule
-A zone_vlan39_output -m comment --comment "!fw3" -j zone_vlan39_dest_ACCEPT
--A zone_vlan39_src_ACCEPT -i br-vlan39 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
--A zone_vlan3_dest_ACCEPT -o br-vlan3 -m comment --comment "!fw3" -j ACCEPT
+-A zone_vlan39_src_ACCEPT -i br-lan.39 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
+-A zone_vlan3_dest_ACCEPT -o br-lan.3 -m comment --comment "!fw3" -j ACCEPT
-A zone_vlan3_forward -m comment --comment "!fw3: Custom vlan3 forwarding rule chain" -j forwarding_vlan3_rule
-A zone_vlan3_forward -m comment --comment "!fw3: Zone vlan3 to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_vlan3_forward -m comment --comment "!fw3: Zone vlan3 to lan forwarding policy" -j zone_lan_dest_ACCEPT
@@ -184,13 +171,10 @@
-A zone_vlan3_input -m comment --comment "!fw3" -j zone_vlan3_src_ACCEPT
-A zone_vlan3_output -m comment --comment "!fw3: Custom vlan3 output rule chain" -j output_vlan3_rule
-A zone_vlan3_output -m comment --comment "!fw3" -j zone_vlan3_dest_ACCEPT
--A zone_vlan3_src_ACCEPT -i br-vlan3 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
+-A zone_vlan3_src_ACCEPT -i br-lan.3 -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
--A zone_wan_dest_ACCEPT -o wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
--A zone_wan_dest_ACCEPT -o wan -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
--A zone_wan_dest_REJECT -o wan -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
@@ -200,13 +184,10 @@
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
--A zone_wan_input -p tcp -m tcp --dport 5060 -m comment --comment "!fw3: Allow-SIP-SIPS-to-kamailio" -j ACCEPT
--A zone_wan_input -p udp -m udp --dport 5060 -m comment --comment "!fw3: Allow-SIP-SIPS-to-kamailio" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
--A zone_wan_src_REJECT -i wan -m comment --comment "!fw3" -j reject
COMMIT
-# Completed on Sat Aug 21 08:33:07 2021
+# Completed on Tue Aug 24 08:18:21 2021