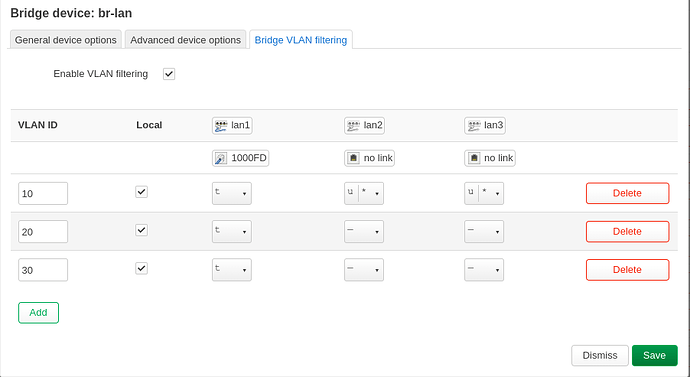
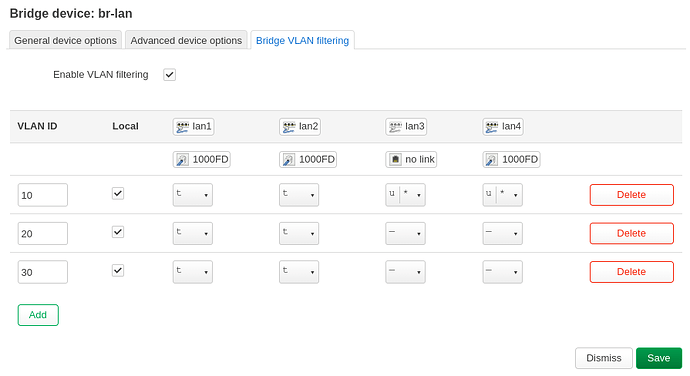
Is your switch managed or unmanaged?
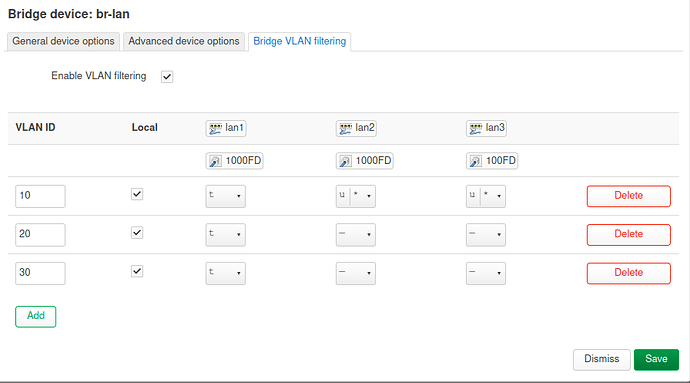
If it's a managed switch, you can use VLAN trunks. That's one physical cable carrying several logical VLANs. IMHO the easiest configuration is to configure all VLANs as tagged on this port. The advantage is that you only need a single cable to carry all VLANs. On your switch you can then configure the remaining ports as "untagged" as you require for your Ethernet devices.
If it's an unmanaged switch, matters are a bit more complex. You can still use tagged VLANs, but the switch won't be aware of this and will not be able to isolate the ports. Hence, you have a risk of mixing up guest network and private network if you add additional wired devices to the switch. If only the APs and routers are involved, an unmanaged switch should work fine.
In both cases you will only need one cable per device.
As an alternative, you can use two cables with untagged VLANs, but then you cannot mix them at an unmanaged switch since you have to isolate the different networks. Thus, you need either a managed switch to perform the isolation (but then you can use VLANs anyway) or two switches (but given the cost and power consumption of a switch, that's not a very economical solution).
An example (my setup):
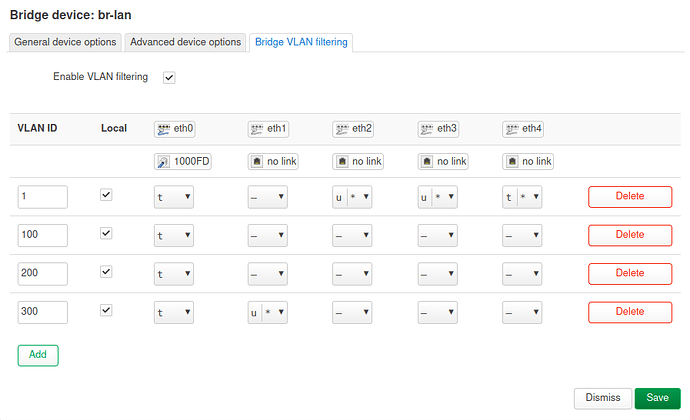
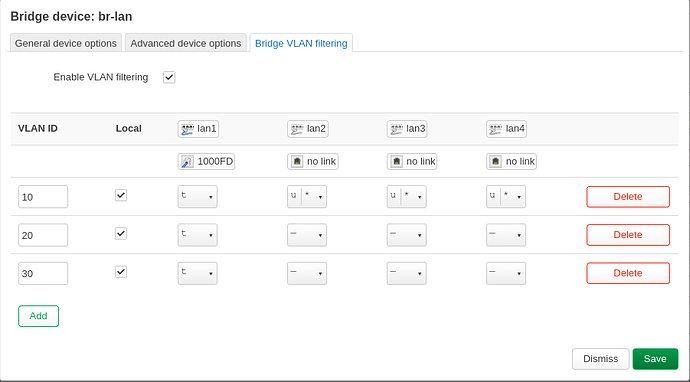
The router - Ubiquiti ER-X, only lan1 is used as VLAN trunk port, so this port is configured as "tagged" on all VLANs. Please be aware that this is a DSA device. 4 defined VLANs:
- 1: Management interface
- 100: Modem, only the router and the modem are in this VLAN; I have a PPPoE connection over VLAN 100
- 200: Private VLAN for the majority of devices
- 300: IoT VLAN for all "insecure" devices
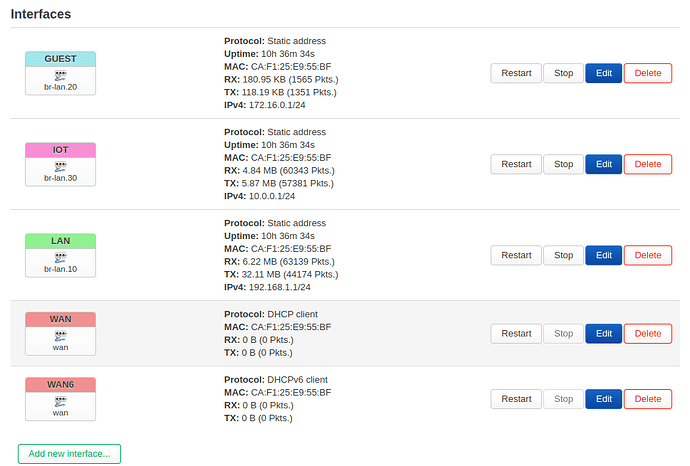
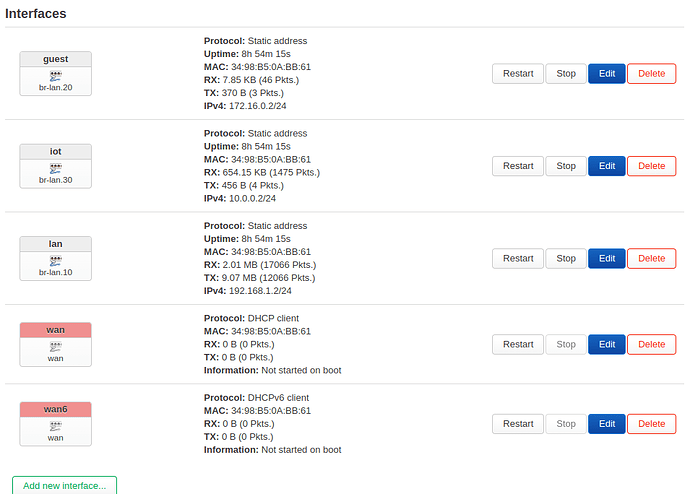
The main router provides three different DHCP servers in different subnets.
/etc/config/network:
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
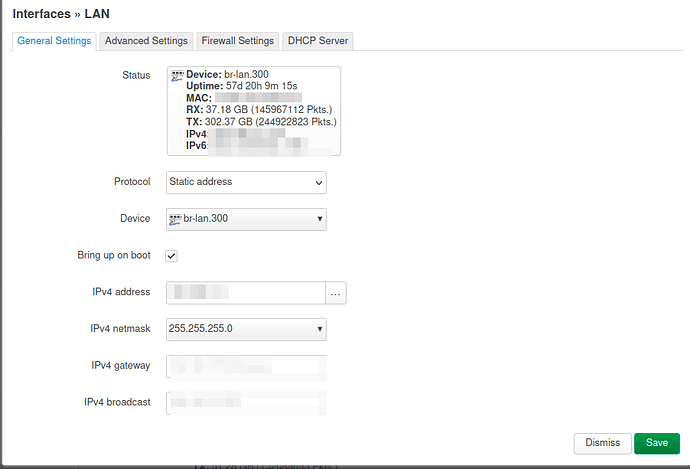
option device 'br-lan.300'
option ipaddr '192.168.17.1'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth0:t'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
config bridge-vlan
option device 'br-lan'
option vlan '100'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '200'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '300'
list ports 'eth0:t'
config interface 'Management'
option proto 'static'
option device 'br-lan.1'
option netmask '255.255.255.0'
option ipaddr '192.168.20.1'
config interface 'Haustechnik'
option proto 'static'
option device 'br-lan.200'
option ipaddr '192.168.18.1'
option netmask '255.255.255.0'
config interface 'modem'
option proto 'static'
option device 'br-lan.100'
option ipaddr '10.0.0.1'
option netmask '255.255.255.0'
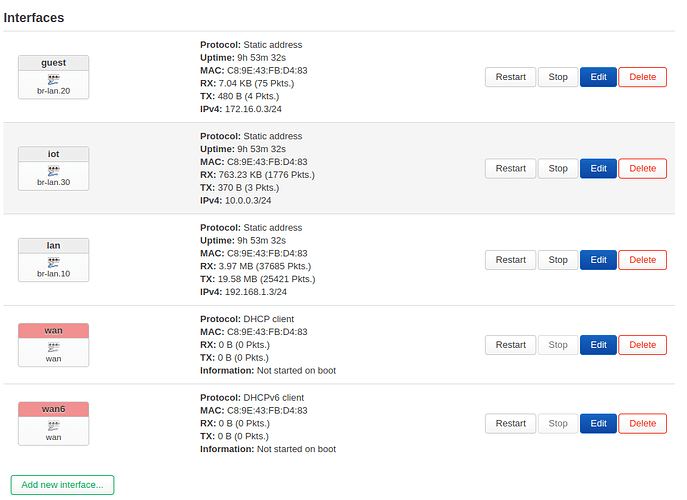
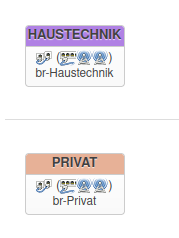
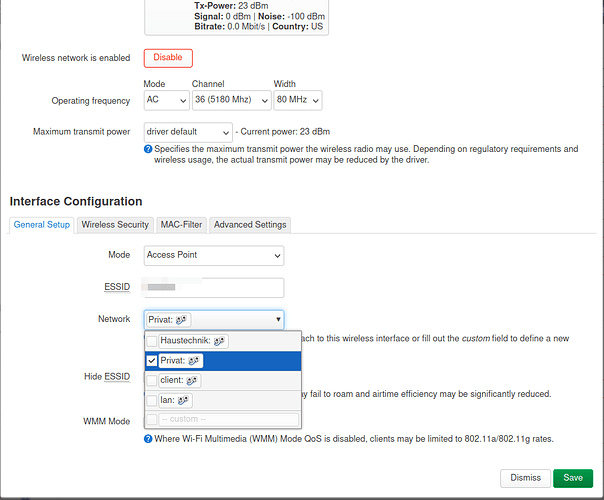
And the configuration of one AP (only has one Ethernet port anyway; the bridges are required for attaching the WiFi interfaces). Each AP has a static IP on VLAN1 and DHCP clients on VLAN1, VLAN200 and VLAN300 (so they all receive multiple IPs from different subnets). One WiFi interface is then attached to br-Private and the othter to br-Haustechnik.
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.20.60'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'Client'
option proto 'dhcp'
option device 'br-lan'
option hostname 'eap225-Mgmt'
config interface 'Private'
option proto 'dhcp'
option hostname 'eap225Private'
option device 'br-Private'
config interface 'Haustechnik'
option proto 'dhcp'
option hostname 'eap225Technik'
option device 'br-Haustechnik'
config device
option name 'br-Haustechnik'
option type 'bridge'
list ports 'eth0.200'
option macaddr 'xx:xx:xx:xx:xx:xx'
config device
option name 'br-Private'
option type 'bridge'
list ports 'eth0.300'
option macaddr 'xx:xx:xx:xx:xx:xx'
On the router, the remaining Ethernet ports can be used by regular devices and are configured as "Management". The AP cannot be used by non-VLAN-aware devices as it's tagged only.