I have DigitalOcean account
Then you can try to setup a tunnel to your VPS in Digital Ocean and use the VPS public IP for your services which will be forwarded to the RPi. You won't need port forward on RPi anymore like this.
I will try it but I am a bit worried about the message I get Insufficient permissions to read UCI configuration
Where did that come from?
The powerline devices should act as a long ethernet cable, and change nothing.
I think I have a bug in my installation. Port forwarding works on my old Mikrotik router with default settings, same for Archer C6 V2. The only time it doesn't work is when I use Raspberry Pi4 as my router.
So, if your old ‘Tik router works and your c6 does not, check the IP address reported on the wan of each device. If you have Rfc1918 addresses in both cases, your upstream device (modem/modem-router combo) is likely the issue. You may need to change settings on the upstream unit (port forwarding or dmz, or dhcp reservation) to make the forwarding work properly.
Mikrotik and Archer works, all 3 - Mikrotik, Archer, Raspberry report the same RFC1918 address.
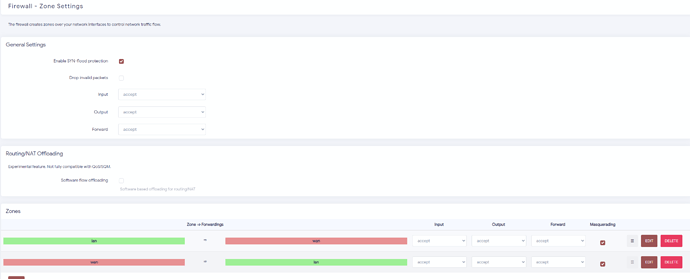
This my Firewall setup now
That's my portforwarding setup
Also my bridge settings
Why do you have eth0 and eth1 bridged?
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
Just from those screenshots, I can see that you have a bunch of things messed up. You may find it faster to reset to defaults and then setup the port forwards from there.
Here it is. Should only eth0 be bridged? That's my LAN connection
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd6b:7561:0c9a::/48'
config device
option name 'br-lan'
option type 'bridge'
option acceptlocal '1'
option bridge_empty '1'
list ports 'eth0'
config interface 'lan'
option device 'eth0'
option proto 'static'
option ipaddr '192.168.0.2'
option netmask '255.255.255.0'
option type 'bridge'
config interface 'wan'
option proto 'dhcp'
option device 'eth1'
option peerdns '0'
list dns '192.168.0.172'
option hostname '*'
option type 'bridge'
option delegate '0'
config device
option name 'eth1'
option macaddr 'B8:69:F4:B0:69:DE'
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option input 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
option reload '1'
config forwarding
option src 'wan'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'wan'
config redirect
option target 'DNAT'
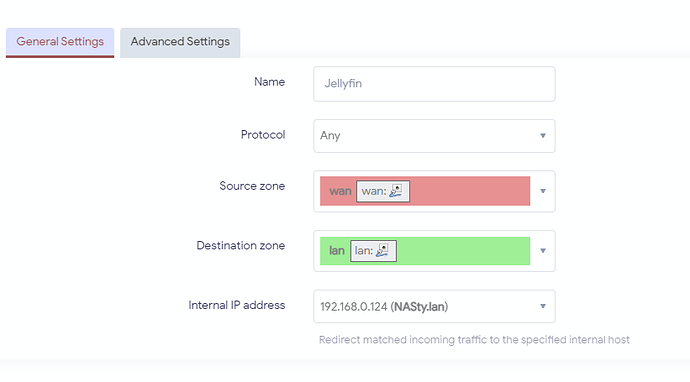
option name 'Jellyfin'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.0.124'
list proto 'all'
config rule
option name 'Jellyfin'
option src 'wan'
option dest 'lan'
option target 'ACCEPT'
list proto 'all'
config redirect
option target 'DNAT'
option name 'Plex'
option src 'wan'
option src_dport '32400'
option dest 'lan'
option dest_ip '192.168.0.124'
option dest_port '32400'
Your config is pretty messed up. It will be easier to reset to defaults and start over.
EDIT: just to be clear why I'm saying that you should reset: the WAN and LAN appear to be bridged together in some strange way, but the bridge is not properly constructed; your firewall isn't doing anything useful since WAN can forward to the LAN and WAN even has the ability to access the router itself, masquerading is enabled on the LAN, and there are probably a dozen other errors that I haven't spotted yet. Currently your router is not even remotely configured properly, and the best option is to simply reset it and start fresh. In all likelihood, you should only be making a few minimal changes to the default configuration... what you've got is a ton of changes that are probably the result of a lot of tinkering and the router just simply isn't going to work properly.
Ok, point taken. So what should be the correct setup? Can you please post some tips or config examplea? My PI has 2 network devices, 1 for LAN and 1 for WAN
The default configuration is usually a good starting place. If you need/want to change the LAN subnet, feel free to do that.
Then you'll add simple rules in the firewall: redirect from WAN on the port(s) of interest in the external port field > LAN with a specified internal IP and internal port (often the same as the external port).
You may also want to add a DHCP reservation if the target host is using DHCP (so that it always gets the same IP; if you have set that host to static IP manually on the device itself, you don't need to worry about the DHCP reservation).
Typically that's it.
Thanks! So on the firewall settings do I keep it as is? Default was WAN forward Reject
Yes. Don't touch the standard firewall configuration except to add the redirect.
I have built as a last resort in Digital Ocean OpenVPN server. I have a tunnel established between my Pi with Jellyfin installed and the OpenVPN Digital Ocean server when I do curl ifconfig.me I get the OpenVPN server. So now I have to figure out how to setup portforwarding.
Wait, what?? How did we go from resetting your severely misconfigured router to setting up an OpenVPN server on a VPS?