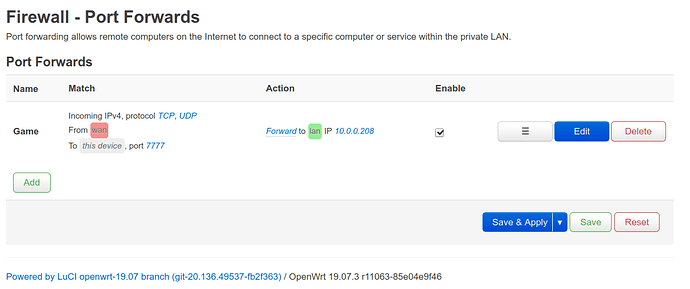
I spent all day figuring out why port forwarding doesn't work, and I can't find what's wrong. I want to open up port 7777, but all outside clients including those port checking websites say the port is closed.
Device: Netgear R7800
OS Version: OpenWrt 19.07.3 r11063-85e04e9f46
/etc/config/network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdad:af44:bdab::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth1.1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.0.1'
list dns '10.0.0.68'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
/etc/config/firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option src 'wan'
option name 'Game'
option target 'DNAT'
option dest_ip '10.0.0.208'
option dest 'lan'
option src_dport '7777'
list proto 'tcp'
list proto 'udp'
/etc/firewall.user:
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
# Keep network on pi-hole
iptables -t nat -I PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 10.0.0.68:53
iptables -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.0.0.68:53
# Punch DNS hole for pi-hole
iptables -t nat -I PREROUTING -i br-lan -p tcp -s 10.0.0.68 --dport 53 -j ACCEPT
iptables -t nat -I PREROUTING -i br-lan -p udp -s 10.0.0.68 --dport 53 -j ACCEPT
I've used tcpdump and do see traffic coming to port 7777 on the router. The firewall on the computer running the game on port 7777 is disabled. Here's the output of restarting /etc/init.d/firewall restart:
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv6 filter table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Redirect 'Game'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 nat table
* Redirect 'Game'
* Zone 'lan'
* Zone 'wan'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 filter table
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ICMPv6-Forward'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Forward 'lan' -> 'wan'
* Zone 'lan'
* Zone 'wan'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.user'